#FactCheck: Fake viral AI video captures a real-time bridge failure incident in Bihar
Executive Summary:
A video went viral on social media claiming to show a bridge collapsing in Bihar. The video prompted panic and discussions across various social media platforms. However, an exhaustive inquiry determined this was not real video but AI-generated content engineered to look like a real bridge collapse. This is a clear case of misinformation being harvested to create panic and ambiguity.

Claim:
The viral video shows a real bridge collapse in Bihar, indicating possible infrastructure failure or a recent incident in the state.
Fact Check:
Upon examination of the viral video, various visual anomalies were highlighted, such as unnatural movements, disappearing people, and unusual debris behavior which suggested the footage was generated artificially. We used Hive AI Detector for AI detection, and it confirmed this, labelling the content as 99.9% AI. It is also noted that there is the absence of realism with the environment and some abrupt animation like effects that would not typically occur in actual footage.
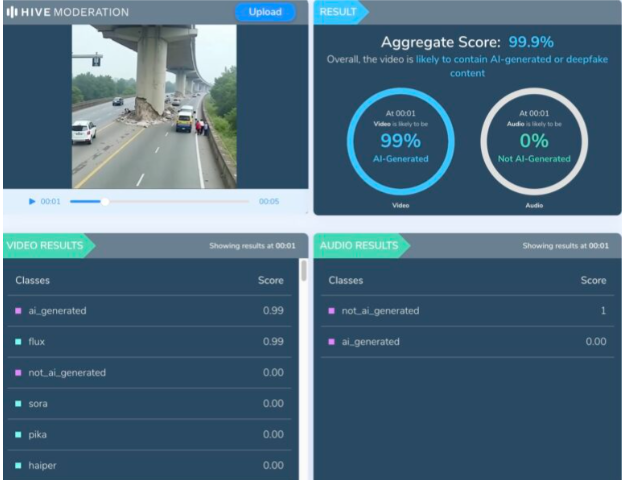
No valid news outlet or government agency reported a recent bridge collapse in Bihar. All these factors clearly verify that the video is made up and not real, designed to mislead viewers into thinking it was a real-life disaster, utilizing artificial intelligence.
Conclusion:
The viral video is a fake and confirmed to be AI-generated. It falsely claims to show a bridge collapsing in Bihar. This kind of video fosters misinformation and illustrates a growing concern about using AI-generated videos to mislead viewers.
Claim: A recent viral video captures a real-time bridge failure incident in Bihar.
Claimed On: Social Media
Fact Check: False and Misleading
Related Blogs

Executive Summary:
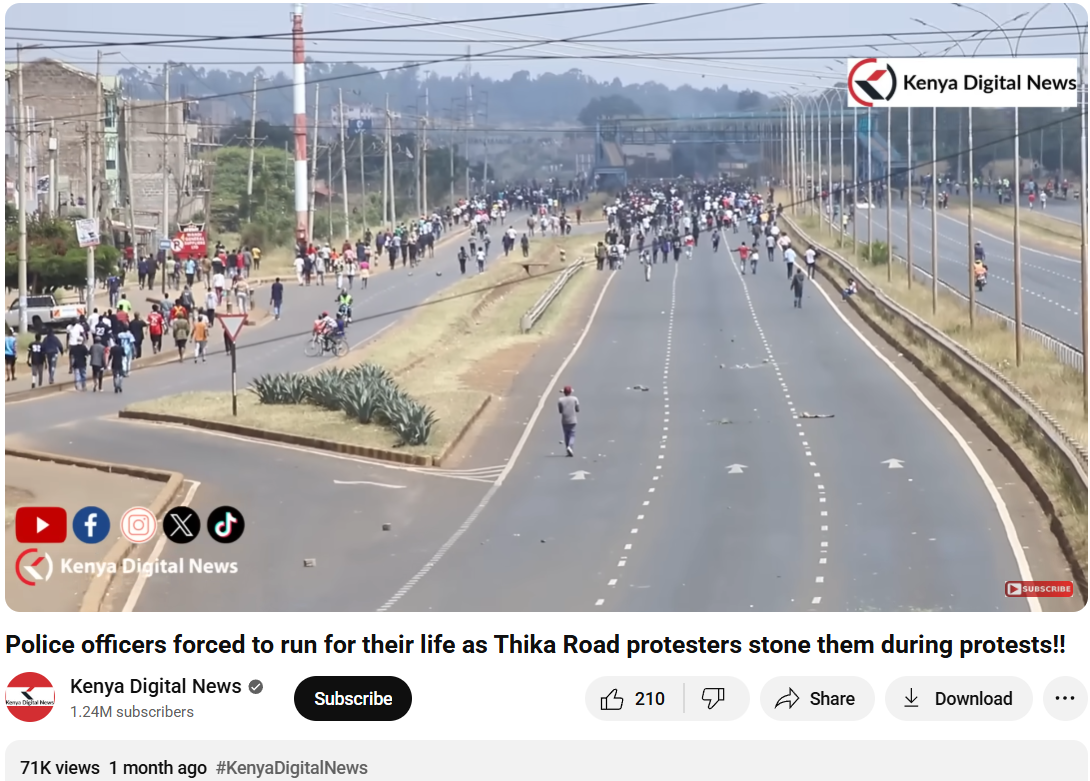
A video of people throwing rocks at vehicles is being shared widely on social media, claiming an incident of unrest in Jammu and Kashmir, India. However, our thorough research has revealed that the video is not from India, but from a protest in Kenya on 25 June 2025. Therefore, the video is misattributed and shared out of context to promote false information.

Claim:
The viral video shows people hurling stones at army or police vehicles and is claimed to be from Jammu and Kashmir, implying ongoing unrest and anti-government sentiment in the region.
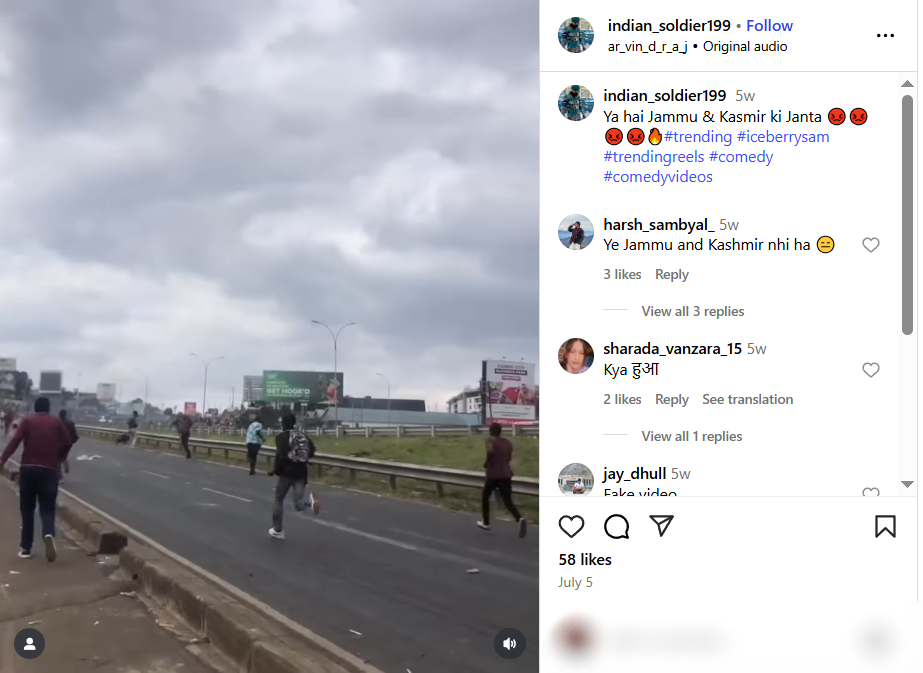
Fact Check:
To verify the validity of the viral statement, we did a reverse image search by taking key frames from the video. The results clearly demonstrated that the video was not sourced from Jammu and Kashmir as claimed, but rather it was consistent with footage from Nairobi, Kenya, where a significant protest took place on 25 June 2025. Protesters in Kenya had congregated to express their outrage against police brutality and government action, which ultimately led to violent clashes with police.
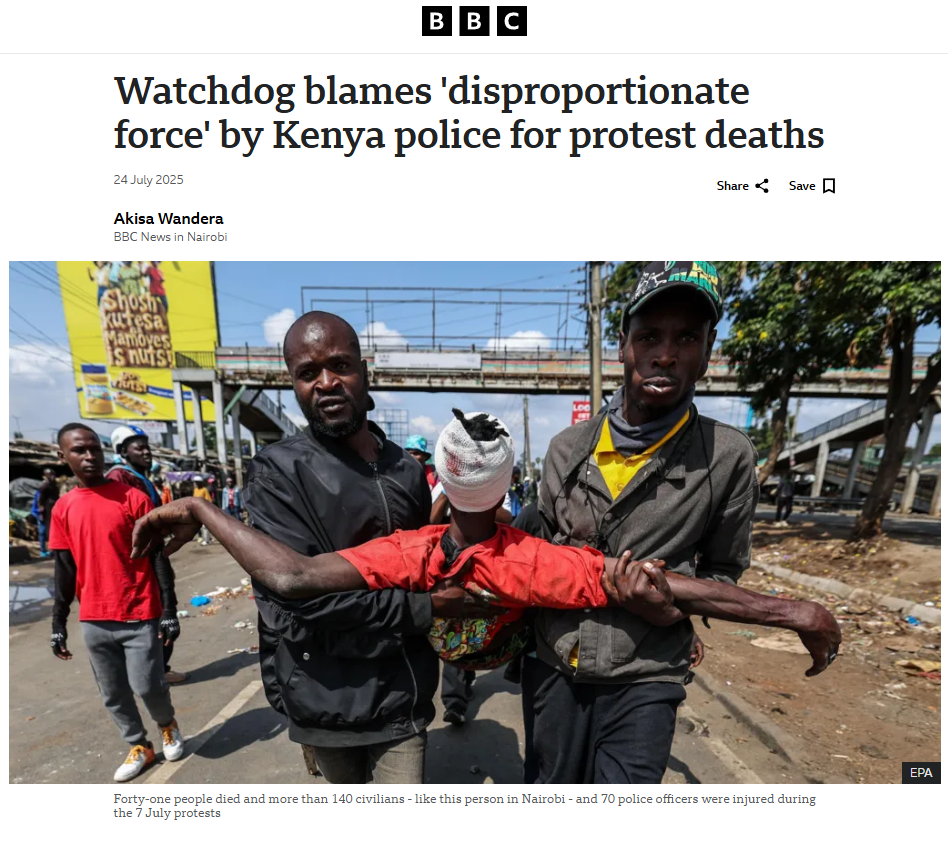
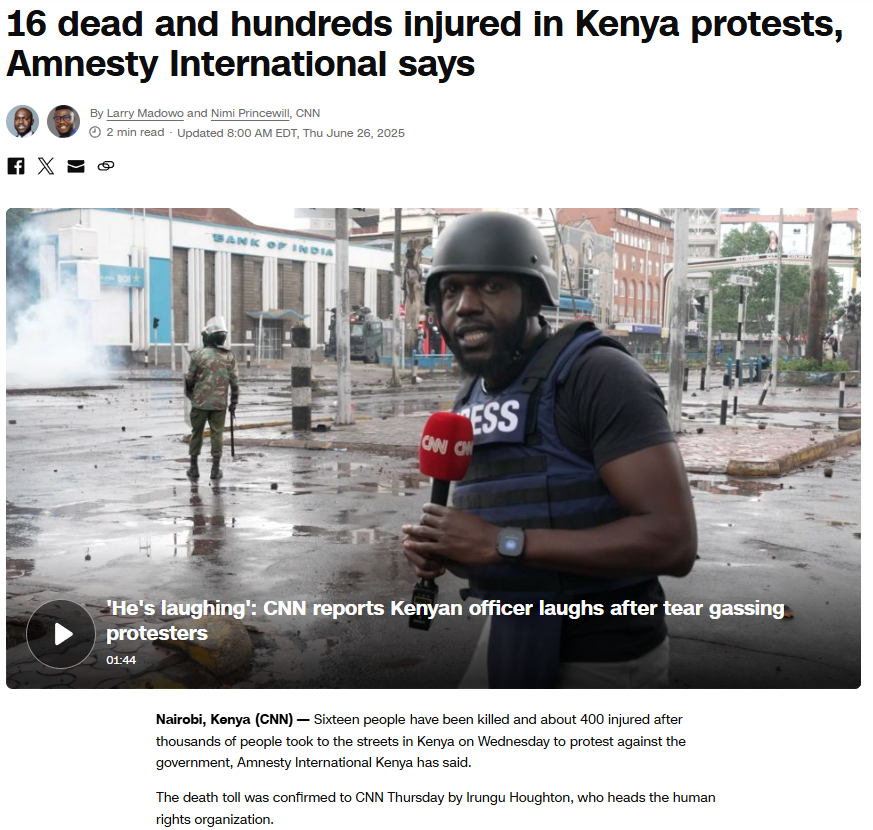
We also came across a YouTube video with similar news and frames. The protests were part of a broader anti-government movement to mark its one-year time period.
To support the context, we did a keyword search of any mob violence or recent unrest in J&K on a reputable Indian news source, But our search did not turn up any mention of protests or similar events in J&K around the relevant time. Based on this evidence, it is clear that the video has been intentionally misrepresented and is being circulated with false context to mislead viewers.
Conclusion:
The assertion that the viral video shows a protest in Jammu and Kashmir is incorrect. The video appears to be taken from a protest in Nairobi, Kenya, in June 2025. Labeling the video incorrectly only serves to spread misinformation and stir up uncalled for political emotions. Always be sure to verify where content is sourced from before you believe it or share it.
- Claim: Army faces heavy resistance from Kashmiri youth — the valley is in chaos.
- Claimed On: Social Media
- Fact Check: False and Misleading

AI systems have grown in both popularity and complexity on which they operate. They are enhancing accessibility for all, including people with disabilities, by revolutionising sectors including healthcare, education, and public services. We are at the stage where AI-powered solutions that can help people with mental, physical, visual or hearing impairments perform everyday and complex tasks are being created.
Generative AI is now being used to amplify human capability. The development of tools for speech-to-text and image recognition is helping in facilitating communication and interaction for visually or hearing-impaired individuals, and smart prosthetics are providing tailored support. Unfortunately, even with these developments, PWDs have continued to face challenges. Therefore, it is important to balance innovation with ethical considerations aand ensuring that these technologies are designed with qualities like privacy, equity, and inclusivity in mind.
Access to Tech: the Barriers Faced by PWDs
PWDs face several barriers while accessing technology. Identifying these challenges is important as they lack computer accessibility, in the use of hardware and software, which has become a norm in life nowadays. Website functions that only work when users click with a mouse, self-service kiosks without accessibility features, touch screens without screen reader software or tactile keyboards, and out-of-order equipment, such as lifts, captioning mirrors and description headsets, are just some difficulties that they face in their day-to-day life.
While they are helpful, much of the current technology doesn’t fully address all disabilities. For example, many assistive devices focus on visual or mobility impairments, but they fall short of addressing cognitive or sensory conditions. In addition to this, these solutions often lack personalisation, making them less effective for individuals with diverse needs. AI has significant potential to bridge this gap. With adaptive systems like voice assistants, real-time translation, and personalised features, AI can create more inclusive solutions, improving access to both digital and physical spaces for everyone.
The Importance of Inclusive AI Design
Creating an Inclusive AI design is important. It ensures that PWDs are not excluded from technological advancements because of the impairments that they are suffering from. The concept of an ‘inclusive or universal’ design promotes creating products and services that are usable for the widest possible range of people. Tech Developers have an ethical responsibility to create advancements in AI that serve everyone. Accessibility features should be built into the core design. They should be treated as a practice rather than an afterthought. However, bias in AI development often stems from data of a non-representative nature, or assumptions can lead to systems that overlook or poorly serve PWDs. If AI algorithms are trained on limited or biased data, they risk excluding marginalised groups, making ethical, inclusive design a necessity for equity and accessibility.
Regulatory Efforts to Ensure Accessible AI
In India, the Rights of Persons with Disabilities Act of 2016 impresses upon the need to provide PWDs with equal accessibility to technology. Subsequently, the DPDP Act of 2023 highlights data privacy concerns for the disabled under section 9 to process their data.
On the international level, the newly incorporated EU’s AI Act mandates measures for transparent, safe, and fair access to AI systems along with including measures that are related to accessibility.
In the US, the Americans with Disabilities Act of 1990 and Section 508 of the 1998 amendment to the Rehabilitation Act of 1973 are the primary legislations that work on promoting digital accessibility in public services.
Challenges in implementing Regulations for AI Accessibility for PWDs
Defining the term ‘inclusive AI’ is a challenge. When working on implementing regulations and compliance for the accessibility of AI, if the primary work is left undefined, it makes the task of creating tools to address the issue an issue. The rapid pace of tech and AI development has more often outpaced legal frameworks in development. This leads to the creation of enforcement gaps. Countries like Canada and tech industry giants like Microsoft and Google are leading forces behind creating accessible AI innovations. Their regulatory frameworks focus on developing AI ethics with inclusivity and collaboration with disability rights groups.
India’s efforts in creating an inclusive AI include the redesign of the Sugamya Bharat app. The app had been created to assist PWDs and the elderly. It will now be incorporating AI features specifically to assist the intended users.
Though AI development has opportunities for inclusivity, unregulated development can be risky. Regulation plays a critical role in ensuring that AI-driven solutions prioritise inclusivity, fairness, and accessibility, harnessing AI’s potential to empower PWDs and contribute to a more inclusive society.
Conclusion
AI development can offer PWDs unprecedented independence and accessibility in leading their lives. The development of AI while keeping inclusivity and fairness in mind is needed to be prioritised. AI that is free from bias, combined with robust regulatory frameworks, together are essential in ensuring that AI serves equitably. Collaborations between tech developers, policymakers, and disability advocates need to be supported and promoted to build AI systems. This will in turn work towards bridging the accessibility gaps for PWDs. As AI continues to evolve, maintaining a steadfast commitment to inclusivity will be crucial in preventing marginalisation and advancing true technological progress for all.
References
- https://www.business-standard.com/india-news/over-1-4k-accessibility-related-complaints-filed-on-govt-app-75-solved-124090800118_1.html
- https://www.forbes.com/councils/forbesbusinesscouncil/2023/06/16/empowering-individuals-with-disabilities-through-ai-technology/ .
- https://hbr.org/2023/08/designing-generative-ai-to-work-for-people-with-disabilities
- Thehttps://blogs.microsoft.com/on-the-issues/2018/05/07/using-ai-to-empower-people-with-disabilities/andensur,personalization
.webp)
Introduction
India's broadcasting sector has undergone significant changes in recent years with technological advancements such as the introduction of new platforms like Direct-to-Home (DTH), Internet Protocol television (IPTV), Over-The-Top (OTT), and integrated models. Platform changes, emerging technologies and advancements in the advertising space have all necessitated the need for new governing laws that take these developments into account.
The Union Government and concerned ministry have realised there is a pressing need to develop a robust regulatory framework for the Indian broadcasting sector in the country and consequently, a draft Broadcasting Services (Regulation) Bill, 2023, was released in November 2023 and the Union Ministry of Information and Broadcasting (MIB) had invited feedback and comments from different stakeholders. The draft Bill aims to establish a unified framework for regulating broadcasting services in the country, replacing the current Cable Television Networks (Regulation) Act, 1995 and other policy guidelines governing broadcasting.
Recently a new draft of an updated ‘Broadcasting Services (Regulation) Bill, 2024,’ was shared with selected broadcasters, associations, streaming services, and tech firms, each marked with their identifier to prevent leaks.
Key Highlights of the Updated Broadcasting Bill
As per the recent draft of the Broadcasting Services (Regulation) Bill, 2024, social media accounts could be identified as ‘Digital News Broadcasters’ and can be classified within the ambit of the regulation. Some of the major aspects of the new bill were first reported by Hindustan Times.
The new draft of the Broadcasting Services (Regulation) Bill, 2024, proposes that individuals who regularly upload videos to social media, make podcasts, or write about current affairs online could be classified as Digital News Broadcasters. This entails that YouTubers and Instagrammers who receive a share of advertising revenue or monetize their social media presence through affiliate activities will be regulated as Digital News Broadcasters. This includes channels, podcasts, and blogs that cover news and utilise Google AdSense. They must comply with a Programme Code and Advertising Code.
Online content creators who do not provide news or current affairs but provide programming and curated programs beyond a certain threshold will be treated as OTT broadcasters in case they provide content licensed or live through a website or social media platform.
The new version also introduces new obligations for intermediaries and social media intermediaries related to streaming services and digital news broadcasters, and, in contrast to the last version circulated in 2023, the latest also carries provisions targeting online advertising. In the context of streaming services, OTT broadcasting services are no longer a part of the definition of "internet broadcasting services." The definition of OTT broadcasting service has also been revised, allowing content creators who regularly upload their content to social media to be considered as OTT broadcasting services.
The new definition of an 'intermediary' includes social media intermediaries, advertisement intermediaries, internet service providers, online search engines, and online marketplaces.
The new Bill allows the government to prescribe different due diligence guidelines for social media platforms and online advertisement intermediaries and requires all intermediaries to provide appropriate information, including information pertaining to the OTT broadcasters and Digital News Broadcasters on their platform, to the central government to ensure compliance with the act. This entails the liability provisions for social media intermediaries which do not provide information “pertaining to OTT Broadcasters and Digital News Broadcasters” on its platforms for compliance. This suggests that when information is sought about a YouTube, Instagram or X/Twitter user, the platform will need to provide this information to the Indian government.
A new draft bill contains specific provisions governing ‘Online Advertising’ and to do so it creates the category of 'advertising intermediaries'. These intermediaries enable the buying or selling of advertisement space on the internet or placing advertisements on online platforms without endorsing the advertisement.
Final Words
The Indian Ministry of Information and Broadcasting (MIB) is making efforts to propose robust regulatory changes to the country's new-age broadcast sector, which would cover the specific provisions for Digital News Broadcasters, OTT Broadcasters and Intermediaries. The proposed bill defining the scope and obligation of each.
However, these changes will have significant implications for press and creative freedom. The changes in the new version of the updated bill from its previous draft expanded the applicability of the bill to a larger number of key actors, this move brought ‘content creators’ under the definition of OTT or digital news broadcasters, which raises concerns about overly rigid provisions and might face criticism from media representative perspectives.
According to recent media reports, the Broadcasting Services (Regulation) Bill, 2024 version has been withdrawn by the I&B ministry facing criticism from relevant stakeholders.
The ministry must take due consideration and feedback from concerned stakeholders and place reliance on balancing individual rights while promoting a healthy regulated landscape considering the needs of the new-age broadcasting sector.
References:
- https://www.medianama.com/2024/07/223-india-broadcast-bill-online-creators/#:~:text=Online%20content%20creators%20that%20do,or%20a%20social%20media%20platform.
- https://www.hindustantimes.com/india-news/new-draft-of-broadcasting-bill-news-influencers-may-be-classified-as-broadcasters-101721961764666.html
- https://www.hindustantimes.com/india-news/broadcasting-bill-still-in-drafting-stage-mib-tells-rs-101722058753083.html
- https://www.newslaundry.com/2024/07/29/indias-new-broadcast-bill-now-has-compliance-requirements-for-youtubers-and-instagrammers
- https://m.thewire.in/article/media/social-media-videos-text-digital-news-broadcasting-bill
- https://mib.gov.in/sites/default/files/Public%20Notice_07.12.2023.pdf
- https://news.abplive.com/news/india/centre-withdraws-draft-of-broadcasting-services-regulation-bill-1709770


