#Factcheck-Viral Image of Men Riding an Elephant Next to a Tiger in Bihar is Misleading
Executive Summary:
A post on X (formerly Twitter) featuring an image that has been widely shared with misleading captions, claiming to show men riding an elephant next to a tiger in Bihar, India. This post has sparked both fascination and skepticism on social media. However, our investigation has revealed that the image is misleading. It is not a recent photograph; rather, it is a photo of an incident from 2011. Always verify claims before sharing.

Claims:
An image purporting to depict men riding an elephant next to a tiger in Bihar has gone viral, implying that this astonishing event truly took place.

Fact Check:
After investigation of the viral image using Reverse Image Search shows that it comes from an older video. The footage shows a tiger that was shot after it became a man-eater by forest guard. The tiger killed six people and caused panic in local villages in the Ramnagar division of Uttarakhand in January, 2011.

Before sharing viral posts, take a brief moment to verify the facts. Misinformation spreads quickly and it’s far better to rely on trusted fact-checking sources.
Conclusion:
The claim that men rode an elephant alongside a tiger in Bihar is false. The photo presented as recent actually originates from the past and does not depict a current event. Social media users should exercise caution and verify sensational claims before sharing them.
- Claim: The video shows people casually interacting with a tiger in Bihar
- Claimed On:Instagram and X (Formerly Known As Twitter)
- Fact Check: False and Misleading
Related Blogs

Introduction
The Union Minister of Information and Broadcasting Ashwini Vaishnaw addressed the Press Council of India on the occasion of National Press Day regarding emergent concerns in the digital media and technology landscape. Union Minister of Information and Broadcasting Ashwini Vaishnaw has identified four major challenges facing news media in India, including fake news, algorithmic bias, artificial intelligence, and fair compensation. He emphasized the need for greater accountability and fairness from Big Tech to combat misinformation and protect democracy. Vaishnaw argued that platforms do not verify information posted online, leading to the spread of false and misleading information. He called on online platforms and Big Tech to combat misinformation and protect democracy.
Key Concerns Highlighted by Union Minister Ashwini Vaishnaw
- Misinformation: Due to India's unique sensitivities, digital platforms should adopt country-specific responsibilities and metrics. The Minister also questioned the safe harbour principle, which shields platforms from liability for user-generated content.
- Algorithmic Biases: The prioritisation of viral content, which is often divisive, by social media algorithms can have serious implications on societal peace.
- Impact of AI on intellectual Property: The training of AI on pre-existing datasets presents the ethical challenge of robbing original creators of their rights to their intellectual property
- Fair compensation: Traditional news media is increasingly facing financial strain since news consumption is shifting rapidly to social media platforms, creating uneven compensation dynamics.
Cyberpeace Insights
- Misinformation: Marked by routine upheavals and moral panics, Indian society is vulnerable to the severe impacts of fake news, including mob violence, political propaganda, health misinformation and more. Inspired by the EU's Digital Services Act, 2022, and other related legislation that addresses hate speech and misinformation, the Indian Minister has called for revisiting the safe harbour protection under Section 79 of the IT Act, 2000. However, any legislation on misinformation must strike a balance between protecting the fundamental rights to freedom of speech, and privacy while safeguarding citizens from its harmful effects.
- Algorithmic Biases: Social media algorithms are designed to boost user engagement since this increases advertisement revenue. This leads to the creation of filter bubbles- exposure to personalized information online and echo chambers interaction with other users with the same opinions that align with their worldview. These phenomena induce radicalization of views, increase intolerance fuel polarization in public discourse, and trigger the spread of more misinformation. Tackling this requires algorithmic design changes such as disincentivizing sensationalism, content labelling, funding fact-checking networks, etc. to improve transparency.
- Impact of AI on Intellectual Property: AI models are trained on data that may contain copyrighted material. It can lead to a loss of revenue for primary content creators, while tech companies owning AI models may financially benefit disproportionately by re-rendering their original works. Large-scale uptake of AI models will significantly impact fields such as advertising, journalism, entertainment, etc by disrupting their market. Managing this requires a push for Ethical AI regulations and the protection of original content creators.
Conclusion: Charting a Balanced Path
The socio-cultural and economic fabric of the Indian subcontinent is not only distinct from the rest of the world but has cross-cutting internal diversities, too. Its digital landscape stands at a crossroads as rapid global technological advancements present increasing opportunities and challenges. In light of growing incidents of misinformation on social media platforms, it is also crucial that regulators consider framing rules that encourage and mandate content verification mechanisms for online platforms, incentivizing them to adopt advanced AI-driven fact-checking tools and other relevant measures. Additionally, establishing public-private partnerships to monitor misinformation trends is crucial to rapidly debunking viral falsehoods. However ethical concerns and user privacy should be taken into consideration while taking such steps. Addressing misinformation requires a collaborative approach that balances platform accountability, technological innovation, and the protection of democratic values.
Sources
- https://www.indiatoday.in/india/story/news-media-4-challenges-ashwini-vaishnaw-national-press-day-speech-big-tech-fake-news-algorithm-ai-2634737-2024-11-17
- https://ec.europa.eu/commission/presscorner/detail/en/ip_24_881
- https://www.legaldive.com/news/digital-services-act-dsa-eu-misinformation-law-propaganda-compliance-facebook-gdpr/691657/
- https://www.fondationdescartes.org/en/2020/07/filter-bubbles-and-echo-chambers/
- https://www.google.com/searchq=News+Media+Bargaining+Code&oq=News+Media+Bargaining+Code&gs_lcrp=EgZjaHJvbWUyBggAEEUYOTIHCAEQABiABDIHCAIQABiABDIHCAMQABiABDIHCAQQABiABDIHCAUQABiABDIICAYQABgWGB4yCAgHEAAYFhgeMggICBAAGBYYHjIICAkQABgWGB7SAQcyMjVqMGo3qAIIsAIB&sourceid=chrome&ie=UTF-8

Executive Summary
A video showing a group of people wearing Muslim caps raising provocative slogans against the Rashtriya Swayamsevak Sangh (RSS) is being widely shared on social media. Users sharing the clip claim that the incident took place recently in Uttar Pradesh. However, CyberPeace research found the claim to be false. The probe established that the video is neither recent nor related to Uttar Pradesh. In fact, the footage dates back to 2022 and is from Telangana. The slogans heard in the video were raised during a protest against Goshamahal MLA T. Raja Singh, and the clip is now being circulated with a misleading claim.
Claim
On January 21, 2026, a user on social media platform X (formerly Twitter) shared the video claiming it showed people in Uttar Pradesh chanting slogans such as, “Kaat daalo saalon ko, RSS walon ko” and “Gustakh-e-Nabi ka sar chahiye.” The post suggested that such slogans were being raised openly in Uttar Pradesh despite strict law enforcement. Links to the post and its archive are provided below.
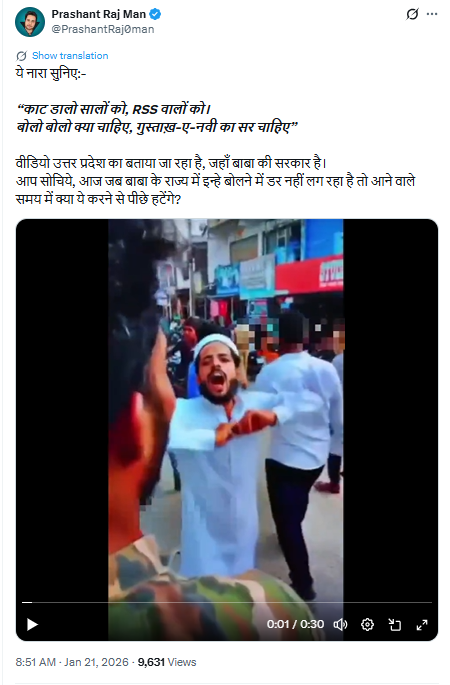
Fact Check:
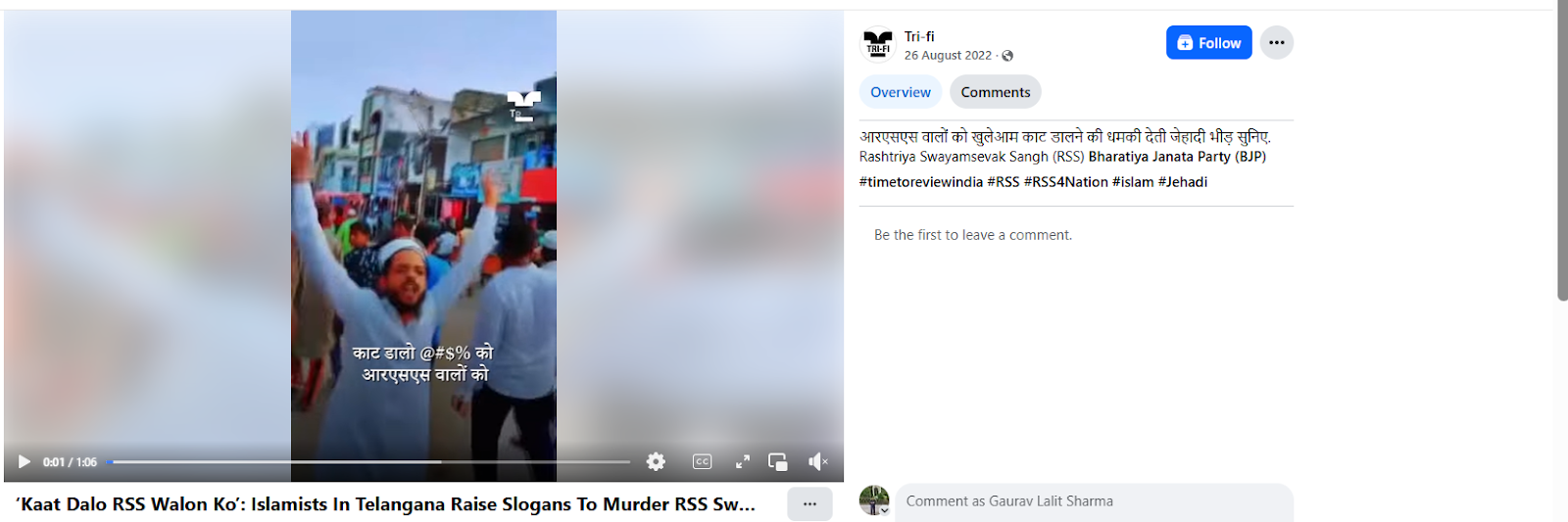
To verify the claim, CyberPeace research conducted a reverse image search using keyframes from the viral video. The same footage was found on a Facebook account where it had been uploaded on August 26, 2022, indicating that the video is not recent.
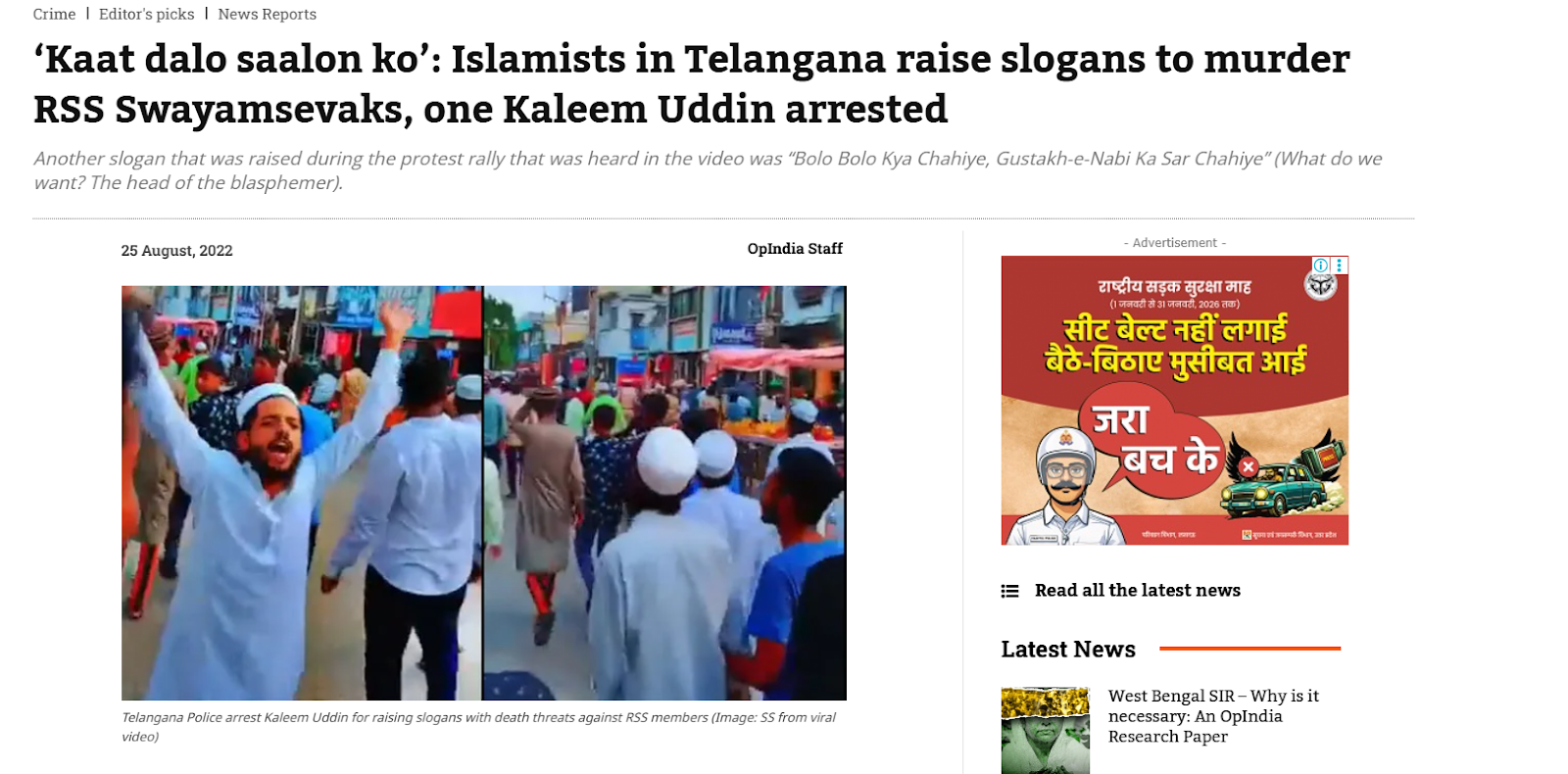
Further verification led the team to a report published by news portal OpIndia on August 25, 2022, which featured identical visuals from the viral clip. According to the report, the video showed a protest march organised against BJP MLA T. Raja Singh following his alleged controversial remarks about Prophet Muhammad. The report identified one of the individuals in the video as Kaleem Uddin, who was allegedly heard raising the slogan “Kaat daalo saalon ko,” to which the crowd responded “RSS walon ko.” The slogan was linked to incitement against RSS members.
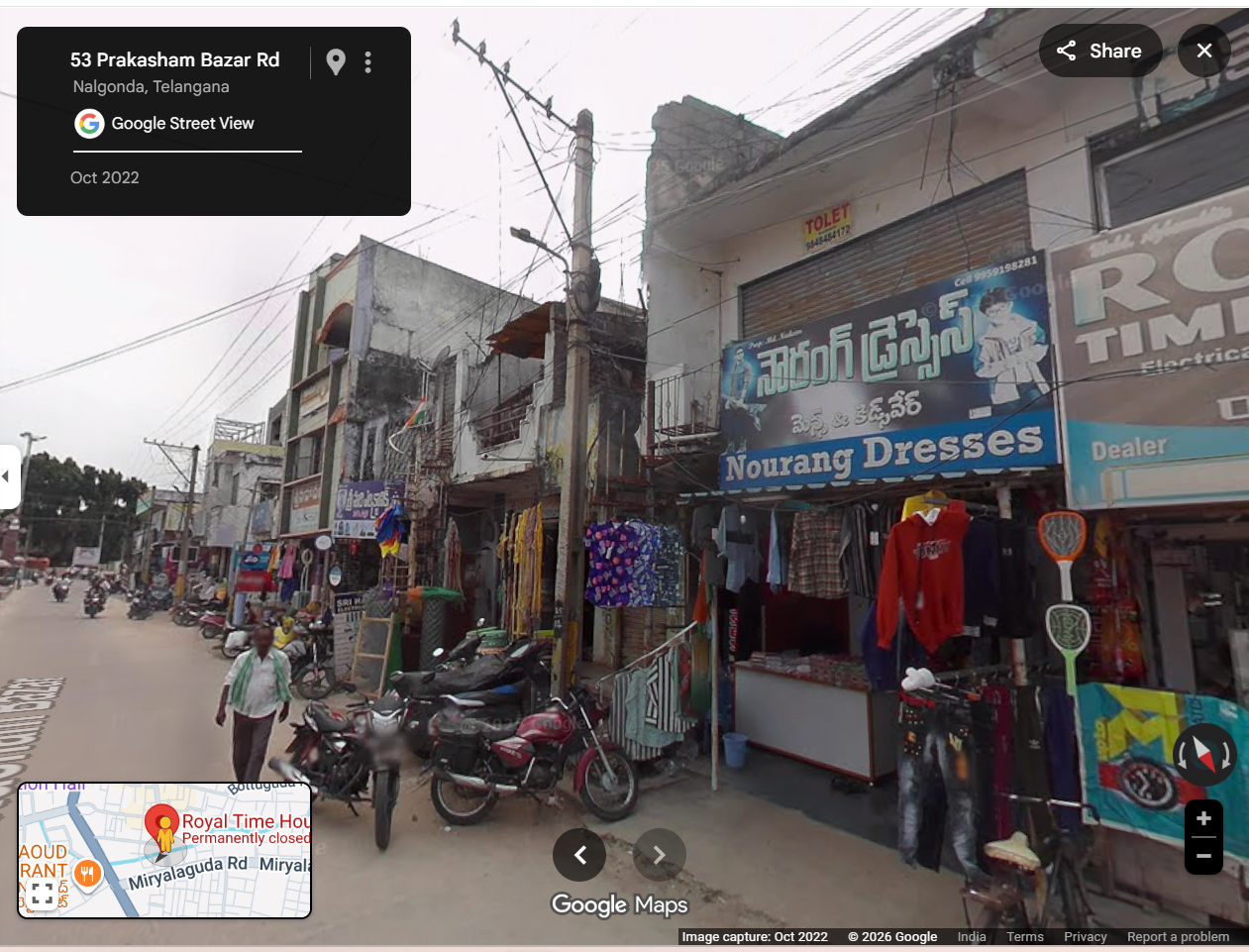
To confirm the location, the video was examined closely. A shop sign reading “Royal Time House” was visible in the footage. Using Google Street View, the same shop was located in Nalgonda, Telangana, conclusively establishing that the video was filmed there and not in Uttar Pradesh.
Conclusion
CyberPeace research confirmed that the viral video is from 2022 and was recorded in Telangana, not Uttar Pradesh. The clip is being falsely circulated with a misleading claim to give it a communal and political angle.
.webp)
Introduction
As per the National Crime Records Bureau (NCRB) ‘Cyber Crime In India Report 2022’, A total of 65,893 cases were registered under Cyber Crimes, showing an increase of 24.4% in registration in comparison to 52,974 cases registered in 2021. The crime rate increased from 3.9 in 2021 to 4.8 in 2022. During 2022, 64.8% of cyber-crime cases registered were for the motive of fraud (42,710 out of 65,893 cases), followed by Extortion with 5.5% (3,648 cases) and Sexual Exploitation with 5.2% (3,434 cases). The statistics released by NCRB show the increased rate of cyber crimes in the country, which poses a significant question of safety in the online world. The rise in cybercrime indicates a rise in emerging criminal groups with malicious intentions, creating new cybercrime hotspots in the country where these groups target and commit cyber crimes despite limited resources.
Cyber Crime Hotspots
Police have recently arrested several cyber criminals in a specific region, indicating that certain areas have become hotspots for cybercrime. Mewat region is one such hotspot indicating a growing trend of cybercrime operating from this area. The Mewat gang's modus operandi is quite different; Cybercriminals in Mewat scam mobile owners just using smartphones and SIM cards without kingpins and targeting mobile owners. The scammers also lure people through online marketplaces such as OLX, in which they pretend to sell possessions and then either physically lure victims to pick-up locations or scam them virtually.
A study conducted by Future Crime Research Foundation and IIT Kanpur in 2023 has revealed that Jamatara city, once considered the cyber crime capital of India, is no longer the epicentre. The study found that 35 hotspots in India are actively involved in cybercrime activities. The top 10 cybercrime hotspots in India collectively account for 80% of cybercrime-related cases in India. These districts are strategically located near India's capital or closer to the National Capital Region (NCR). These districts are strategically placed with multiple borders, making them easy targets for criminals.
Online financial fraud and social media-related crimes are the most common in India. Cybercriminals exploit data as a gold mine, using it to commit crimes. For instance, they can obtain banking and insurance data, use simple AI tools to cheat victims, and they can easily impersonate identities to lure innocent people. In cybercrime hotspots, sextortion is a modern way for cybercriminals to record and demand money. Loan app fraud, OLX fraud, and job fraud also originate from these specific regions.
Recommendations
To counter the challenges posed by emerging cybercrime hubs, the following recommendations are to be considered:
- Advanced threat Intelligence: The digital landscape is evolving, and the threat landscape is becoming more complex. AI's role in cybersecurity is becoming increasingly critical, both positively and negatively, as it helps in understanding and addressing advanced threats. AI is capable of proactive threat hunting, real-time anomaly detection, and swift incident response.
- Enhancing capabilities of Law Enforcement Agencies: Law enforcement agencies must be sensitised to advanced tools or techniques to investigate cyber crime cases effectively. The development and implementation of advanced forensic tools and technologies need to be utilised or implemented to keep up with the evolving tactics of cybercrime perpetrators.
- Continuous Monitoring: Continuous cybersecurity monitoring is crucial for detecting anomalies and preventing cyber-attacks. It involves analysing systems and data to establish baseline security, identify deviations, and investigate potential threats. Cybersecurity experts use data observability tools, artificial intelligence, and machine learning to detect unexpected dataset changes.
- Cyber Security Awareness: Public awareness needs to be higher. Cybercrime prevention and cybersecurity is a shared responsibility of all of us by being aware of the threats and following the best practices. The frequent interaction between law enforcement and the public is necessary to raise awareness about safeguarding personal and financial information. Effective campaigns on cyber security are necessary to educate netizens.
Safety Tips for Netizens
Install up-to-date security software and firewalls on devices, use strong passwords for accounts, and regularly update software and applications. Be cautious when clicking on links or downloading files from unknown sources, and be cautious of your personal information.
Conclusion
The rise of Cyber Crime Hotspots in specific regions or districts has significantly exacerbated the issue of increasing cybercrime rates. In order to combat cybercrime more effectively, it is necessary for law enforcement agencies to strengthen their coordination between different states and to adapt advanced technology methods to counter cybercrime threats effectively. Moreover, educating netizens about cyber crime threats and providing best practices is an effective method to counter these threats, considered the first line of defense against cybercrime.
References
- https://ncrb.gov.in/uploads/nationalcrimerecordsbureau/custom/1701607577CrimeinIndia2022Book1.pdf
- https://economictimes.indiatimes.com/tech/technology/no-kingpins-just-a-smartphone-and-sim-card-how-cybercriminals-in-mewat-scam-mobile-owners/articleshow/98062889.cms?from=mdr
- https://www.futurecrime.org/fcrf-cyber-crime-survey-2023
- https://timesofindia.indiatimes.com/city/mumbai/jamtara-loses-crown-as-new-remote-districts-rewrite-indias-cybercrime-map/articleshow/104475868.cms?from=mdr
- https://government.economictimes.indiatimes.com/news/secure-india/80-of-cyber-crimes-from-10-new-districts-iit-report/103921338
- https://www.dw.com/en/how-mewat-became-indias-new-hub-for-cyber-criminals/video-68674527
- https://www.indiatoday.in/from-india-today-magazine/story/into-cybercrime-hotspot-india-mewat-rajasthan-haryana-uttar-pradesh-2381545-2023-05-19
- https://frontline.thehindu.com/the-nation/spotlight-how-nuh-district-in-haryana-became-a-breeding-ground-for-cybercriminals/article67098193.ece
- https://www.opindia.com/2024/04/nuh-mewat-cyber-crime-haryana-police-crackdown/#google_vignette


