#FactCheck: Fake Claim that US has used Indian Airspace to attack Iran
Executive Summary:
An online claim alleging that U.S. bombers used Indian airspace to strike Iran has been widely circulated, particularly on Pakistani social media. However, official briefings from the U.S. Department of Defense and visuals shared by the Pentagon confirm that the bombers flew over Lebanon, Syria, and Iraq. Indian authorities have also refuted the claim, and the Press Information Bureau (PIB) has issued a fact-check dismissing it as false. The available evidence clearly indicates that Indian airspace was not involved in the operation.
Claim:
Various Pakistani social media users [archived here and here] have alleged that U.S. bombers used Indian airspace to carry out airstrikes on Iran. One widely circulated post claimed, “CONFIRMED: Indian airspace was used by U.S. forces to strike Iran. New Delhi’s quiet complicity now places it on the wrong side of history. Iran will not forget.”

Fact Check:
Contrary to viral social media claims, official details from U.S. authorities confirm that American B2 bombers used a Middle Eastern flight path specifically flying over Lebanon, Syria, and Iraq to reach Iran during Operation Midnight Hammer.

The Pentagon released visuals and unclassified briefings showing this route, with Joint Chiefs of Staff Chair Gen. Dan Caine explained that the bombers coordinated with support aircraft over the Middle East in a highly synchronized operation.

Additionally, Indian authorities have denied any involvement, and India’s Press Information Bureau (PIB) issued a fact-check debunking the false narrative that Indian airspace was used.

Conclusion:
In conclusion, official U.S. briefings and visuals confirm that B-2 bombers flew over the Middle East not India to strike Iran. Both the Pentagon and Indian authorities have denied any use of Indian airspace, and the Press Information Bureau has labeled the viral claims as false.
- Claim: Fake Claim that US has used Indian Airspace to attack Iran
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

Introduction
To combat the problem of annoying calls and SMS, telecom regulator TRAI has urged service providers to create a uniform digital platform in two months that will allow them to request, maintain, and withdraw customers’ approval for promotional calls and messages. In the initial stage, only subscribers will be able to initiate the process of registering their consent to receive promotional calls and SMS, and later, business entities will be able to contact customers to seek their consent to receive promotional messages, according to a statement issued by the Telecom Regulatory Authority of India (TRAI) on Saturday.
TRAI Directs Telecom Providers to Set Up Digital Platform
TRAI has now directed all access providers to develop and deploy the Digital Consent Acquisition (DCA) facility for creating a unified platform and process to digitally register customers’ consent across all service providers and principal entities. Consent is received and maintained under the current system by several key entities such as banks, other financial institutions, insurance firms, trading companies, business entities, real estate businesses, and so on.
The purpose, scope of consent, and the principal entity or brand name shall be clearly mentioned in the consent-seeking message sent over the short code,” according to the statement.
It stated that only approved online or app links, call-back numbers, and so on will be permitted to be used in consent-seeking communications.
TRAI issued guidelines to guarantee that all voice-based Telemarketers are brought under a single Distributed ledger technology (DLT) platform for more efficient monitoring of nuisance calls and unwanted communications. It also instructs operators to actively deploy AI/ML-based anti-phishing systems as well as to integrate tech solutions on the DLT platform to deal with malicious calls and texts.
TRAI has issued two separate Directions to Access Service Providers under TCCCPR-2018 (Telecom Commercial Communications Customer Preference Regulations) to ensure that all promotional messages are sent through Registered Telemarketers (RTMs) using approved Headers and Message Templates on Distributed Ledger Technologies (DLT) platform, and to stop misuse of Headers and Message Templates,” the regulator said in a statement.
Users can already block telemarketing calls and texts by texting 1909 from their registered mobile number. By dialing 1909, customers can opt out of getting advertising calls by activating the do not disturb (DND) feature.

Telecom providers operate DLT platforms, and businesses involved in sending bulk promotional or transactional SMS must register by providing their company information, including sender IDs and SMS templates.
According to the instructions, telecom companies will send consent-seeking messages using the common short code 127. The goal, extent of consent, and primary entity/brand name must be clearly stated in the consent-seeking message delivered via the shortcode.
TRAI stated that only whitelisted URLs/APKs (Android package kits file format)/OTT links/call back numbers, etc., shall be used in consent-seeking messages.
Telcos must “ensure that promotional messages are not transmitted by unregistered telemarketers or telemarketers using telephone numbers (10 digits numbers).” Telecom providers have been urged to act against all erring telemarketers in accordance with the applicable regulations and legal requirements.
Users can, however, refuse to receive any consent-seeking messages launched by any significant Telcos have been urged to create an SMS/IVR (interactive voice response)/online service for this purpose.
According to TRAI’s timeline, the consent-taking process by primary companies will begin on September 1.According to a nationwide survey conducted by a local circle, 66% of mobile users continue to receive three or more bothersome calls per day, the majority of which originate from personal cell numbers.
There are scams surfacing on the internet with new types of scams, like WhatsApp international call scams. The latest scam is targeting Delhi police, the scammers pretend to be police officials of Delhi and ask for the personal details of the users and the calling them from a 9-digit number.
A recent scam
A Twitter user reported receiving an automated call from +91 96681 9555, stating, “This call is from Delhi Police.” It went on to ask her to stay in the queue since some of her documents needed to be picked up. Then he said he is a sub-inspector at New Delhi’s Kirti Nagar police station. He then questioned if she had lately misplaced her Aadhaar card, PAN card, or ATM card, to which she replied ‘no’. The fraudster then claims to be a cop and asks her to validate the final four digits of her card because they have discovered a card with her name on it. And so many other people tweeted about this.
The scams are constantly increasing as earlier these scammers asked for account details and claimed to be Delhi police and used 9-digit numbers for scamming people.
TRAI’s new guidelines regarding the consent to receive any promotional calls and messages to telecommunication providers will be able to curb the scams.
The e- KYC is an essential requirement as e-KYC offers a more secure identity verification process in an increasingly digital age that uses biometric technologies to provide quick results.

Conclusion
The aim is to prevent unwanted calls and communications sent to customers via digital methods without their permission. Once this platform is implemented, an organization can only send promotional calls or messages with the customer’s explicit approval. Companies use a variety of methods to notify clients about their products, including phone calls, text messages, emails, and social media. Customers, however, are constantly assaulted with the same calls and messages as a result of this practice. With the constant increase in scams, the new guideline of TRAI will also curb the calling of Scams. digital KYC prevents SIM fraud and offers a more secure identity verification method.
.webp)
Executive Summary
The U.S. Department of Justice recently released nearly three million pages of documents, along with thousands of videos and photographs, related to its research into convicted offender Jeffrey Epstein. Meanwhile, a video showing a massive crowd protesting on a street is going viral on social media The video, which had earlier circulated with false claims linking it to anti-government protests in Iran, is now being shared by several users who claim that the protest took place in the United States after the release of the Epstein files. Research by CyberPeace found the viral claim to be false. The video being linked to protests in the United States following the release of the Epstein files is not real and was generated using artificial intelligence (AI).
Claim:
An Instagram user uploaded the viral video on February 9, 2026, with the caption: “After Epstein files released in America. All eyes on America.”
- https://www.instagram.com/reel/DUjLe-XE5lA
- https://ghostarchive.org/archive/tkP6W
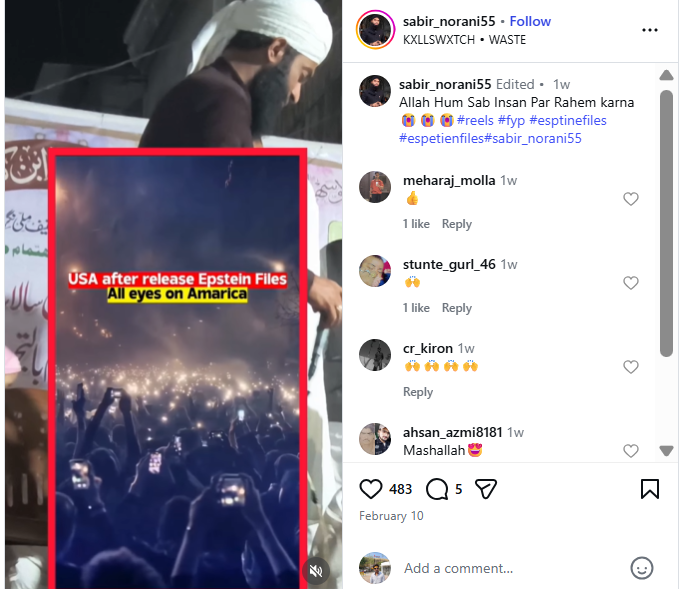
Fact Check:
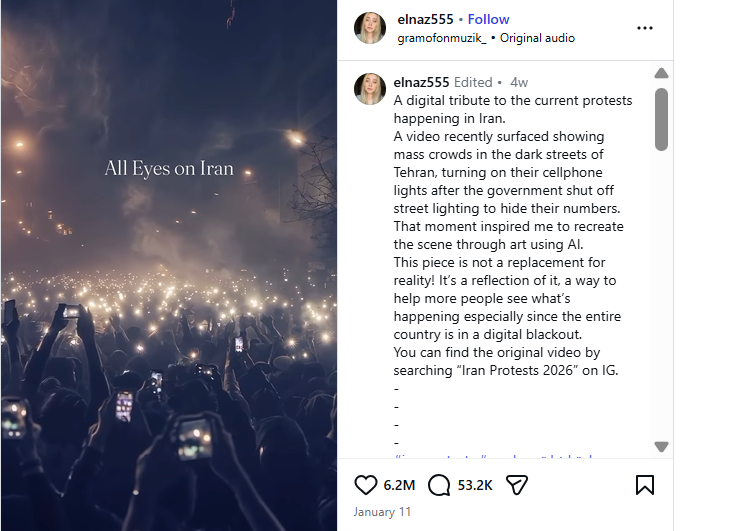
To verify the claim, we first conducted a reverse search of the viral video using Google Lens. The same video was found posted on January 10, 2026, by an Instagram account named “elnaz555,” where it was shared in the context of recent protests in Iran. The post also mentioned that the video was created using AI.
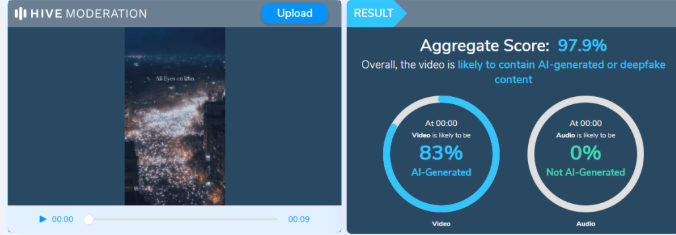
Based on this lead, we further analyzed a higher-quality version of the viral video using Hive Moderation, a tool used to detect AI-generated images and videos. The analysis indicated a 97.9% probability that the video was generated using artificial intelligence. The research clearly shows that the video is not authentic and has been falsely linked to protests in the United States after the release of the Epstein files.
Conclusion:
The claim circulating on social media is false. The viral video allegedly showing protests in the United States following the release of the Epstein files is AI-generated and not related to any real event.

Digital vulnerabilities like cyber-attacks and data breaches proliferate rapidly in the hyper-connected world that is created today. These vulnerabilities can compromise sensitive data like personal information, financial data, and intellectual property and can potentially threaten businesses of all sizes and in all sectors. Hence, it has become important to inform all stakeholders about any breach or attack to ensure they can be well-prepared for the consequences of such an incident.
The non-reporting of reporting can result in heavy fines in many parts of the world. Data breaches caused by malicious acts are crimes and need proper investigation. Organisations may face significant penalties for failing to report the event. Failing to report data breach incidents can result in huge financial setbacks and legal complications. To understand why transparency is vital and understanding the regulatory framework that governs data breaches is the first step.
The Current Indian Regulatory Framework on Data Breach Disclosure
A data breach essentially, is the unauthorised processing or accidental disclosure of personal data, which may occur through its acquisition, sharing, use, alteration, destruction, or loss of access. Such incidents can compromise the affected data’s confidentiality, integrity, or availability. In India, the Information Technology Act of 2000 and the Digital Personal Data Protection Act of 2023 are the primary legislation that tackles cybercrimes like data breaches.
- Under the DPDP Act, neither materiality thresholds nor express timelines have been prescribed for the reporting requirement. Data Fiduciaries are required to report incidents of personal data breach, regardless of their sensitivity or impact on the Data Principal.
- The IT (Indian Computer Emergency Response Team and Manner of Performing Functions and Duties) Rules, 2013, the IT (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011, along with the Cyber Security Directions, under section 70B(6) of the IT Act, 2000, relating to information security practices, procedure, prevention, response and reporting of cyber incidents for Safe & Trusted Internet prescribed in 2022 impose mandatory notification requirements on service providers, intermediaries, data centres and corporate entities, upon the occurrence of certain cybersecurity incidents.
- These laws and regulations obligate companies to report any breach and any incident to regulators such as the CERT-In and the Data Protection Board.
The Consequences of Non-Disclosure
A non-disclosure of a data breach has a manifold of consequences. They are as follows:
- Legal and financial penalties are the immediate consequence of a data breach in India. The DPDP Act prescribes a fine of up to Rs 250 Crore from the affected parties, along with suits of a civil nature and regulatory scrutiny. Non-compliance can also attract action from CERT-In, leading to more reputational damage.
- In the long term, failure to disclose data breaches can erode customer trust as they are less likely to engage with a brand that is deemed unreliable. Investor confidence may potentially waver due to concerns about governance and security, leading to stock price drops or reduced funding opportunities. Brand reputation can be significantly tarnished, and companies may struggle with retaining and attracting customers and employees. This can affect long-term profitability and growth.
- Companies such as BigBasket and Jio in 2020 and Haldiram in 2022 have suffered from data breaches recently. Poor transparency and delay in disclosures led to significant reputational damage, legal scrutiny, and regulatory actions for the companies.
Measures for Improvement: Building Corporate Reputation via Transparency
Transparency is critical when disclosing data breaches. It enhances trust and loyalty for a company when the priority is data privacy for stakeholders. Ensuring transparency mitigates backlash. It demonstrates a company’s willingness to cooperate with authorities. A farsighted approach instils confidence in all stakeholders in showcasing a company's resilience and commitment to governance. These measures can be further improved upon by:
- Offering actionable steps for companies to establish robust data breach policies, including regular audits, prompt notifications, and clear communication strategies.
- Highlighting the importance of cooperation with regulatory bodies and how to ensure compliance with the DPDP Act and other relevant laws.
- Sharing best public communications practices post-breach to manage reputational and legal risks.
Conclusion
Maintaining transparency when a data breach happens is more than a legal obligation. It is a good strategy to retain a corporate reputation. Companies can mitigate the potential risks (legal, financial and reputational) by informing stakeholders and cooperating with regulatory bodies proactively. In an era where digital vulnerabilities are ever-present, clear communication and compliance with data protection laws such as the DPDP Act build trust, enhance corporate governance, and secure long-term business success. Proactive measures, including audits, breach policies, and effective public communication, are critical in reinforcing resilience and fostering stakeholder confidence in the face of cyber threats.
References
- https://www.meity.gov.in/writereaddata/files/Digital%20Personal%20Data%20Protection%20Act%202023.pdf
- https://www.cert-in.org.in/PDF/CERT-In_Directions_70B_28.04.2022.pdf
- https://chawdamrunal.medium.com/the-dark-side-of-covering-up-data-breaches-why-transparency-is-crucial-fe9ed10aac27
- https://www.dlapiperdataprotection.com/index.html?t=breach-notification&c=IN


