#FactCheck -AI-Generated Video Falsely Shows PM Modi Praising Christianity
Executive Summary:
A video of Prime Minister Narendra Modi is going viral across multiple social media platforms. In the clip, PM Modi is purportedly heard praising Christianity and stating that only Jesus Christ can lead people to heaven.Several users are sharing and commenting on the video, believing it to be genuine. The CyberPeace researched the viral claim and found it to be false. The circulating video has been created using artificial intelligence (AI).
Claim:
On January 29, 2026, a Facebook user named ‘Khaju Damor’ posted the viral video of PM Modi. The post gained traction, with many users sharing and commenting on it as if it were authentic. (Links and archived versions provided)

Fact Check:
As part of our research , we first closely examined the viral video. Upon careful observation, several inconsistencies were noticed. The Prime Minister’s facial expressions and hand movements appeared unnatural. The lip-sync and overall visual presentation also raised suspicions about the clip being digitally manipulated. To verify this further, we analyzed the video using the AI detection tool Hive Moderation. The tool’s analysis indicated a 99% probability that the video was AI-generated.
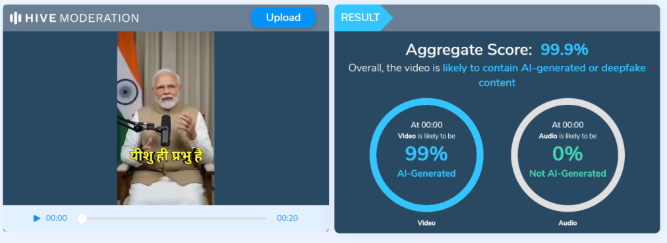
To independently confirm the findings, we also ran the clip through another detection platform, Undetectable.ai. Its analysis likewise indicated a very high likelihood that the video was created using artificial intelligence.

Conclusion:
Our research confirms that the viral video of Prime Minister Narendra Modi praising Christianity and making the alleged statement about heaven is fake. The clip has been generated using AI tools and does not depict a real statement made by the Prime Minister.
Related Blogs

Executive Summary:
Following India’s heavy defeat to South Africa in the T20 World Cup 2026, the team has been facing intense trolling on social media. Amid this backdrop, a video of Indian cricket team head coach Gautam Gambhir has gone viral. In the clip, Gambhir can be heard saying,“Even people who have nothing to do with cricket have made comments. An IPL owner also wrote about split coaching. It’s surprising. People must stay in their own domain. If we don’t interfere in someone else’s domain, they have no right to interfere in ours.”The video is being shared with the claim that Gambhir made these remarks recently in response to trolling after India’s loss to South Africa in the T20 World Cup 2026. However, research by the CyberPeace found the claim to be misleading. The viral video is not related to the T20 World Cup 2026. It is from December 2025 and pertains to India’s Test series defeat against South Africa. An old video is being circulated with a misleading context.
Claim
An Instagram user, ‘rns_news200’, shared the viral video on February 23, 2026, claiming that after the loss to South Africa, head coach Gautam Gambhir issued a stern warning to Indian fans. The caption stated that Suryakumar Yadav was heavily trolled on social media after the match, and Gambhir responded strongly, saying players should not be unfairly targeted and the team deserves support, especially during difficult times.

Fact Check
To verify the claim, we conducted a keyword search on Google. We found the same video on the official X (formerly Twitter) account of sports journalist Vikrant Gupta. The video was posted on December 7, 2025. According to the caption, Gambhir was expressing dissatisfaction following India’s performance.
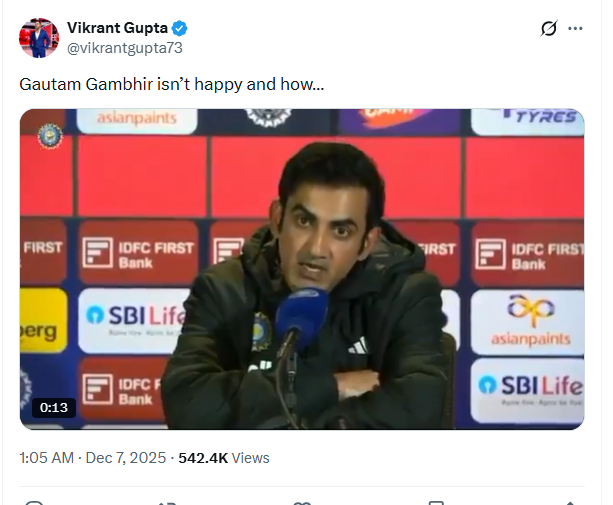
We also found the longer version of the video on the official website of the Board of Control for Cricket in India (BCCI), where it was published on December 6, 2025. In the full video, Gambhir is clearly seen speaking about India’s defeat to South Africa in a Test match. The specific segment that went viral appears around the 1 minute 58 second mark.
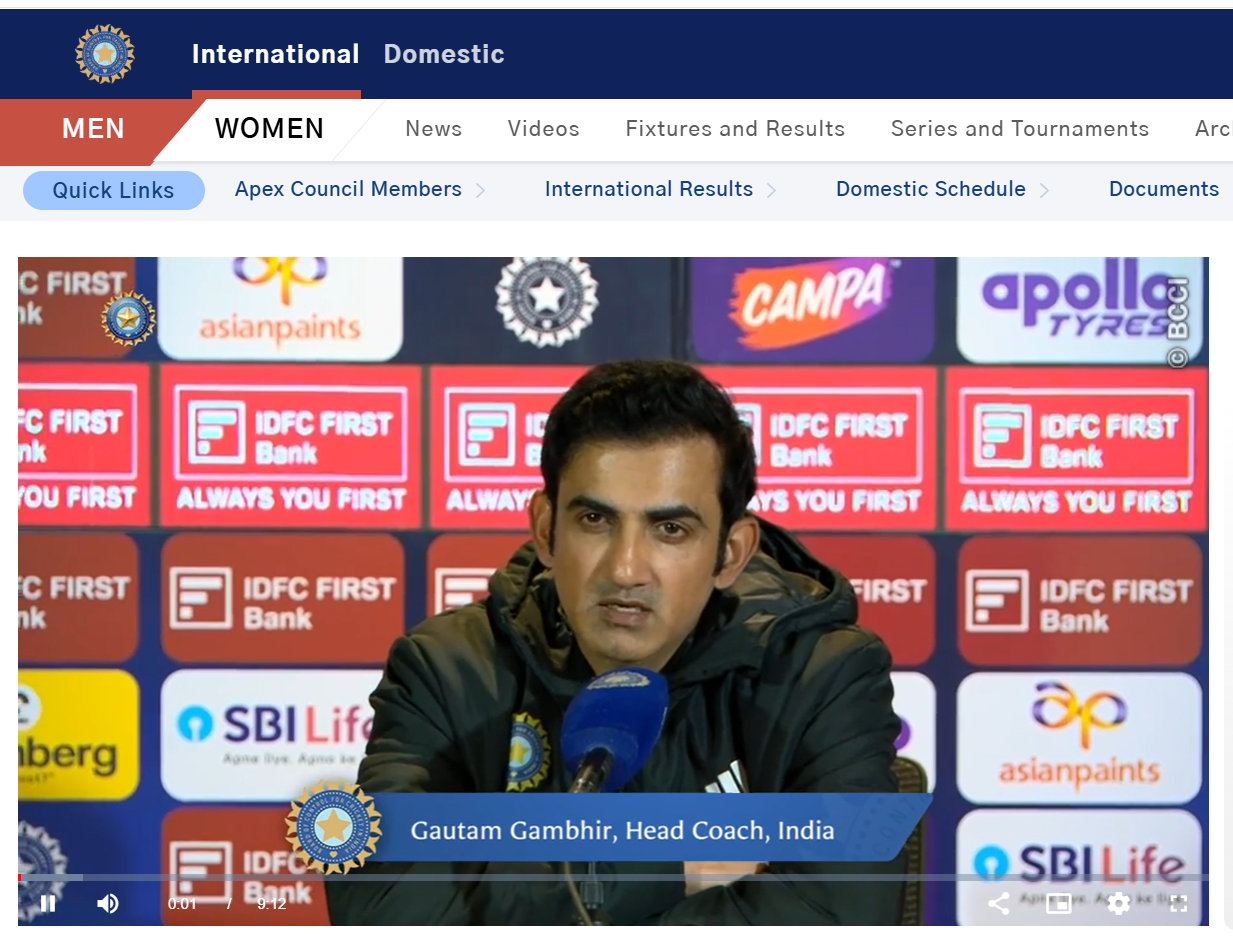
Conclusion
Our research found that the viral claim about Gautam Gambhir’s video being linked to trolling after the T20 World Cup 2026 is misleading. The clip is from December 2025 and relates to India’s Test series defeat against South Africa — not the T20 World Cup 2026.An old video is being reshared with a false and misleading context.

Introduction
The Government of India has initiated a cybercrime crackdown that has resulted in the blocking of 781,000 SIM cards and 208,469 IMEI (International Mobile Equipment Identity) numbers that are associated with digital fraud as of February 2025. This data was released as a written response by the Union Minister of State for Home Affairs, Bandi Sanjay Kumar, with respect to a query presented in the Lok Sabha. A significant jump from the 669,000 SIM cards blocked in the past year, efforts aimed at combating digital fraud are in full swing, considering the increasing cases. The Indian Cyber Crime Coordination Centre (I4C) is proactively blocking other platform accounts found suspicious, such as WhatsApp Accounts (83,668) and Skype IDs (3,962) on its part, aiding in eliminating identified threat actors.
Increasing Digital Fraud And The Current Combative Measures
According to the data tabled by the Ministry of Finance in the Rajya Sabha, the first 10 months of the Financial year 2024-2025 have recorded around 2.4 million incidents covering an amount of Rs. 4,245 crore involving cases of digital Financial Fraud cases. Apart from the evident financial loss, such incidents also take an emotional toll as people are targeted regardless of their background and age, leaving everyone equally vulnerable. To address this growing problem, various government departments have dedicated measures to combat and reduce such incidents. Some of the notable initiatives/steps are as follows:
- The Citizen Financial Cyber Fraud Reporting and Management System- This includes reporting Cybercrimes through the nationwide toll-free (1930) number and registration on the National Cyber Crime Reporting Portal. On being a victim of digital fraud, one can call the toll-free number, describing details of the incident, which would further help in the investigation. After reporting the incident, the complainant receives a generated login ID/acknowledgement number that they can use for further reference.
- International Incoming Spoofed Calls Prevention System- This is a mechanism developed to counter fraudulent calls that appear to originate from within India but are actually made from international locations. This system prevents the misuse of the Calling Line Identity (CLI), which is manipulated to deceive recipients in order to carry out financial crimes like digital arrests, among other things. Coordinating with the Department of Telecommunication (DoT), private telecommunication service providers (TSPs) are being encouraged to check with their ILD (International Long-Distance) network as a measure. Airtel has recently started categorising such numbers as International numbers on their part.
- Chakshu Facility at Sanchar Saathi platform- A citizen-centric initiative, created by the Department of Telecommunications, to empower mobile subscribers. It focuses on reporting unsolicited commercial communication (spam messages) and reporting suspected fraudulent communication. (https://sancharsaathi.gov.in/).
- Aadhaar-based verification of SIM cards- A directive issued by the Prime Minister's Office to the Department of Telecommunications mandates an Aadhaar-based biometric verification for the issuance of new SIM cards. This has been done so in an effort to prevent fraud and cybercrime through mobile connections obtained using fake documents. Legal action against non-compliant retailers in the form of FIRs is also being taken.
On the part of the public, awareness of the following steps could encourage them on how to deal with such situations:
- Awareness regarding types of crimes and the tell-tale signs of the modus operandi of a criminal: A general awareness and a cautionary approach to how such crimes take place could help better prepare and respond to such malicious scams. Some important signs on the part of the offender include pressuring the victim into immediate action, insistence on video calls, and the threat of arrest in case of non-compliance. It is also important to note that no official authority, in any legal capacity, allows for enabling a digital/online arrest.
- Knowing the support channels: Awareness regarding reporting mechanisms and cyber safety hygiene tips can help in building cyber resilience amongst netizens.
Conclusion
As cybercrooks continue to find new ways of duping people of their hard-earned money, both government and netizens must make efforts to combat such crimes and increase awareness on both ends (systematic and public). Increasing developments in AI, deepfakes, and other technology often render the public inept at assessing the veracity of the source, making them susceptible to such crime. A cautionary yet proactive approach is need of the hour.
References
- https://mobileidworld.com/india-blocks-781000-sim-cards-in-major-cybercrime-crackdown/
- https://www.storyboard18.com/how-it-works/over-83k-whatsapp-accounts-used-for-digital-arrest-blocked-home-ministry-60292.htm
- https://www.business-standard.com/finance/news/digital-financial-frauds-touch-rs-4-245-crore-in-the-apr-jan-period-of-fy25-125032001214_1.html
- https://www.business-standard.com/india-news/govt-blocked-781k-sims-3k-skype-ids-83k-whatsapp-accounts-till-feb-125032500965_1.html
- https://pib.gov.in/PressReleasePage.aspx?PRID=2042130
- https://mobileidworld.com/india-mandates-aadhaar-biometric-verification-for-new-sim-cards-to-combat-fraud/
- https://pib.gov.in/PressReleaseIframePage.aspx?PRID=2067113
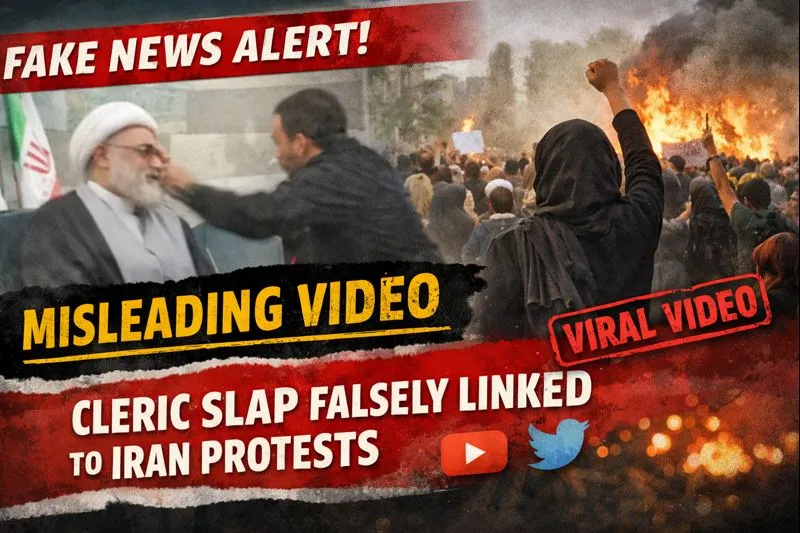
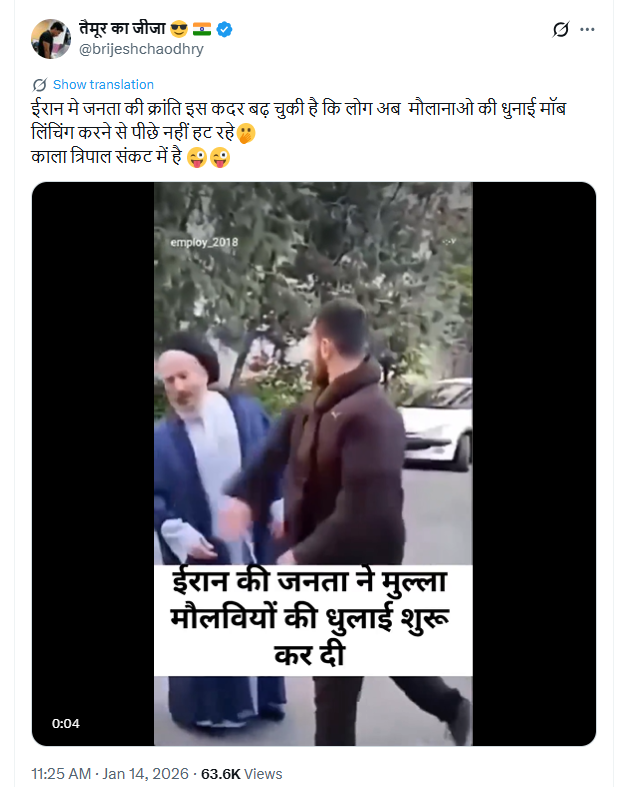
Amid reports that the death toll in Iran’s ongoing protests has risen to 2,571, a video has been widely circulated on social media showing a man slapping a person dressed in clerical attire after an argument. Users sharing the clip claim that public anger in Iran has escalated to the point where people are now physically attacking religious clerics. However, research by the Cyber Peace Foundation has found this claim to be misleading. The research established that the video is not recent and has no connection to the current protests in Iran. In fact, the clip dates back to 2021 and was entirely scripted.
Claim
On January 14, 2026, users on X (formerly Twitter) shared the viral video with captions suggesting that Iranian citizens are openly assaulting clerics amid the ongoing unrest. One such post stated that the situation in Iran had deteriorated so badly that people were now beating religious leaders.
The link, archived version, and screenshot of the post are available below:
Factcheck:
To verify the authenticity of the claim, the Cyber Peace Foundation extracted keyframes from the viral video and conducted a Google reverse image search. This led investigators to a report published on April 19, 2021, on the Persian-language website of Deutsche Welle (DW). The visuals matched the viral clip exactly, confirming that the footage is nearly five years old, not recent. Here is the link to the original video, along with a screenshot:
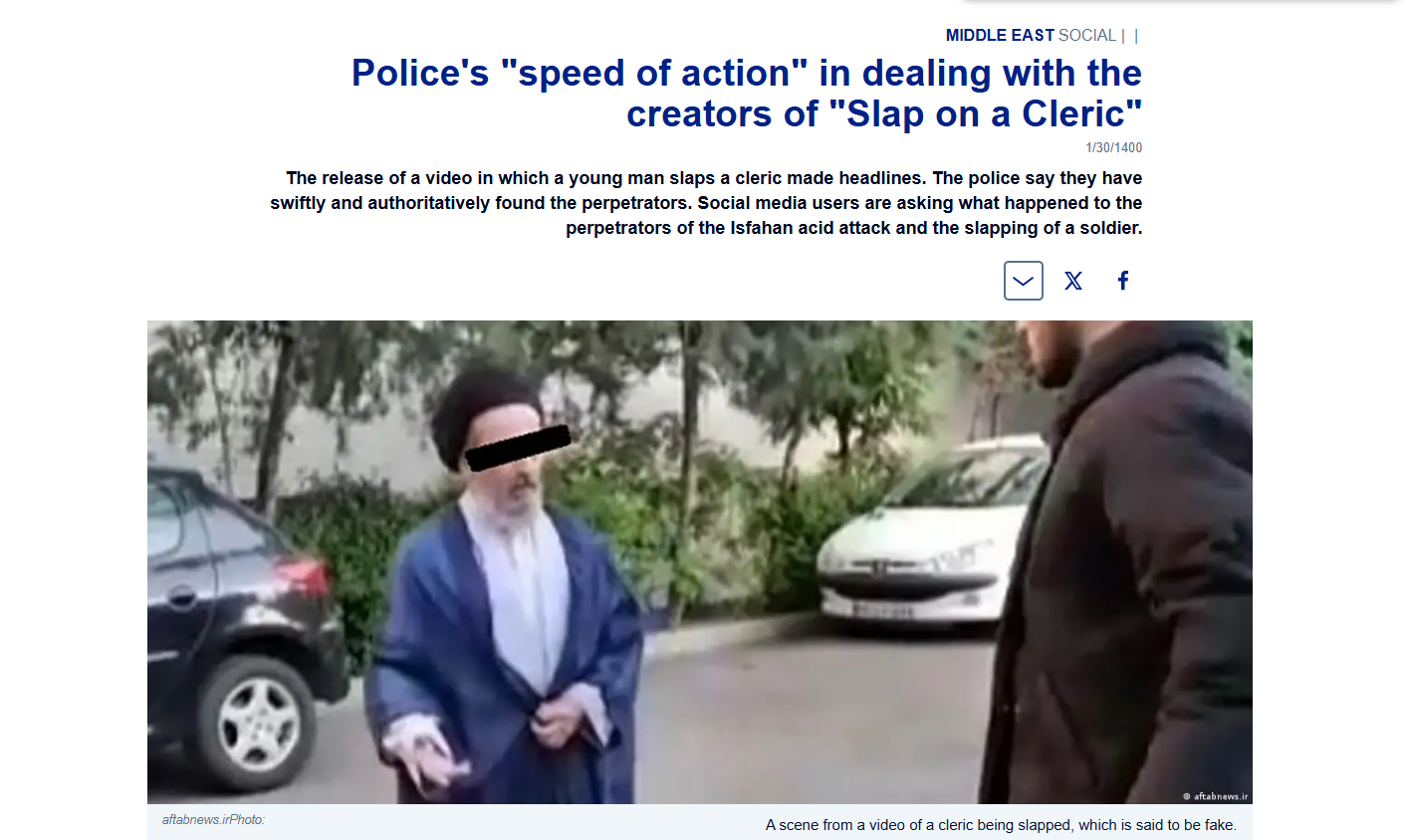
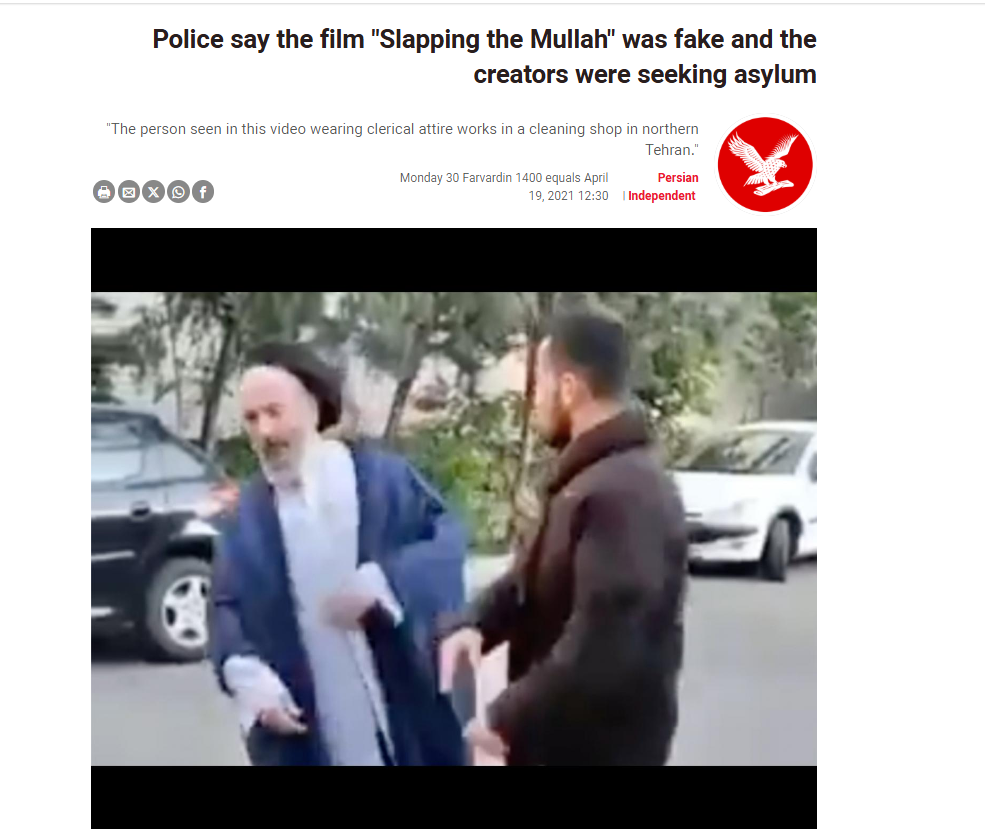
Further examination of reports by Fars News Agency revealed that Tehran police had conducted a detailed probe into the video at the time and declared it fake and pre-scripted. According to Tehran Police Chief Hossein Rahimi, the individual seen wearing religious attire was not a cleric. Here is the link to the original video, along with a screenshot: He was actually employed at a carpet cleaning shop in Tehran, while the man seen slapping him was his own son.
Police stated that the video was deliberately staged and circulated to provoke public sentiment and create unrest by falsely linking it to religious tensions. Both the father and son were arrested, and images of them in police custody were published in contemporaneous reports. Additional confirmation was found on the Independent Persian website, which had also reported on the incident on April 19, 2021, reiterating that the video was fabricated and unrelated to any protest movement. Here is the link to the original video, along with a screenshot:
Conclusion
The claim that the viral video shows an Iranian protester slapping a cleric during the current wave of protests is false. The video is from 2021, was scripted, and has no link to the ongoing demonstrations in Iran. It is being reshared with a misleading narrative to spread disinformation and inflame public sentiment.c


