#FactCheck - AI-Generated Video Falsely Claims Salman Khan Is Joining AIMIM
A video of Bollywood actor Salman Khan is being widely circulated on social media, in which he can allegedly be heard saying that he will soon join Asaduddin Owaisi’s party, the All India Majlis-e-Ittehadul Muslimeen (AIMIM). Along with the video, a purported image of Salman Khan with Asaduddin Owaisi is also being shared. Social media users are claiming that Salman Khan is set to join the AIMIM party.
CyberPeace research found the viral claim to be false. Our research revealed that Salman Khan has not made any such statement, and that both the viral video and the accompanying image are AI-generated.
Claim
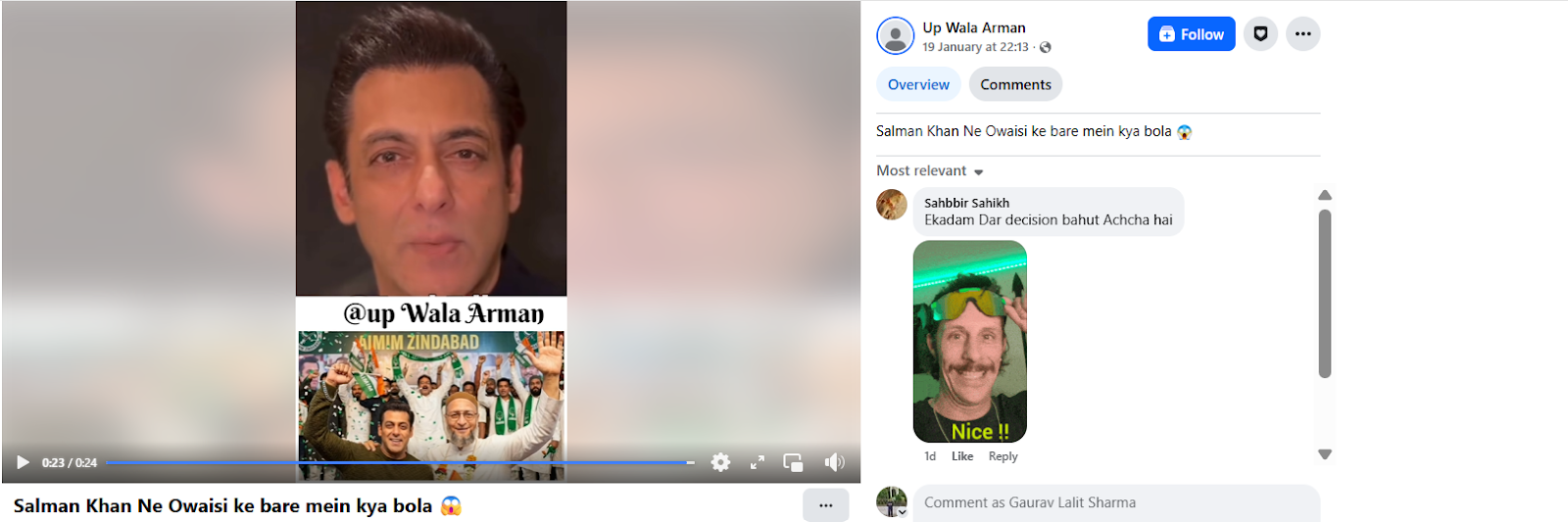
Social media users claim that Salman Khan has announced his decision to join AIMIM.On 19 January 2026, a Facebook user shared the viral video with the caption, “What did Salman say about Owaisi?” In the video, Salman Khan can allegedly be heard saying that he is going to join Owaisi’s party. (The link to the post, its archived version, and screenshots are available.)
Fact Check:
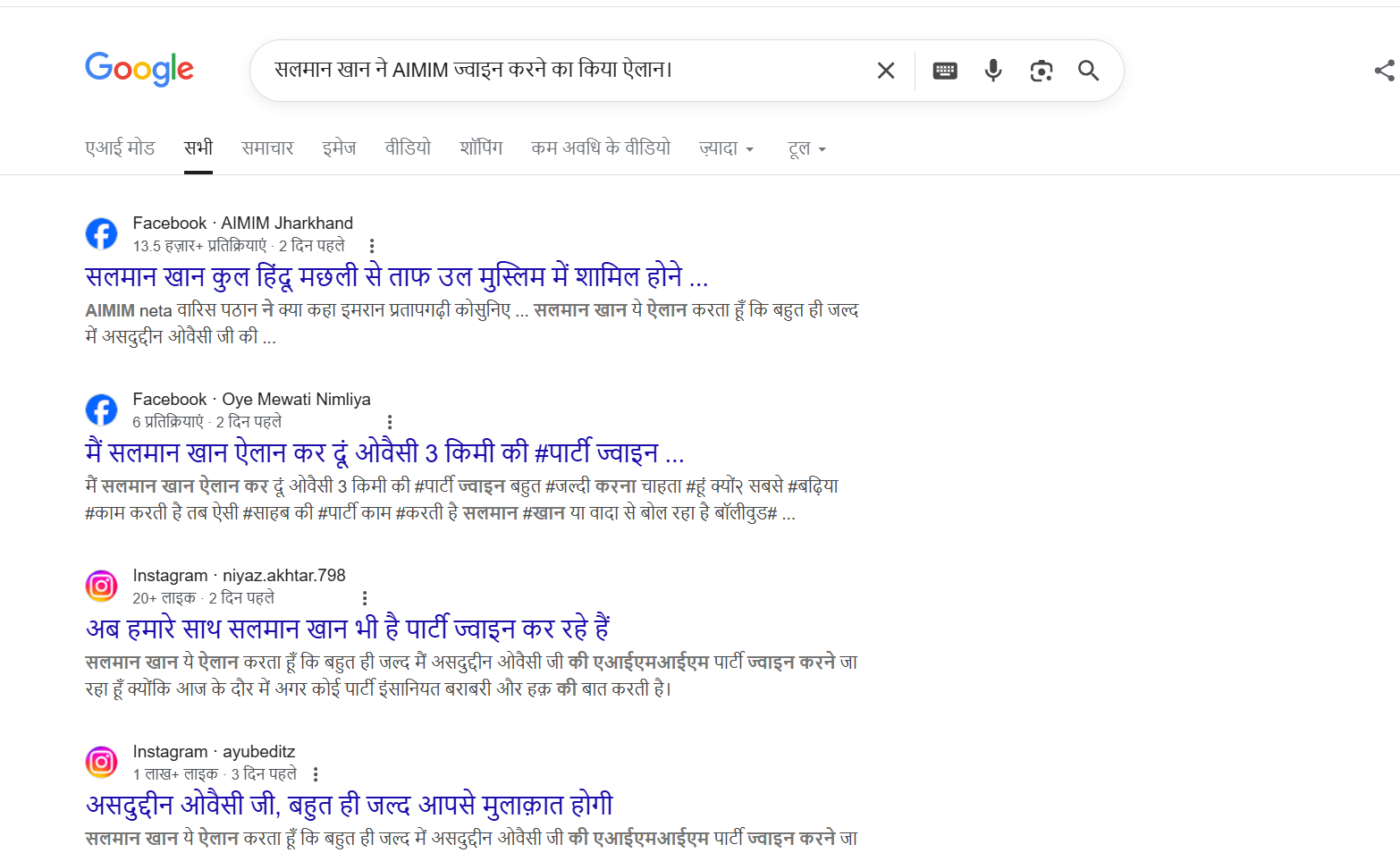
To verify the claim, we first searched Google using relevant keywords. However, no credible or reliable media reports were found supporting the claim that Salman Khan is joining AIMIM.
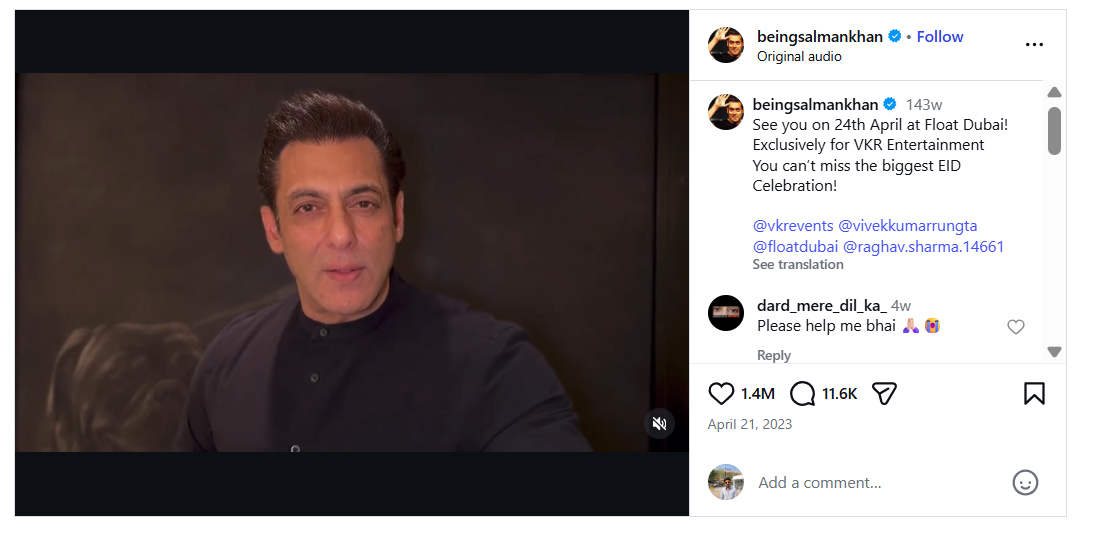
In the next step of verification, we extracted key frames from the viral video and conducted a reverse image search using Google Lens. This led us to a video posted on Salman Khan’s official Instagram account on 21 April 2023. In the original video, Salman Khan is seen talking about an event scheduled to take place in Dubai. A careful review of the full video confirmed that no statement related to AIMIM or Asaduddin Owaisi is made.
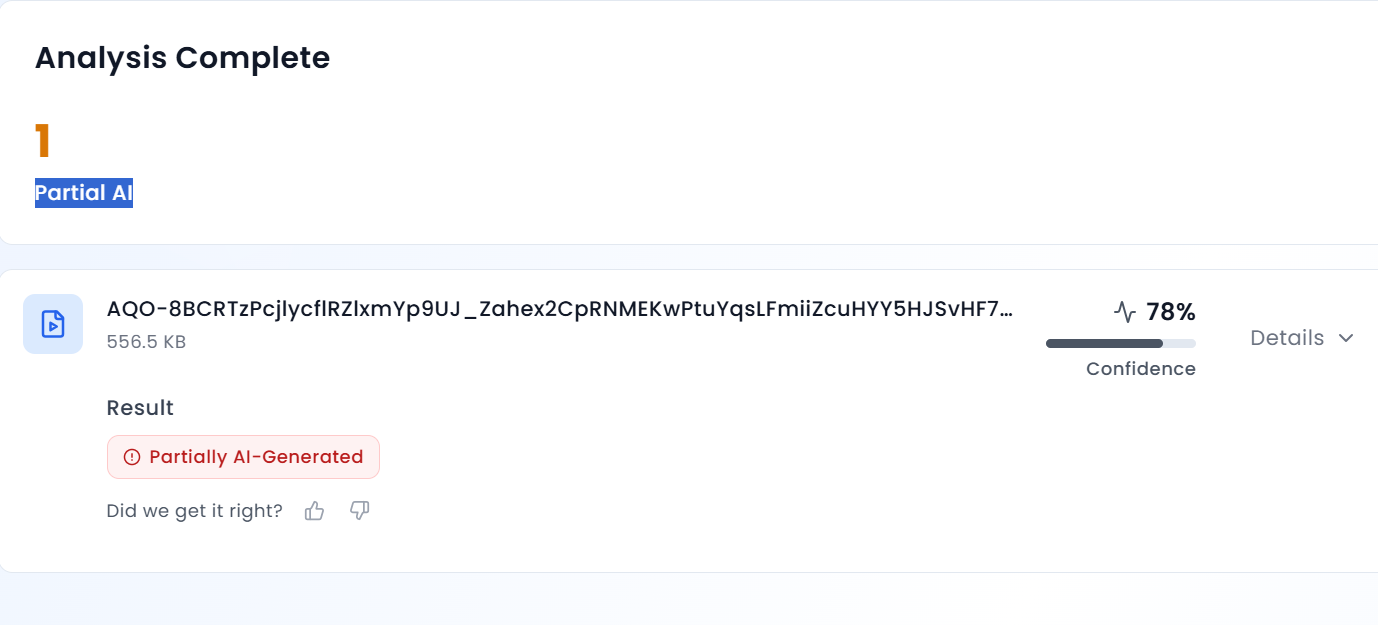
Further analysis of the viral clip revealed that Salman Khan’s voice sounds unnatural and robotic. To verify this, we scanned the video using AURGIN AI, an AI-generated content detection tool. According to the tool’s analysis, the viral video was generated using artificial intelligence.
Conclusion
Salman Khan has not announced that he is joining the AIMIM party. The viral video and the image circulating on social media are AI-generated and manipulated.
Related Blogs
%20(1).webp)
Introduction
The Central Electricity Authority (CEA) has released the Draft Central Electricity Authority (Cyber Security in Power Sector) Regulations, 2024, inviting ‘comments’ from stakeholders, including the general public, which are to be submitted by 10 September 2024. The new regulation is intended to make India’s power sector more cyber-resilient and responsive to counter emerging cyber threats and safeguard the nation's power infrastructure.
Key Highlights of the CEA’s New (Cyber Security in Power Sector) Regulations, 2024
- Central Electricity Authority has framed the ‘Cyber Security in Power Sector Regulations, 2024’ in the exercise of the powers conferred by sub-section (1) of 177 of the Electricity Act, 2003 in order to make regulations for measures relating to Cyber Security in the power sector.
- The scope of the regulation entails that these regulations will be applicable to all Responsible Entities, Regional Power Committees, Appropriate Commission, Appropriate Government and Associated Power Sector Government Organizations, and Training Institutes recognized by the Authority, Authority and Vendors.
- One key aspect of the proposed regulation is the establishment of a dedicated Computer Security Incident Response Team (CSIRT) for the power sector. This team will coordinate a unified cyber defense strategy throughout the sector, establishing security frameworks, and serving as the main agency for handling incident response and recovery. The CSIRT will also be responsible for creating/developing Standard Operating Procedures (SOPs), security policies, and best practices for incident response activities in consultation with CERT-In and NCIIPC. The detailed roles and responsibilities of CSIRT are outlined under Chapter 2 of the said regulations.
- All responsible entities in the power sector as mentioned under the scope of the regulation, are mandated to appoint a Chief Information Security Officer (CISO) and an alternate CISO, who need to be Indian nationals and who are senior management employees. The regulations specify that these officers must directly report to the CEO/Head of the Responsible Entity. Thus emphasizing the critical nature of CISO’s roles in safeguarding the nation’s power grid sector assets.
- All Responsible Entities shall establish an Information Security Division (ISD) dedicated to ensuring Cyber Security, headed by the CISO and remain operational around the clock. The schedule under regulation entails that the minimum workforce required for setting up an ISD is 04 (Four) officers including CISO and 04 officers/officials for shift operations. Sufficient workforce and infrastructure support shall be ensured for ISD. The detailed functions and responsibilities of ISD are outlined under Chapter 5 regulation 10. Furthermore, the ISD shall be manned by sufficient numbers of officers, having valid certificates of successful completion of domain-specific Cyber Security courses.
- The regulation obliged the entities to have a defined, documented and maintained Cyber Security Policy which is approved by the Board or Head of the entity. The regulation also obliged the entities to have a Cyber Crisis Management Plan (CCMP) approved by the higher management.
- As regards upskilling and empowerment the regulation advocates for organising or conducting periodic Cyber Security awareness programs and Cyber Security exercises including mock drills and tabletop exercises.
CyberPeace Policy Outlook
CyberPeace Policy & Advocacy Vertical has submitted its detailed recommendations on the proposed ‘Cyber Security in Power Sector Regulations, 2024’ to the Central Electricity Authority, Government of India. We have advised on various aspects within the regulation including harmonisation of these regulations with other rules as issued by CERT-In and NCIIPC, at present. As this needs to be clarified which set of guidelines will supersede in case of any discrepancy that may arise. Additionally, we advised on incorporating or making modifications to specific provisions under the regulation for a more robust framework. We have also emphasized legal mandates and penalties for non-compliance with cybersecurity, so as to make sure that these regulations do not only act as guiding principles but also provide stringent measures in case of non-compliance.
References:
In the digital era of the present day, a nation’s strength no longer gets measured only by the number of missiles or aircraft it has in its inventory. Rather, it also calls for defending the digital borders. Major infrastructures like power grids and dams are increasingly being targeted by cyberattacks in the global security environment that modern militaries operate in. When communication channels are vulnerable to an information breach, cybersecurity becomes a crucial component of national defence.
Why is cybersecurity a crucial national security concern in the modern era?
The technologies and procedures that shield digital devices, networks, and systems from unwanted access or attacks are referred to as cybersecurity. Cyberattacks are silent in the context of national security, in contrast to conventional warfare. They are swift and are also capable of causing a massive disruption without even a single case of physical infiltration. However, hostile states, terrorist organisations, or criminal networks may be able to steal any classified information or disrupt military infrastructure due to a cybersecurity breach in a military network.
To fully comprehend the significance of cybersecurity, let's examine the various approaches, such as:
- Protecting critical infrastructures- Today's nations rely heavily on digital networks to run vital services like banking, transportation, electricity, water supply, and healthcare. Therefore, a cyberattack on these systems could cause problems across the country and interfere with our daily activities. Therefore, it is also seen that the military forces of a nation closely work in synergy with other government agencies and private organizations to create a strong ecosystem of security in this sector.
- Safeguarding military operations in the present age- The armed forces heavily rely on digital tools for communication, mission planning, surveillance, and coordination. In case the cyber intruders get access to those systems, then a lot of major operational hurdles can come up in the form of breach of mission details, disruption of channels, and compromise of the confidentiality of military operations. These are certain conditions that make cybersecurity an important aspect for protecting the physical bases and the security architectures.
- Preventing cyber warfare- With the evolution of the geopolitical landscape, state and non-state actors are now resorting to cyberattacks to gather intelligence, disrupt security networks, and influence political outcomes. Still, strong cybersecurity can help nations to ensure, detect, defend, and respond to threats in an effective manner.
- Securing government databases- The government databases are known for storing sensitive information about the citizens, military assets, diplomatic data, and vital information related to major national infrastructures. If these get compromised, then it can weaken the strategic position of the nation and put the national security of the nation at a grave risk. Therefore, it becomes necessary to protect government data as a priority.
How can countries improve their cybersecurity defences?
Countries all over the world are developing their cyber capabilities using a variety of tactics to protect against the increasing number of cyber threats. A few of these can be interpreted as;
- Creating cyber defence units- The majority of contemporary armed forces have created specialised cyber domains devoted to threat identification. Their responsibilities have been centred on keeping an eye on those dangers, stopping intrusions, and reacting quickly to cyberattacks.
- Public-Private Partnerships- To safeguard vital industries like energy grids, financial networks, and communication systems, the government collaborates with private businesses and technology suppliers. Additionally, these collaborations foster innovation to improve the overall defence against cyberattacks.
- Establishing international collaborations- Cyber threats do not respect our borders. As a result, which countries are increasing their share of intelligence, best practices, and defensive strategies with their allies? Groups like NATO have conducted a joint cyber defence exercise to prepare for dealing with a digital future.
However, these collaborations can help to develop a united front against cybercrime.
Core Pillars of the modern military cyber defence
The modern defence strategies have been built upon several key designated pillars that are designed to prevent, detect, and respond to cyber threats, which can be mentioned as;
- Cyberspace as an operational domain- Militaries have now begun to treat cyberspace like the land, air, sea, and space as domains where wars can both begin and also end. Developing some dedicated cyber units to conduct digital operations to defend networks and engage in a range of counter-cyber activities when required.
- Active and proactive defence- Instead of passively waiting for the attacks to happen, real-time monitoring tools are used for blocking the threats that arise. Proactive defence goes a step further by hunting for potential threats before they can reach the networks.
- • Protection of vital infrastructures- The armed forces collaborate closely with civilian organisations and agencies to secure vital infrastructures that are important to the country. Critical infrastructure is protected from cyberattacks by layered defence, which includes encryption, stringent access control, and ongoing monitoring.
- • Strengthening alliances- Countries can develop a strong and well-coordinated defence system by exchanging intelligence to carry out cooperative cyber operations.
- Fostering innovation for the development of a workforce- Cyber threats evolve at a rapid pace, which calls for the military to invest in advanced technologies like AI-driven systems, secure cloud technologies, besides ensure continuous training related to cybersecurity.
Conclusion
The modern militaries have adopted the method of protecting digital networks to defend their land and seas. Cybersecurity has become the new line of defence to protect government data and vital defence infrastructure from serious and unseen threats. The countries are building a secure, robust, and resilient digital future with the aid of solid alliances, cutting-edge technologies, knowledgeable workers, and a proactive defence strategy.
References
- https://www.ssh.com/academy/cyber-defense-strategy-dod-perspective#:~:text=Defence%20organizations%20are%20prime%20targets,SSH%20Key%20Management%20and%20Compliance
- https://www.fortinet.com/resources/cyberglossary/cyber-warfare#:~:text=Advanced%20endpoint%20security%20adds%20proactive,information%20by%20halting%20unauthorized%20transfers
- https://medium.com/@lynnfdsouza/the-impact-of-cyber-warfare-on-modern-military-strategies-c77cf6d1a788
- https://ccoe.dsci.in/blog/why-cybersecurity-is-critical-for-national-defense-protecting-countries-in-the-digital-age

Introduction
Romance scams have been rised in India. A staggering 66 percent of individuals in India have been ensnared by the siren songs of deceitful online dating schemes. These are not the attempts of yesteryears but rather a new breed of scams, seamlessly weaving the threads of traditional deceit with the sinew of cutting-edge technologies such as generative AI and deep fakes. A report by Tenable highlights the rise of romance scams in India, which now combine traditional tactics with advanced technologies like generative AI and deepfakes. Over 69% of Indians struggle to distinguish between artificial and authentic human voices. Scammers are using celebrity impersonations and platforms like Facebook to lure victims into a false sense of security.
The Romance Scam
A report by Tenable, the exposure management company, illuminates the disturbing evolution of these romance scams. It reveals a reality: AI-generated deep lakes have attained a level of sophistication where an astonishing 69 percent of Indians confess to struggling to discern between artificial and authentic human voices. This technological prowess has armed scammers with the tools to craft increasingly convincing personas, enabling them to perpetrate their nefarious acts with alarming success.
In 2023 alone, 43 percent of Indians reported falling victim to AI voice scams, with a staggering 83 percent of those targeted suffering financial loss. The scammers, like puppeteers, manipulate their digital marionettes with a deftness that is both awe-inspiring and horrifying. They have mastered the art of impersonating celebrities and fabricating personas that resonate with their targets, particularly preying on older demographics who may be more susceptible to their charms.
Social media platforms, which were once heralded as the town squares of the 21st century, have unwittingly become fertile grounds for these fraudulent activities. They lure victims into a false sense of security before the scammers orchestrate their deceitful symphonies. Chris Boyd, a staff research engineer at Tenable, issues a stern warning against the lure of private conversations, where the protective layers of security are peeled away, leaving individuals exposed to the machinations of these digital charlatans.
The Vulnerability of Individuals
The report highlights the vulnerability of certain individuals, especially those who are older, widowed, or experiencing memory loss. These individuals are systematically targeted by heartless criminals who exploit their longing for connection and companionship. The importance of scrutinising requests for money from newfound connections is underscored, as is the need for meticulous examination of photographs and videos for any signs of manipulation or deceit.
'Increasing awareness and maintaining vigilance are our strongest weapons against these heartless manipulations, 'safeguarding love seekers from the treacherous web of AI-enhanced deception.'
The landscape of love has been irrevocably altered by the prevalence of smartphones and the deep proliferation of mobile internet. Finding love has morphed into a digital odyssey, with more and more Indians turning to dating apps like Tinder, Bumble, and Hinge. Yet, as with all technological advancements, there lurks a shadowy underbelly. The rapid adoption of dating sites has provided potential scammers with a veritable goldmine of opportunity.
It is not uncommon these days to hear tales of individuals who have lost their life savings to a person they met on a dating site or who have been honey-trapped and extorted by scammers on such platforms. A new study, titled 'Modern Love' and published by McAfee ahead of Valentine's Day 2024, reveals that such scams are rampant in India, with 39 percent of users reporting that their conversations with a potential love interest online turned out to be with a scammer.
The study also found that 77 percent of Indians have encountered fake profiles and photos that appear AI-generated on dating websites or apps or on social media, while 26 percent later discovered that they were engaging with AI-generated bots rather than real people. 'The possibilities of AI are endless, and unfortunately, so are the perils,' says Steve Grobman, McAfee’s Chief Technology Officer.
Steps to Safeguard
Scammers have not limited their hunting grounds to dating sites alone. A staggering 91 percent of Indians surveyed for the study reported that they, or someone they know, have been contacted by a stranger through social media or text message and began to 'chat' with them regularly. Cybercriminals exploit the vulnerability of those seeking love, engaging in long and sophisticated attempts to defraud their victims.
McAfee offers some steps to protect oneself from online romance and AI scams:
- Scrutinise any direct messages you receive from a love interest via a dating app or social media.
- Be on the lookout for consistent, AI-generated messages which often lack substance or feel generic.
- Avoid clicking on any links in messages from someone you have not met in person.
- Perform a reverse image search of any profile pictures used by the person.
- Refrain from sending money or gifts to someone you haven’t met in person, even if they send you money first.
- Discuss your new love interest with your trusted friend. It can be easy to overlook red flags when you are hopeful and excited.
Conclusion
The path is fraught with illusions, and only by arming oneself with knowledge and scepticism can one hope to find true connection without falling prey to the mirage of deceit. As we navigate this treacherous terrain, let us remember that the most profound connections are often those that withstand the test of time and the scrutiny of truth.
References
- https://www.businesstoday.in/technology/news/story/valentine-day-alert-deepfakes-genai-amplifying-romance-scams-in-india-warn-researchers-417245-2024-02-13
- https://www.indiatimes.com/amp/news/india/valentines-day-around-40-per-cent-indians-have-been-scammed-while-looking-for-love-online-627324.html
- https://zeenews.india.com/technology/valentine-day-deepfakes-in-romance-scams-generative-ai-in-scams-romance-scams-in-india-online-dating-scams-in-india-ai-voice-scams-in-india-cyber-security-in-india-2720589.html
- https://www.mcafee.com/en-us/consumer-corporate/newsroom/press-releases/2023/20230209.html


