#FactCheck -Social Media Claim of ICC’s One-Year Ban on Pakistan Cricket Is Misleading
Executive Summary:
A purported media release allegedly issued in the name of the International Cricket Council (ICC) is being widely circulated on social media. The release claims that the ICC has decided to impose a one-year ban on Pakistan cricket. CyberPeace’s research found this claim to be false.The research revealed that the media release circulating on social media is fake, and no such letter or official statement has been issued by the ICC.
Claim:
On social media platform X (formerly Twitter), a user shared the viral letter on February 3, 2026, claiming that an ICC meeting was held in which board members voted on issues related to Pakistan. The post alleged that 14 out of 16 votes were cast in favour of the BCCI. The user further claimed that Pakistan’s share of ICC revenue would be reduced and that Pakistan might be asked to compensate for losses incurred by the ICC.
The viral letter, written in English, stated that matters related to Pakistan were discussed in an ICC meeting and that a 14–2 majority vote led to the decision to impose a one-year ban on Pakistan cricket. It further claimed that the Pakistan Super League (PSL) would be suspended for one year, Pakistan’s annual revenue share would be reduced from 5.75 percent to 2.25 percent, and Pakistan would not be allowed to host any ICC tournaments until 2040. The letter also claimed that these decisions were taken to safeguard the integrity and spirit of the game. Links to the viral post, archive link, and screenshots can be seen below.

Fact Check:
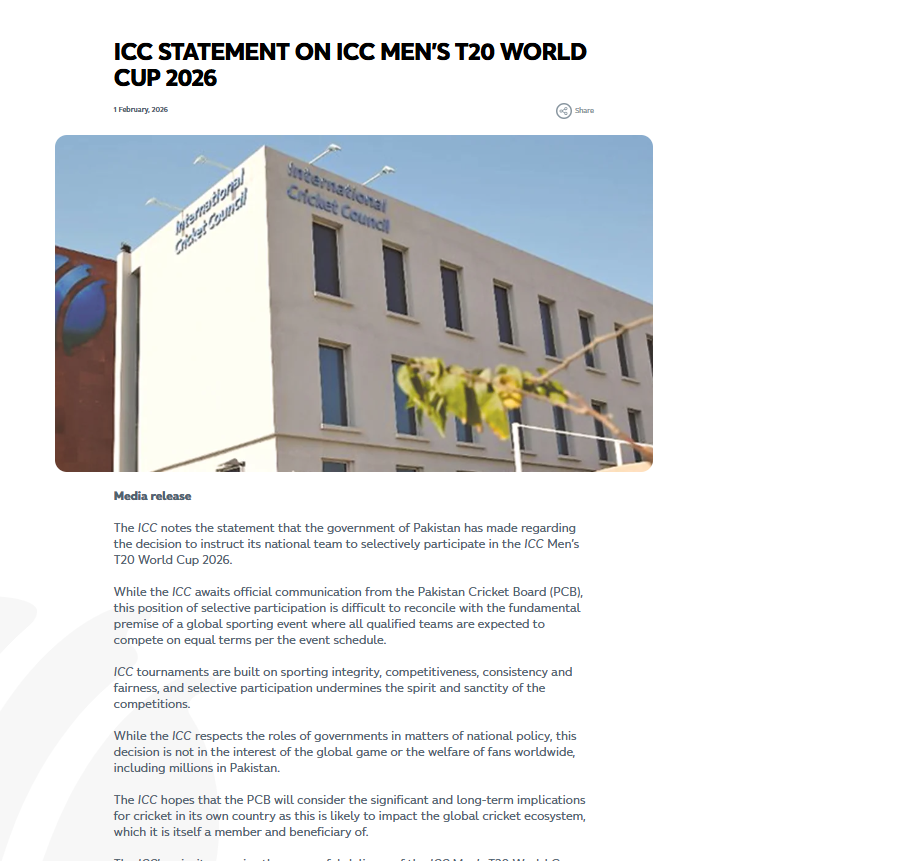
To verify the viral claim, CyberPeace conducted a Google search using relevant keywords. However, no credible or reliable media reports supporting the claim were found. In the next step of the research , an official press release uploaded on DD Sports’ Facebook page on February 2, 2026, was found. The press release responded to Pakistan’s decision not to play against India in a Group A match. The DD Sports statement said that the Pakistan Cricket Board should consider the long-term and serious implications of such a decision, as it could impact the global cricket ecosystem—of which Pakistan is itself a member and beneficiary.

Notably, the official press release made no mention of any ban on Pakistan cricket, reduction in revenue share, suspension of the PSL, or restrictions on hosting ICC tournaments, contrary to the claims made in the viral letter. Further, the same official statement was found published on the ICC’s website on February 1, 2026. This release also did not mention any decision related to banning Pakistan cricket or barring the country from hosting ICC tournaments for the next 40 years.
Conclusion
CyberPeace concludes that the media release circulating on social media is fake. The ICC has not issued any official letter or statement announcing a one-year ban on Pakistan cricket, revenue cuts, or restrictions on hosting ICC tournaments.









.webp)





