#FactCheck - AI-Generated Image of Abhishek Bachchan and Aishwarya Rai Falsely Linked to Kedarnath Visit
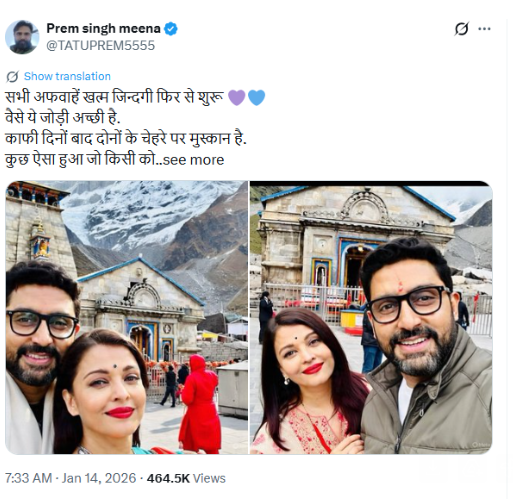
A photo featuring Bollywood actor Abhishek Bachchan and actress Aishwarya Rai is being widely shared on social media. In the image, the Kedarnath Temple is clearly visible in the background. Users are claiming that the couple recently visited the Kedarnath shrine for darshan.
Cyber Peace Foundation’s research found the viral claim to be false. Our research revealed that the image of Abhishek Bachchan and Aishwarya Rai is not real, but AI-generated, and is being misleadingly shared as a genuine photograph.
Claim
On January 14, 2026, a user on X (formerly Twitter) shared the viral image with a caption suggesting that all rumours had ended and that the couple had restarted their life together. The post further claimed that both actors were seen smiling after a long time, implying that the image was taken during their visit to Kedarnath Temple.
The post has since been widely circulated on social media platforms
Fact Check:
To verify the claim, we first conducted a keyword search on Google related to Abhishek Bachchan, Aishwarya Rai, and a Kedarnath visit. However, we did not find any credible media reports confirming such a visit.
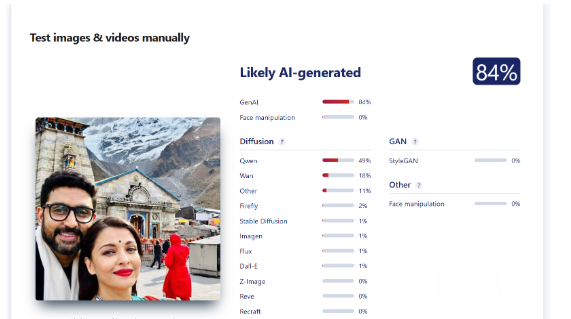
On closely examining the viral image, several visual inconsistencies raised suspicion about it being artificially generated. To confirm this, we scanned the image using the AI detection tool Sightengine. According to the tool’s analysis, the image was found to be 84 percent AI-generated.
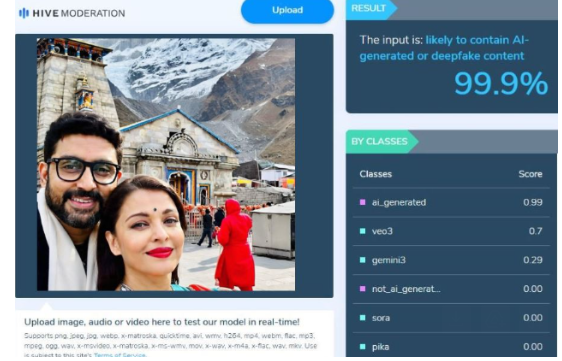
Additionally, we scanned the same image using another AI detection tool, HIVE Moderation. The results showed an even stronger indication, classifying the image as 99 percent AI-generated.
Conclusion
Our research confirms that the viral image showing Abhishek Bachchan and Aishwarya Rai at Kedarnath Temple is not authentic. The picture is AI-generated and is being falsely shared on social media to mislead users.
Related Blogs
.webp)
Introduction
In today's digital economy, data is not only a business asset but also the fuel for innovation, decision-making, and consumer trust. However, the digitisation of services has made personal or sensitive data a top target for cybercriminals. The stakes are high: a data breach can cost millions of fines, cause damage to reputation and devastate the confidence of consumers. Therefore, regulatory compliance and data protection have become a strategic imperative.
From the General Data Protection Regulation (GDPR) in the EU to the Digital Personal Data Protection (DPDP) Act of India, various sector-specific regulations like HIPAA for healthcare in the US, companies are now subject to a web of data protection and compliance laws. The challenge is to balance compliance efforts with strong security, a balance that demands both policy restraint and technical resilience. This blog examines pivotal pillars, shifting trends and actionable best practices for dominating data protection and compliance in 2025 and beyond.
Why Data Protection and Compliance Matter More Than Ever
Data protection isn't just about keeping fines at bay, it's about preserving the relationship with customers, partners and regulators. A 2024 IBM report says the average data-breach cost has now exceeded USD 4.5 million, with regulatory fines constituting a large portion of the cost. In addition to economics, breaches tend to result in intellectual property loss, customer loss and long-term brand attenuation. Compliance ensures organisations remain within certain legislative necessities for collecting, holding, transferring and setting of personal and sensitive information. Failure to conformity can lead to serious penalties: under GDPR, fines could be up to 4% of the company's annual turnover or €20 million, whichever is higher. In regulated sectors like banking and healthcare, compliance breaches can also lead to the suspension of licenses.
Important Regulatory Frameworks Informing 2025
- GDPR and Its Global Ripple Effect
GDPR was enacted in 2018 and continues to have a ripple effect on privacy legislation worldwide. Its tenets of lawfulness, transparency, data minimisation and purpose limitation have been replicated in many jurisdictions such as Brazil's LGPD and South Korea's PIPA.
- India's DPDP Act
The DPDP Act, 2023, gives high importance to consent-based processing of data, transparent notice rules and fiduciary responsibilities for data. With a penalty for default of up to INR 250 crore, it's amongst the most impactful laws for digital personal data protection.
- Sectoral Regulations
- HIPAA for healthcare information in the US.
- PCI DSS for payment card security.
- DORA (Digital Operational Resilience Act) in the EU for financial organisations.
- These industry-specific models generate overlapping compliance responsibilities, making cross-enterprise compliance programs vital.
Key Pillars of a Sound Data Protection & Compliance Program
- Data Governance and Classification
Having insight into what data you have to store, where it is stored and who can have access to it is the keystone of compliance. Organisations need to have data classification policies in place to group information based on sensitivity and impose more rigorous controls on sensitive data.
- Security Controls and Privacy by Design
Strong technical defences, encryption, multi-factor authentication, and intrusion detection are the initial defences. Privacy by design integrated in product development guarantees compliance is thought through from the initial stage, not added on afterwards.
- Consent and Transparency
Contemporary data legislation highlights informed consent. This entails simple, non-technical privacy notices, detailed opt-in choices, and straightforward withdrawal options. Transparency produces trust and lessens legal danger.
- Incident Response and Breach Notification
Most laws demand timely breach notifications, and GDPR insists on reporting within 72 hours. Having a documented incident response plan maintains legal deadlines and reduces harm.
- Employee Training and Awareness
Human mistake is the top source of data breaches. Ongoing training in prevention of phishing, password management, basic cyber hygiene and compliance requirements is crucial.
Upcoming Trends in 2025
- AI-Powered Compliance Monitoring
Organisations are embracing AI-powered solutions to systematically monitor data flows, identify policy breaches and auto-create compliance reports. The solutions assist in closing the loop between IT security teams and compliance officers.
- Cross-Border Data Transfer Mechanisms
With increasingly severe regulations, companies are spending more on secure cross-border data transfer frameworks like Standard Contractual Clauses (SCCs) and Binding Corporate Rules (BCRs).
- Privacy-Enhancing Technologies (PETs)
Methods such as homomorphic encryption and differential privacy are picking up steam, enabling organisations to sift through datasets without revealing sensitive personal data.
- ESG and Data Ethics
Data handling is increasingly becoming a part of Environmental, Social and Governance (ESG) reporting. Ethical utilisation of customer data, not just compliance, has become a reputational differentiator.
Challenges in Implementation
Despite having transparent frameworks, data protection plans encounter challenges like jurisdictions having competing needs, and global compliance is becoming expensive. The emerging technologies, such as generative AI, often bring privacy threats that haven’t been fully covered by legislation. Small and micro enterprises have neither the budget nor the skills to implement enterprise-level compliance programs. Qualifying these challenges often needs a risk-based strategy, allocations of resources to top areas of impact and automating the compliance chores wherever possible.
Best Practices for 2025 and Beyond
In 2025, regulatory compliance and data protection are no longer a precaution or a response to a breach but are strategic drivers of resilience and trust. As regulatory analysis rises, cyber threats evolve, and consumer expectations grow, administrations need to integrate compliance into the very fabric of their actions. By bringing governance and technology together, organisations can break free from a "checklist" mentality and instead adopt a proactive and risk-sensitive approach. Eventually, data protection is not just about not getting in trouble; it's about developing a kind that succeeds in the digital era.
References
- GDPR – Official EU Regulation Page: https://gdpr.eu
- India’s DPDP Act Overview – MeitY: https://www.meity.gov.in/data-protection-framework
- HIPAA – US Department of Health & Human Services: https://www.hhs.gov/hipaa
- PCI DSS Standards: https://www.pcisecuritystandards.org
- IBM Cost of a Data Breach Report 2024: https://www.ibm.com/reports/data-breach
- OECD – Privacy Guidelines: https://www.oecd.org/sti/privacy-guidelines

Executive Summary:
A video went viral on social media claiming to show a bridge collapsing in Bihar. The video prompted panic and discussions across various social media platforms. However, an exhaustive inquiry determined this was not real video but AI-generated content engineered to look like a real bridge collapse. This is a clear case of misinformation being harvested to create panic and ambiguity.

Claim:
The viral video shows a real bridge collapse in Bihar, indicating possible infrastructure failure or a recent incident in the state.
Fact Check:
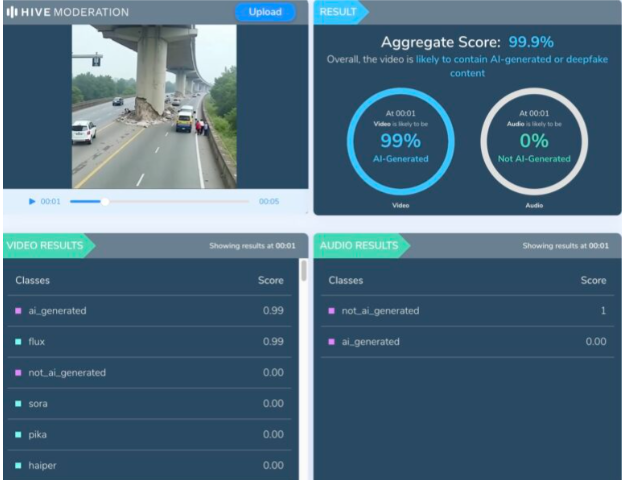
Upon examination of the viral video, various visual anomalies were highlighted, such as unnatural movements, disappearing people, and unusual debris behavior which suggested the footage was generated artificially. We used Hive AI Detector for AI detection, and it confirmed this, labelling the content as 99.9% AI. It is also noted that there is the absence of realism with the environment and some abrupt animation like effects that would not typically occur in actual footage.
No valid news outlet or government agency reported a recent bridge collapse in Bihar. All these factors clearly verify that the video is made up and not real, designed to mislead viewers into thinking it was a real-life disaster, utilizing artificial intelligence.
Conclusion:
The viral video is a fake and confirmed to be AI-generated. It falsely claims to show a bridge collapsing in Bihar. This kind of video fosters misinformation and illustrates a growing concern about using AI-generated videos to mislead viewers.
Claim: A recent viral video captures a real-time bridge failure incident in Bihar.
Claimed On: Social Media
Fact Check: False and Misleading

Introduction
Monopolies in any sector can have a great impact on economic efficiency and, by extension, on the market and the larger economy. Data monopolies hurt both small startups and large, established companies, and it is typically the biggest corporate players who have the biggest data advantage. Google has recently lost a major antitrust case filed by the U.S. Department of Justice, which focused on the company's search engine dominance and expensive partnerships to promote its products. The lawsuit accused Google of using its dominant position in the search engine market to maintain a monopoly. The case has had a significant impact on consumers and the tech industry as a whole. This dominance allowed Google to raise prices on advertisers without consequences, and delay innovations and privacy features that consumers want when they search online.
Antitrust Allegations Against Google in the US and EU
In the case filed by the US Department of Justice, US District Judge Amit Mehta ruled that Google was monopolistic. In the 10-week-long trial, Google lost the major antitrust lawsuit, and it was established that the tech giant had a monopoly in the web search and advertising sectors. The lawsuit accused Google of using its dominant position in the search engine market to elbow out rivals and maintain a monopoly. The tech giant’s exclusive deals with handset makers were brought before the court as evidence. Additionally, the European Commission has fined Google €1.49 billion for breaching EU antitrust rules in 2019.
The Impact of Big Tech Monopolies on the Digital Ecosystem and Beyond
- Big-tech companies collect vast amounts of personal data, raising concerns about how this data is used and protected. The concentration of data in the hands of a few companies can lead to privacy breaches and misuse of personal information.
- The dominance of a few tech giants in digital advertising markets can stifle competition, leading to higher prices for advertisers and fewer choices for consumers. This concentration also allows these companies to exert major control over what ads are shown and to whom.
- Big-tech platforms have substantial power over the dissemination of information. Their algorithms and policies on content moderation can influence public discourse and may spread misinformation. The lack of competition means fewer alternatives are accessible for users seeking different content moderation policies. In 2021 Google paid $26.3 billion to ensure its search engine is the default on smartphones and browsers and to keep control of its dominant market share.
Regulatory Mechanisms in the Indian Context
In India, antitrust issues are governed by the Competition Act of 2002 and the Competition Commission of India (CCI) checks monopolistic practices. In 2022, the CCI imposed a penalty of Rs 1,337.76 crore on Google for abusing its dominant position in multiple markets for 'anti-competitive practices' in the Android mobile device ecosystem. The Draft Digital Competition Bill, 2024, has been proposed as a legislative reform to regulate a wide range of digital services, including online search engines, social networking platforms, video-sharing sites, interpersonal communication services, operating systems, web browsers, cloud services, advertising services, and online intermediation services. The bill aims to promote competition and fairness in the digital market by addressing anti-competitive practices and dominant position abuses in the digital business space.
Conclusion
Big-tech companies are increasingly under scrutiny from regulators due to concerns over their monopolistic practices, data privacy issues, and the immense influence on markets and public discourse. The U.S. Department of Justice's victory against Google and the European Commission's hefty fines are indicators of a global paradigm shift towards more aggressive regulation to foster competition and protect consumer interests. The combined efforts of regulators across different jurisdictions underscore the recognition that monopolistic practices by such big tech giants can stifle innovation, harm consumers’ interests, and create barriers for new entrants, thus necessitating strong legal frameworks to ensure fair and contestable markets. Overall, the increasing regulatory pressure signifies a pivotal moment for big-tech companies, as they face the challenge of adapting to a more tightly controlled environment where their market dominance and business practices are under intense examination.
References
- https://www.livemint.com/technology/tech-news/googles-future-siege-u-s-court-explores-breaking-up-company-after-landmark-ruling-11723648047735.html
- https://www.thehindu.com/sci-tech/technology/what-is-the-google-monopoly-antitrust-case-and-how-does-it-affect-consumers/article68495551.ece
- https://indianexpress.com/article/business/google-has-an-illegal-monopoly-on-search-us-judge-finds-9497318/


