#FactCheck: Viral video claims BSF personnel thrashing a person selling Bangladesh National Flag in West Bengal
Executive Summary:
A video circulating online claims to show a man being assaulted by BSF personnel in India for selling Bangladesh flags at a football stadium. The footage has stirred strong reactions and cross border concerns. However, our research confirms that the video is neither recent nor related to the incident that occurred in India. The content has been wrongly framed and shared with misleading claims, misrepresenting the actual incident.
Claim:
It is being claimed through a viral post on social media that a Border Security Force (BSF) soldier physically attacked a man in India for allegedly selling the national flag of Bangladesh in West Bengal. The viral video further implies that the incident reflects political hostility towards Bangladesh within Indian territory.

Fact Check:
After conducting thorough research, including visual verification, reverse image searching, and confirming elements in the video background, we determined that the video was filmed outside of Bangabandhu National Stadium in Dhaka, Bangladesh, during the crowd buildup prior to the AFC Asian Cup. A match featuring Bangladesh against Singapore.

Second layer research confirmed that the man seen being assaulted is a local flag-seller named Hannan. There are eyewitness accounts and local news sources indicating that Bangladeshi Army officials were present to manage the crowd on the day under review. During the crowd control effort a soldier assaulted the vendor with excessive force. The incident created outrage to which the Army responded by identifying the officer responsible and taking disciplinary measures. The victim was reported to have been offered reparations for the misconduct.

Conclusion:
Our research confirms that the viral video does not depict any incident in India. The claim that a BSF officer assaulted a man for selling Bangladesh flags is completely false and misleading. The real incident occurred in Bangladesh, and involved a local army official during a football event crowd-control situation. This case highlights the importance of verifying viral content before sharing, as misinformation can lead to unnecessary panic, tension, and international misunderstanding.
- Claim: Viral video claims BSF personnel thrashing a person selling Bangladesh National Flag in West Bengal
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

Introduction
The Ministry of Electronics and Information Technology (MeitY) issued an advisory on March 1 2024, urging platforms to prevent bias, discrimination, and threats to electoral integrity by using AI, generative AI, LLMs, or other algorithms. The advisory requires that AI models deemed unreliable or under-tested in India must obtain explicit government permission before deployment. While leveraging Artificial Intelligence models, Generative AI, software, or algorithms in their computer resources, Intermediaries and platforms need to ensure that they prevent bias, discrimination, and threats to electoral integrity. As Intermediaries are required to follow due diligence obligations outlined under “Information Technology (Intermediary Guidelines and Digital Media Ethics Code)Rules, 2021, updated as of 06.04.2023”. This advisory is issued to urge the intermediaries to abide by the IT rules and regulations and compliance therein.
Key Highlights of the Advisories
- Intermediaries and platforms must ensure that users of Artificial Intelligence models/LLM/Generative AI, software, or algorithms do not allow users to host, display, upload, modify, publish, transmit, store, update, or share unlawful content, as per Rule 3(1)(b) of the IT Rules.
- The government emphasises intermediaries and platforms to prevent bias or discrimination in their use of Artificial Intelligence models, LLMs, and Generative AI, software, or algorithms, ensuring they do not threaten the integrity of the electoral process.
- The government requires explicit permission to use deemed under-testing or unreliable AI models, LLMs, or algorithms on the Indian internet. Further, it must be deployed with proper labelling of potential fallibility or unreliability. Further, users can be informed through a consent popup mechanism.
- The advisory specifies that all users should be well informed about the consequences of dealing with unlawful information on platforms, including disabling access, removing non-compliant information, suspension or termination of access or usage rights of the user to their user account and imposing punishment under applicable law. It entails that users are clearly informed, through terms of services and user agreements, about the consequences of engaging with unlawful information on the platform.
- The advisory also indicates measures advocating to combat deepfakes or misinformation. The advisory necessitates identifying synthetically created content across various formats, advising platforms to employ labels, unique identifiers, or metadata to ensure transparency. Furthermore, the advisory mandates the disclosure of software details and tracing the first originator of such synthetically created content.
Rajeev Chandrasekhar, Union Minister of State for IT, specified that
“Advisory is aimed at the Significant platforms, and permission seeking from Meity is only for large platforms and will not apply to startups. Advisory is aimed at untested AI platforms from deploying on the Indian Internet. Process of seeking permission , labelling & consent based disclosure to user about untested platforms is insurance policy to platforms who can otherwise be sued by consumers. Safety & Trust of India's Internet is a shared and common goal for Govt, users and Platforms.”
Conclusion
MeitY's advisory sets the stage for a more regulated Al landscape. The Indian government requires explicit permission for the deployment of under-testing or unreliable Artificial Intelligence models on the Indian Internet. Alongside intermediaries, the advisory also applies to digital platforms that incorporate Al elements. Advisory is aimed at significant platforms and will not apply to startups. This move safeguards users and fosters innovation by promoting responsible AI practices, paving the way for a more secure and inclusive digital environment.
References
- https://regmedia.co.uk/2024/03/04/meity_ai_advisory_1_march.pdf
- https://economictimes.indiatimes.com/tech/technology/govts-ai-advisory-will-not-apply-to-startups-mos-it-rajeev-chandrasekhar/articleshow/108197797.cms?from=mdr
- https://www.meity.gov.in/writereaddata/files/Advisory%2015March%202024.pdf
.webp)
Executive Summary:
A viral video claims to show a massive cumulonimbus cloud over Gurugram, Haryana, and Delhi NCR on 3rd September 2025. However, our research reveals the claim is misleading. A reverse image search traced the visuals to Lviv, Ukraine, dating back to August 2021. The footage matches earlier reports and was even covered by the Ukrainian news outlet 24 Kanal, which published the story under the headline “Lviv Covered by Unique Thundercloud: Amazing Video”. Thus, the viral claim linking the phenomenon to a recent event in India is false.
Claim:
A viral video circulating on social media claims to show a massive cloud formation over Gurugram, Haryana, and the Delhi NCR region on 3rd September 2025. The cloud appears to be a cumulonimbus formation, which is typically associated with heavy rainfall, thunderstorms, and severe weather conditions.

Fact Check:
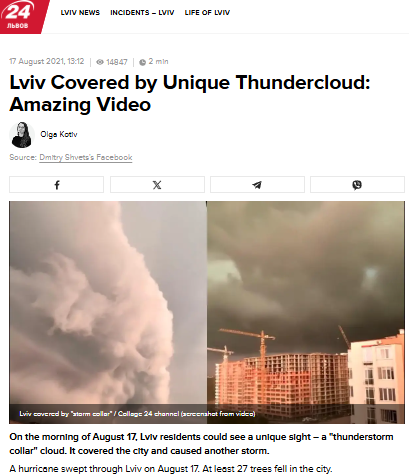
After conducting a reverse image search on key frames of the viral video, we found matching visuals from videos that attribute the phenomenon to Lviv, a city in Ukraine. These videos date back to August 2021, thereby debunking the claim that the footage depicts a recent weather event over Gurugram, Haryana, or the Delhi NCR region.
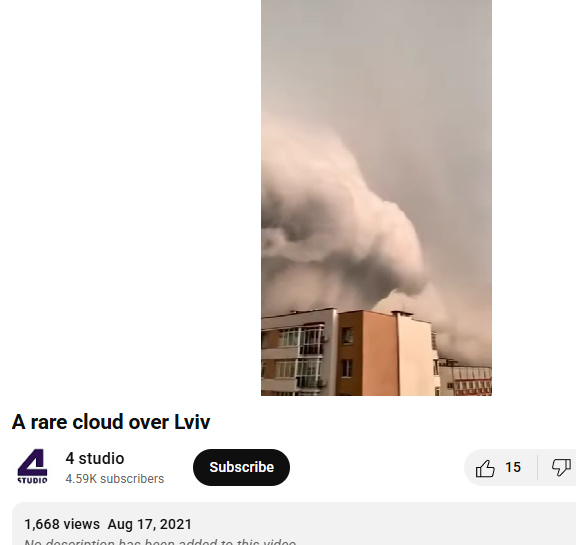

Further research revealed that a Ukrainian news channel named 24 Kanal, had reported on the Lviv thundercloud phenomenon in August 2021. The report was published under the headline “Lviv Covered by Unique Thundercloud: Amazing Video” ( original in Russian, translated into English).
Conclusion:
The viral video does not depict a recent weather event in Gurugram or Delhi NCR, but rather an old incident from Lviv, Ukraine, recorded in August 2021. Verified sources, including Ukrainian media coverage, confirm this. Hence, the circulating claim is misleading and false.
- Claim: Old Thundercloud Video from Lviv city in Ukraine Ukraine (2021) Falsely Linked to Delhi NCR, Gurugram and Haryana.
- Claimed On: Social Media
- Fact Check: False and Misleading.

Introduction
As the world is being "Digitally Interlaced", cyber security has become a continuous wrangle. The “Gambling industry” is considered an incredibly lucrative mark for cybercriminals, principally due to the enormous quantities of cash on hand and the sensitive details it processes day to day. Cybercriminals may use susceptibilities in gambling scaffolds to achieve financial scams or launder unlawful funds. An analysis by Security Scorecard discovered that the online gambling industry was ranked third in the possibility of encountering a cyber attack, following the energy and financial services sectors. Similarly, Online gambling is a bending matter that demands meticulous contemplation by policymakers and nationals. The incredible rise of online gambling has led to a terse acclivity in unlawful activities such as online scams, fraud, etc. Also, online sports gambling has become a thriving endeavour in contemporary years as millions of people are putting stakes and gambles on their electronic devices.
The Challenges
Online gambling has thus become a widespread frolicking for numerous youngsters, with the industry tossed to be worth billions of dollars in the forthcoming decades. The prominent cyber security challenges in the gambling industry are money laundering, financial laundering, ransomware, personal information theft, data breaches, distributed Denial of Service (DDoS), system disruptions and Insider perils and employee malfeasance. Challenges of online gambling also include being properly not regulated and a lack of social interaction with near and dear ones. The spread of Internet gambling has presented many problems affecting consumer behaviour online, motivations to gamble, problem gambling, security of websites, and the righteousness and virtue of the games. The rise of online gambling among young people due to the lack of clear regulations has likewise produced an abundant backdrop for financial ruination.
Web games and betting are among the fastest-evolving areas of the Internet. Over the past several years, there has been an international flare-up in online gambling, permitting customers to play from the convenience of home, work, and public locations. Numerous offshore betting websites and apps usually permit parties to win in the start with sound returns, whereas after the user gets addicted and invests considerable sums, they either keep failing or have the website refuse to cash out the winnings. Also, the information demonstrates that online games have been employed to commit wrongdoings (Child sexual exploitive material, religious conversion, cyberbullying, fraud, betting in virtual online casinos, etc.)
India's laws and regulations surrounding online gambling are complex and constantly evolving. While the legal framework is not entirely clear, a few state in India have their own set of rules.
Recently In April 2023, the Union Ministry of Electronics and Information Technology (“MeitY”), by virtue of the rule-making powers available to the central government under the Information Technology Act, 2000 (“IT Act 2000”), implemented a new central legal framework for online gaming through amendments to the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021 (“IT Rules 2021”). These amendments (“Online Gaming Rules”) propose a light-touch, co-regulatory regime whereby MeitY-recognised, independent self-regulatory bodies (“SRB”) will verify whether an “online real-money game” is to be made available to the general public or not – in accordance with the baseline criteria prescribed by the Online Gaming Rules.
The Online Gaming Rules attempt to regulate online gaming platforms by treating them as an “online gaming intermediary” (“OGI”) and prescribing intermediary due diligence obligations for them under the IT Rules 2021. An OGI has been defined in the Online Gaming Rules as “any intermediary that enables the users of its computer resource to access one or more online games”. Under the Online Gaming Rules, an online game can be a “permissible online game” if (i) it is not an online real-money game, or (ii) it is an online real-money game but is “verified” by an SRB in accordance with the baseline criteria prescribed by the Online Gaming Rules and any additional criteria prescribed by the SRB itself.
Global Perspective
The global gaming industry worth over US$227 billion in 2022 is further projected to grow to US$312 billion by 2027. Several countries have set regulatory frameworks about online gaming, though these are skewed, concentrating mainly on gambling and circumventing numerous of the more typical cyber threats. The US spends about $60 billion annually on online gambling and sports betting. In Europe, gambling is an even larger moneymaker. Also, numerous countries in Europe, like the UK, have legalised gambling. Nevertheless, it is prohibited for a US based company to operate an online gambling site. Yet, sports betting online is permitted in some states.
Today, though the gaming market has been overpowered by China and the US, future growth in the sector is anticipated to come from emerging economies like India with increasing populations. The permitted status of online gambling in India is nonetheless imprecise, vamoosing space for exploitation by cyber criminals and disarray for players involved. One of the climactic points that ought to be addressed is the sudden upsurge of online games, which increases gambling. Skill-based games such as poker, rummy etc., have additionally been developed to circumvent the legal definition of gambling in India. The recent instances of the online gaming industry not being properly regulated have also come to light in India. For instance, the Enforcement Directorate (ED) is still investigating the vast Mahadev Online Betting scandal, exposing an unknown money laundering method using Unified Payment Interface (UPI) IDs. Also, the Cyber Cell in Agra has taken proactive action against copyright violations, illegal online gambling and betting activities, shutting down 27 Illegal cricket betting sites in major operations, safeguarding several lakhs of Indians with thousands of crores from being transferred to overseas shores principally China.
Consequently, though India has announced new regulations on online gaming, its contemporary policy framework cannot contend with the problems endangering this sector. The Public Gambling Act of 1867 makes it unlawful to use a public gambling house or to be seen in one. Nevertheless, the act does not explicitly cite online gambling, leading to further interpretation. The Ministry of Home Affairs (MHA) has released a further awareness campaign for offshore illegal gambling apps, notifying users to be mindful of foreign apps as they may be fraudulent and might induce monetary damage to the user. Also, state laws control gambling in India with each state having its own directive on the subject. Yet, the Supreme Court of India has maintained that skilled games are not gambling and are thus legal. Furthermore, the Information Technology (IT) Act, of 2000 does not precisely handle online gambling or games that enable gambling.
Today, developers have strived for new ways to monetise the growing popularity of online gaming, which oversaw the creation of in-game currencies that can be bought using actual money, usually through credit cards. Several nations have prohibited the usage of in-game currency and loot boxes, considering them a kind of online gambling. The in-game currency has thus caused much disagreement about becoming a state of hunting monetisation by developers, especially targeting minor or newbie players. The gambling industry, therefore, faces unique cybersecurity challenges that require a comprehensive and proactive approach to cybersecurity.
Conclusion
Presently, there are approximately 3.09 billion active video game players worldwide, and the number is expected to reach 3.32 billion by 2024 as of 2023. In the contemporary digital era, information is priceless, and encryption acts as a necessary means to safeguard it. Thus, Regulators are working to maintain the swiftness of shift in the industry, as the dearth of transparency in the law has made it challenging to implement regulations. There is also less awareness about cyber security in India due to the following grounds such as the lack of ethical hackers in the country, companies in India lacking focus on cyber security and hiring a team of ethical hackers and cyber security experts. Furthermore, there has been a lack of knowledge among the citizens as well.
It is essential to realise the conceivable social and economic consequences and take measures to handle the online gambling industry. The industry has thus been undersized in the mode of research following online crime and Internet gambling, even though it is an acute emphasis. There is also a pressing necessity to rebuild these regulations to tackle the more unbridled cyber security hazards swarming the gaming industry. Similarly, there is an urgent need for governments and policymakers around the world to start paying more attention to the gaming industry as cyber security threats continue to rise. There should be a further need to strengthen the regulatory framework, establish Self Regulatory Organizations (SROs), create ethical gaming designs and increase awareness among gamers. The Government of India should consider devising its own rating system to rate games so that players under 18 cannot access them.
Eventually, cyber security is a shared commitment, and everyone in the online gambling ecosystem must function jointly to provide a secure and safe setting for all.
References:
- https://truefort.com/gambling-industry-cybersecurity/
- https://www.orfonline.org/research/cybersecurity-threats-in-online-gaming-learnings-for-india
- https://www.hackread.com/chinese-scammers-cloned-websites-gambling-network/
- https://www.civilsdaily.com/news/cybersecurity-threats-from-online-gaming/
- https://www.linkedin.com/pulse/legal-considerations-online-gambling-india-sudden-increase-mathur/
- https://www.jsheld.com/insights/articles/the-importance-of-cybersecurity-in-the-online-sports-betting-industry
- https://www.the420.in/agra-cyber-cell-takes-down-27-illegal-betting-sites/
- https://g2g.news/gaming/ministry-of-home-affairs-releases-new-awareness-campaign-for-online-gaming-in-india/
- https://smestreet.in/technology/kaspersky-warns-of-increased-phishing-scams-and-data-breaches-in-apac-for-2024-2381601
- https://economictimes.indiatimes.com/tech/newsletters/morning-dispatch/govt-bans-mahadev-other-illegal-betting-apps-cyber-attacks-against-india-spike/articleshow/104996017.cms?from=mdr
- https://cipher.com/cybersecurity-for-gambling/
- https://www.mangalorean.com/tightening-the-reins-indian-government-blocks-over-550-illegal-betting-and-gambling-apps/
- https://cybersecurityasean.com/news-press-releases/kaspersky-predicts-rise-cyber-threats-across-apac-2024
- https://www.cnbctv18.com/technology/mahadev-betting-app-scam-ed-money-laundering-upi-celebrities-under-scanner-17815661.htm
- https://iclg.com/practice-areas/gambling-laws-and-regulations/india


