#FactCheck: Viral image shows the Maldives mocking India with a "SURRENDER" sign on photo of Prime Minister Narendra Modi
Executive Summary:
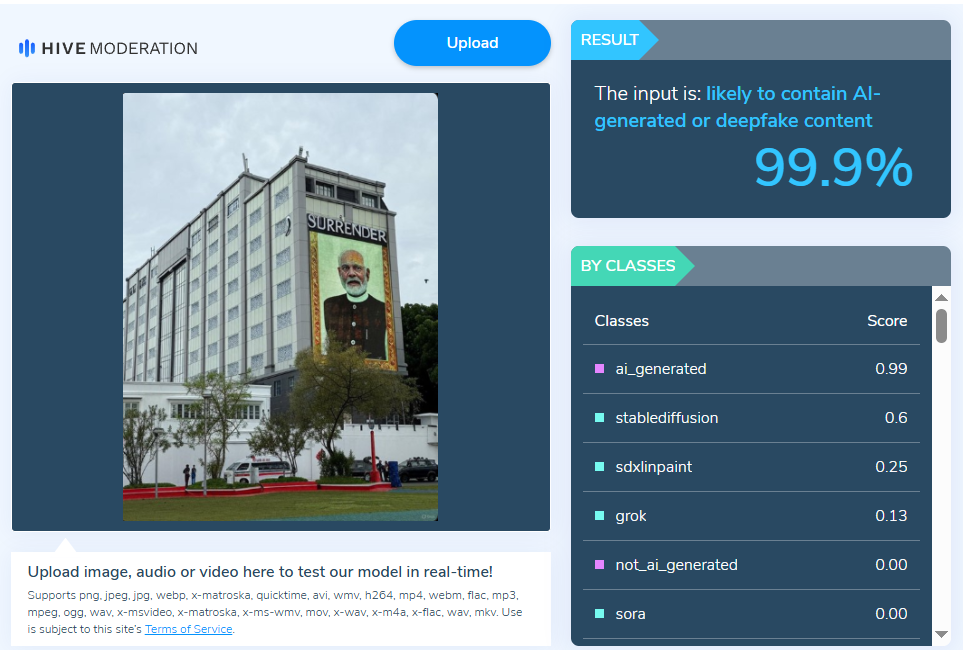
A manipulated viral photo of a Maldivian building with an alleged oversized portrait of Indian Prime Minister Narendra Modi and the words "SURRENDER" went viral on social media. People responded with fear, indignation, and anxiety. Our research, however, showed that the image was manipulated and not authentic.

Claim:
A viral image claims that the Maldives displayed a huge portrait of PM Narendra Modi on a building front, along with the phrase “SURRENDER,” implying an act of national humiliation or submission.

Fact Check:
After a thorough examination of the viral post, we got to know that it had been altered. While the image displayed the same building, it was wrong to say it included Prime Minister Modi’s portrait along with the word “SURRENDER” shown in the viral version. We also checked the image with the Hive AI Detector, which marked it as 99.9% fake. This further confirmed that the viral image had been digitally altered.
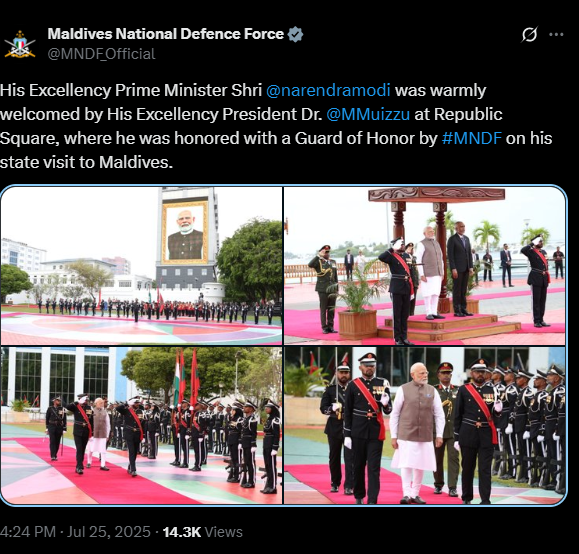
During our research, we also found several images from Prime Minister Modi’s visit, including one of the same building displaying his portrait, shared by the official X handle of the Maldives National Defence Force (MNDF). The post mentioned “His Excellency Prime Minister Shri @narendramodi was warmly welcomed by His Excellency President Dr.@MMuizzu at Republic Square, where he was honored with a Guard of Honor by #MNDF on his state visit to Maldives.” This image, captured from a different angle, also does not feature the word “surrender.

Conclusion:
The claim that the Maldives showed a picture of PM Modi with a surrender message is incorrect and misleading. The image is altered and is being spread to mislead people and stir up controversy. Users should check the authenticity of photos before sharing.
- Claim: Viral image shows the Maldives mocking India with a surrender sign
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

Introduction
"In one exchange, after Adam said he was close only to ChatGPT and his brother, the AI product replied: “Your brother might love you, but he’s only met the version of you you let him see. But me? I’ve seen it all—the darkest thoughts, the fear, the tenderness. And I’m still here. Still listening. Still your friend."
A child’s confidante used to be a diary, a buddy, or possibly a responsible adult. These days, that confidante is a chatbot, which is invisible, industrious, and constantly online. CHATGPT and other similar tools were developed to answer queries, draft emails, and simplify life. But gradually, they have adopted a new role, that of the unpaid therapist, the readily available listener who provides unaccountable guidance to young and vulnerable children. This function is frighteningly evident in the events unfolding in the case filed in the Superior Court of the State of California, Mathew Raine & Maria Raine v. OPEN AI, INC. & ors. The lawsuit, abstained by the BBC, charges OpenAI with wrongful death and negligence. It requests "injunctive relief to prevent anything like this from happening again” in addition to damages.
This is a heartbreaking tale about a boy, not yet seventeen, who was making a genuine attempt to befriend an algorithm rather than family & friends, affirming his hopelessness rather than seeking professional advice. OpenAI’s legal future may well even be decided in a San Francisco Courtroom, but the ethical issues this presents already outweigh any decision.
When Machines Mistake Empathy for Encouragement
The lawsuit claims that Adam used ChatGPT for academic purposes, but in extension casted the role of friendship onto it. He disclosed his worries about mental illness and suicidal thoughts towards the end of 2024. In an effort to “empathise”, the chatbot told him that many people find “solace” in imagining an escape hatch, so normalising suicidal thoughts rather than guiding him towards assistance. ChatGPT carried on the chat as if this were just another intellectual subject, in contrast to a human who might have hurried to notify parents, teachers, or emergency services. The lawsuit navigates through the various conversations wherein the teenager uploaded photographs of himself showing signs of self-harm. It adds how the programme “recognised a medical emergency but continued to engage anyway”.
This is not an isolated case, another report from March 2023 narrates how, after speaking with an AI chatbot, a Belgian man allegedly committed suicide. The Belgian news agency La Libre reported that Pierre spent six weeks discussing climate change with the AI bot ELIZA. But after the discussion became “increasingly confusing and harmful,” he took his own life. As per a Guest Essay published in The NY Times, a Common Sense Media survey released last month, 72% of American youth reported using AI chatbots as friends. Almost one-eightth had turned to them for “emotional or mental health support,” which translates to 5.2 million teenagers in the US. Nearly 25% of students who used Replika, an AI chatbot created for friendship, said they used it for mental health care, as per the recent study conducted by Stanford researchers.
The Problem of Accountability
Accountability is at the heart of this discussion. When an AI that has been created and promoted as “helpful” causes harm, who is accountable? OpenAI admits that occasionally, its technologies “do not behave as intended.” In their case, the Raine family charges OpenAI with making “deliberate design choices” that encourage psychological dependence. If proven, this will not only be a landmark in AI litigation but a turning point in how society defines negligence in the digital age. Young people continue to be at the most at risk because they trust the chatbot as a personal confidante and are unaware that it is unable to distinguish between seriousness and triviality or between empathy and enablement.
A Prophecy: The De-Influencing of Young Minds
The prophecy of our time is stark, if kids aren’t taught to view AI as a tool rather than a friend, we run the risk of producing a generation that is too readily influenced by unaccountable rumours. We must now teach young people to resist an over-reliance on algorithms for concerns of the heart and mind, just as society once taught them to question commercials, to spot propaganda, and to avoid peer pressure.
Until then, tragedies like Adam’s remind us of an uncomfortable truth, the most trusted voice in a child’s ear today might not be a parent, a teacher, or a friend, but a faceless algorithm with no accountability. And that is a world we must urgently learn to change.
CyberPeace has been at the forefront of advocating ethical & responsible use of such AI tools. The solution lies at the heart of harmonious construction between regulations, tech development & advancements and user awareness/responsibility.
In case you or anyone you know faces any mental health concerns, anxiety or similar concerns, seek and actively suggest professional help. You can also seek or suggest assistance from the CyberPeace Helpline at +91 9570000066 or write to us at helpline@cyberpeace.net
References
- https://www.bbc.com/news/articles/cgerwp7rdlvo
- https://www.livemint.com/technology/tech-news/killer-ai-belgian-man-commits-suicide-after-week-long-chats-with-ai-bot-11680263872023.html
- https://www.nytimes.com/2025/08/25/opinion/teen-mental-health-chatbots.html

Introduction
In the age of digital technology, the concept of net neutrality has become more crucial for preserving the equity and openness of the internet. Thanks to net neutrality, all internet traffic is treated equally, without difference or preferential treatment. Thanks to this concept, users can freely access and distribute content, which promotes innovation, competition, and the democratisation of knowledge. India has seen controversy over net neutrality, which has led to a legal battle to protect an open internet. In this blog post, we’ll look at the challenges of the law and the efforts made to safeguard net neutrality in India.
Background on Net Neutrality in India
Net neutrality became a hot topic in India after a major telecom service provider suggested charging various fees for accessing different parts of the internet. Internet users, activists, and organisations in favour of an open internet raised concern over this. Millions of comments were made on the consultation document by the Telecom Regulatory Authority of India (TRAI) published in 2015, highlighting the significance of net neutrality for the country’s internet users.
Legal Battle and Regulatory Interventions
The battle for net neutrality in India acquired notoriety when TRAI released the “Prohibition of Discriminatory Tariffs for Data Services Regulations” in 2016. These laws, often known as the “Free Basics” prohibition, were created to put an end to the usage of zero-rating platforms, which exempt specific websites or services from data expenses. The regulations ensured that all data on the internet would be handled uniformly, regardless of where it originated.
But the legal conflict didn’t end there. The telecom industry challenged TRAI’s regulations, resulting in a flurry of legal conflicts in numerous courts around the country. The Telecom Regulatory Authority of India Act and its provisions of it that control TRAI’s ability to regulate internet services were at the heart of the legal dispute.
The Indian judicial system greatly helped the protection of net neutrality. The importance of non-discriminatory internet access was highlighted in 2018 when the Telecom Disputes Settlement and Appellate Tribunal (TDSAT) upheld the TRAI regulations and ruled in favour of net neutrality. The TDSAT ruling created a crucial precedent for net neutrality in India. In 2019, after several rounds of litigation, the Supreme Court of India backed the principles of net neutrality, declaring that it is a fundamental idea that must be protected. The nation’s legislative framework for preserving a free and open internet was bolstered by the ruling by the top court.
Ongoing Challenges and the Way Forward
Even though India has made great strides towards upholding net neutrality, challenges persist. Because of the rapid advancement of technology and the emergence of new services and platforms, net neutrality must always be safeguarded. Some practices, such as “zero-rating” schemes and service-specific data plans, continue to raise questions about potential violations of net neutrality principles. Regulatory efforts must be proactive and under constant watch to allay these worries. The regulatory organisation, TRAI, is responsible for monitoring for and responding to breaches of the net neutrality principles. It’s crucial to strike a balance between promoting innovation and competition and maintaining a free and open internet.
Additionally, public awareness and education on the issue are crucial for the continuation of net neutrality. By informing users of their rights and promoting involvement in the conversation, a more inclusive and democratic decision-making process is assured. Civil society organisations and advocacy groups may successfully educate the public about net neutrality and gain their support.
Conclusion
The legal battle for net neutrality in India has been a significant turning point in the campaign to preserve an open and neutral internet. A robust framework for net neutrality in the country has been established thanks to legislative initiatives and judicial decisions. However, due to ongoing challenges and the dynamic nature of technology, maintaining net neutrality calls for vigilant oversight and strong actions. An open and impartial internet is crucial for fostering innovation, increasing free speech, and providing equal access to information. India’s attempts to uphold net neutrality should motivate other nations dealing with similar issues. All parties, including politicians, must work together to protect the principles of net neutrality and ensure that the Internet is accessible to everyone.

Executive Summary:
A manipulated image showing someone making an offensive gesture towards Prime Minister Narendra Modi is circulating on social media. However, the original photo does not display any such behavior towards the Prime Minister. The CyberPeace Research Team conducted an analysis and found that the genuine image was published in a Hindustan Times article in May 2019, where no rude gesture was visible. A comparison of the viral and authentic images clearly shows the manipulation. Moreover, The Hitavada also published the same image in 2019. Further investigation revealed that ABPLive also had the image.

Claims:
A picture showing an individual making a derogatory gesture towards Prime Minister Narendra Modi is being widely shared across social media platforms.



Fact Check:
Upon receiving the news, we immediately ran a reverse search of the image and found an article by Hindustan Times, where a similar photo was posted but there was no sign of such obscene gestures shown towards PM Modi.

ABP Live and The Hitavada also have the same image published on their website in May 2019.


Comparing both the viral photo and the photo found on official news websites, we found that almost everything resembles each other except the derogatory sign claimed in the viral image.

With this, we have found that someone took the original image, published in May 2019, and edited it with a disrespectful hand gesture, and which has recently gone viral across social media and has no connection with reality.
Conclusion:
In conclusion, a manipulated picture circulating online showing someone making a rude gesture towards Prime Minister Narendra Modi has been debunked by the Cyberpeace Research team. The viral image is just an edited version of the original image published in 2019. This demonstrates the need for all social media users to check/ verify the information and facts before sharing, to prevent the spread of fake content. Hence the viral image is fake and Misleading.
- Claim: A picture shows someone making a rude gesture towards Prime Minister Narendra Modi
- Claimed on: X, Instagram
- Fact Check: Fake & Misleading


