#FactCheck - Digitally Altered Image Falsely Shows World Bank President Ajay Banga Holding Khalistani Flag
Executive Summary
A digitally manipulated image of World Bank President Ajay Banga has been circulating on social media, falsely portraying him as holding a Khalistani flag. The image was shared by a Pakistan-based X (formerly Twitter) user, who also incorrectly identified Banga as the President of the International Monetary Fund (IMF), thereby fuelling misleading speculation that he supports the Khalistani movement against India.
The Claim
On February 5, an X user with the handle @syedAnas0101010 posted an image allegedly showing Ajay Banga holding a Khalistani flag. The user misidentified him as the IMF President and captioned the post, “IMF president sending signals to INDIA.” The post quickly gained traction, amplifying false narratives and political speculation. Here is the link and archive link to the post, along with a screenshot:
Fact Check:
To verify the authenticity of the image, the CyberPeace Fact Check Desk conducted a detailed research . The image was first subjected to a reverse image search using Google Lens, which led to a Reuters news report published on June 13, 2023. The original photograph, captured by Reuters photojournalist Jonathan Ernst, showed Ajay Banga arriving at the World Bank headquarters in Washington, D.C., on June 2, 2023, marking his first day in office. In the authentic image, Banga is seen holding a coffee cup, not a flag.
Further analysis confirmed that the viral image had been digitally altered to replace the coffee cup with a Khalistani flag, thereby misrepresenting the context and intent of the original photograph. Here is the link to the report, along with a screenshot.
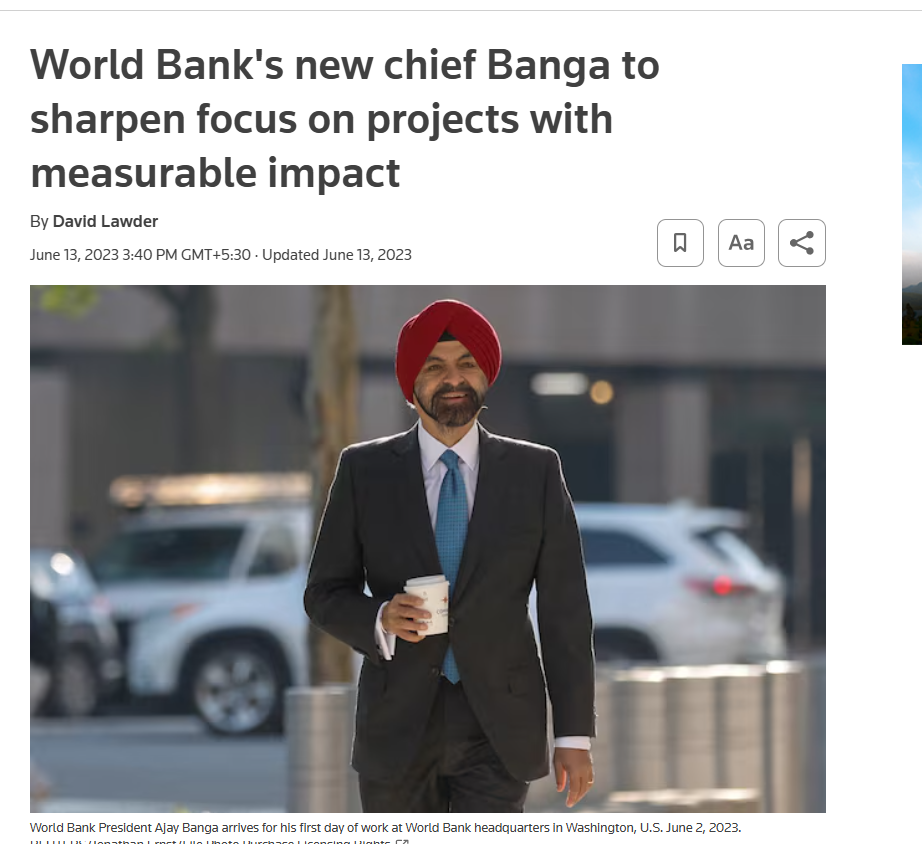
To strengthen the findings, the altered image was also analysed using the Hive Moderation AI detection tool. The tool’s assessment indicated a high likelihood that the image contained AI-generated or manipulated elements, reinforcing the conclusion that the image was not genuine. Below is a screenshot of the result.
Conclusion
The viral image claiming to show World Bank President Ajay Banga holding a Khalistani flag is fake. The photograph was digitally manipulated to spread misinformation and provoke political speculation. In reality, the original Reuters image from June 2023 shows Banga holding a coffee cup during his arrival at the World Bank headquarters. The claim that he supports the Khalistani movement is false and misleading.
Related Blogs
.webp)
Introduction:
The Federal Bureau of Investigation (FBI) focuses on threats and is an intelligence-driven agency with both law enforcement and intelligence responsibilities. The FBI has the power and duty to look into certain offences that are entrusted to it and to offer other law enforcement agencies cooperation services including fingerprint identification, lab tests, and training. In order to support its own investigations as well as those of its collaborators and to better comprehend and address the security dangers facing the United States, the FBI also gathers, disseminates, and analyzes intelligence.
The FBI’s Internet Crime Complaint Center (IC3) Functions combating cybercrime:
- Collection: Internet crime victims can report incidents and notify the relevant authorities of potential illicit Internet behavior using the IC3. Law enforcement frequently advises and directs victims to use www.ic3.gov to submit a complaint.
- Analysis: To find new dangers and trends, the IC3 examines and examines data that users submit via its website.
- Public Awareness: The website posts public service announcements, business alerts, and other publications outlining specific frauds. Helps to raise awareness and make people become aware of Internet crimes and how to stay protected.
- Referrals: The IC3 compiles relevant complaints to create referrals, which are sent to national, international, local, and state law enforcement agencies for possible investigation. If law enforcement conducts an investigation and finds evidence of a crime, the offender may face legal repercussions.
Alarming increase in cyber crime cases:
In the recently released 2022 Internet Crime Report by the FBI's Internet Crime Complaint Center (IC3), the statistics paint a concerning picture of cybercrime in the United States. FBI’s Internet Crime Complaint Center (IC3) received 39,416 cases of extortion in 2022. The number of cases in 2021 stood at 39,360.
FBI officials emphasize the growing scope and sophistication of cyber-enabled crimes, which come from around the world. They highlight the importance of reporting incidents to IC3 and stress the role of law enforcement and private-sector partnerships.
About Internet Crime Complaint Center IC3:
IC3 was established in May 2000 by the FBI to receive complaints related to internet crimes.
It has received over 7.3 million complaints since its inception, averaging around 651,800 complaints per year over the last five years. IC3's mission is to provide the public with a reliable reporting mechanism for suspected cyber-enabled criminal activity and to collaborate with law enforcement and industry partners.
The FBI encourages the public to regularly review consumer and industry alerts published by IC3. An victim of an internet crime are urged to submit a complaint to IC3, and can also file a complaint on behalf of another person. These statistics underscore the ever-evolving and expanding threat of cybercrime and the importance of vigilance and reporting to combat this growing challenge.
What is sextortion?
The use or threatened use of a sexual image or video of another person without that person’s consent, derived from online encounters or social media websites or applications, primarily to extort money from that person or asking for sexual favours and giving warning to distribute that picture or video to that person’s friends, acquaintances, spouse, partner, or co-workers or in public domain.
Sextortion is an online crime that can be understood as, when an bad actor coerces a young person into creating or sharing a sexual image or video of themselves and then uses it to get something from such young person, such as other sexual images, money, or even sexual favours. Reports highlights that more and more kids are being blackmailed in this way. Sextortion can also happen to adults. Sextortion can also take place by taking your pictures from social media account and converting those pictures into sexually explicit content by morphing such images or creating deepfake by miusing deepfake technologies.
Sextortion in the age of AI and advanced technologies:
AI and deep fake technology make sextortion even more dangerous and pernicious. A perpetrator can now produce a high-quality deep fake that convincingly shows a victim engaged in explicit acts — even if the person has not done any such thing.
Legal Measures available in cases of sextortion:
In India, cybersecurity is governed primarily by the Indian Penal Code (IPC) and the Information Technology Act, 2000 (IT Act). Addressing cyber crimes such as hacking, identity theft, and the publication of obscene material online, sextortion and other cyber crimes. The IT Act covers various aspects of electronic governance and e-commerce, with providing provisions for defining such offences and providing punishment for such offences.
Recently Digital Personal Data Protection Act, 2023 has been enacted by the Indian Government to protect the digital personal data of the Individuals. These laws collectively establish the legal framework for cybersecurity and cybercrime prevention in India. Victims are urged to report the crime to local law enforcement and its cybercrime divisions. Law enforcement will investigate sextortion cases reports and will undertake appropriate legal action.
How to stay protected from evolving cases of sextortion: Best Practices:
- Report the Crime to law enforcement agency and social media platform or Internet service provider.
- Enable Two-step verification as an extra layer of protection.
- Keep your laptop Webcams covered when not in use.
- Stay protected from malware and phishing Attacks.
- Protect your personal information on your social media account, and also monitor your social media accounts in order to identify any suspicious activity. You can also set and review privacy settings of your social media accounts.
Conclusion:
Sextortion cases has been increased in recent time. Knowing the risk, being aware of rules and regulations, and by following best practices will help in preventing such crime and help you to stay safe and also avoid the chance of being victimized. It is important to spreading awareness about such growing cyber crimes and empowering the people to report it and it is also significant to provide support to victims. Let’s all unite in order to fight against such cyber crimes and also to make life a safer place on the internet or digital space.
References:
- https://www.ic3.gov/Media/PDF/AnnualReport/2022_IC3ElderFraudReport.pdf
- https://octillolaw.com/insights/fbi-ic3-releases-2022-internet-crime-report/
- https://www.iafci.org/app_themes/docs/Federal%20Agency/2022_IC3Report.pdf
Executive Summary:
New Linux malware has been discovered by a cybersecurity firm Volexity, and this new strain of malware is being referred to as DISGOMOJI. A Pakistan-based threat actor alias ‘UTA0137’ has been identified as having espionage aims, with its primary focus on Indian government entities. Like other common forms of backdoors and botnets involved in different types of cyberattacks, DISGOMOJI, the malware allows the use of commands to capture screenshots, search for files to steal, spread additional payloads, and transfer files. DISGOMOJI uses Discord (messaging service) for Command & Control (C2) and uses emojis for C2 communication. This malware targets Linux operating systems.
The DISCOMOJI Malware:
- The DISGOMOJI malware opens a specific channel in a Discord server and every new channel corresponds to a new victim. This means that the attacker can communicate with the victim one at a time.
- This particular malware connects with the attacker-controlled Discord server using Emoji, a form of relay protocol. The attacker provides unique emojis as instructions, and the malware uses emojis as a feedback to the subsequent command status.
- For instance, the ‘camera with flash’ emoji is used to screenshots the device of the victim or to steal, the ‘fox’ emoji cracks all Firefox profiles, and the ‘skull’ emoji kills the malware process.
- This C2 communication is done using emojis to ensure messaging between infected contacts, and it is almost impossible for Discord to shut down the malware as it can always change the account details of Discord it is using once the maliciou server is blocked.
- The malware also has capabilities aside from the emoji-based C2 such as network probing, tunneling, and data theft that are needed to help the UTA0137 threat actor in achieving its espionage goals.
Specific emojis used for different commands by UTA0137:
- Camera with Flash (📸): Captures a picture of the target device’s screen as per the victim’s directions.
- Backhand Index Pointing Down (👇): Extracts files from the targeted device and sends them to the command channel in the form of attachments.
- Backhand Index Pointing Right (👉): This process involves sending a file found on the victim’s device to another web-hosted file storage service known as Oshi or oshi[. ]at.
- Backhand Index Pointing Left (👈): Sends a file from the victim’s device to transfer[. ]sh, which is an online service for sharing files on the Internet.
- Fire (🔥): Finds and transmits all files with certain extensions that exist on the victim’s device, such as *. txt, *. doc, *. xls, *. pdf, *. ppt, *. rtf, *. log, *. cfg, *. dat, *. db, *. mdb, *. odb, *. sql, *. json, *. xml, *. php, *. asp, *. pl, *. sh, *. py, *. ino, *. cpp, *. java,
- Fox (🦊): This works by compressing all Firefox related profiles in the affected device.
- Skull (💀): Kills the malware process in windows using ‘os. Exit()’
- Man Running (🏃♂️): Execute a command on a victim’s device. This command receives an argument, which is the command to execute.
- Index Pointing up (👆) : Upload a file to the victim's device. The file to upload is attached along with this emoji
Analysis:
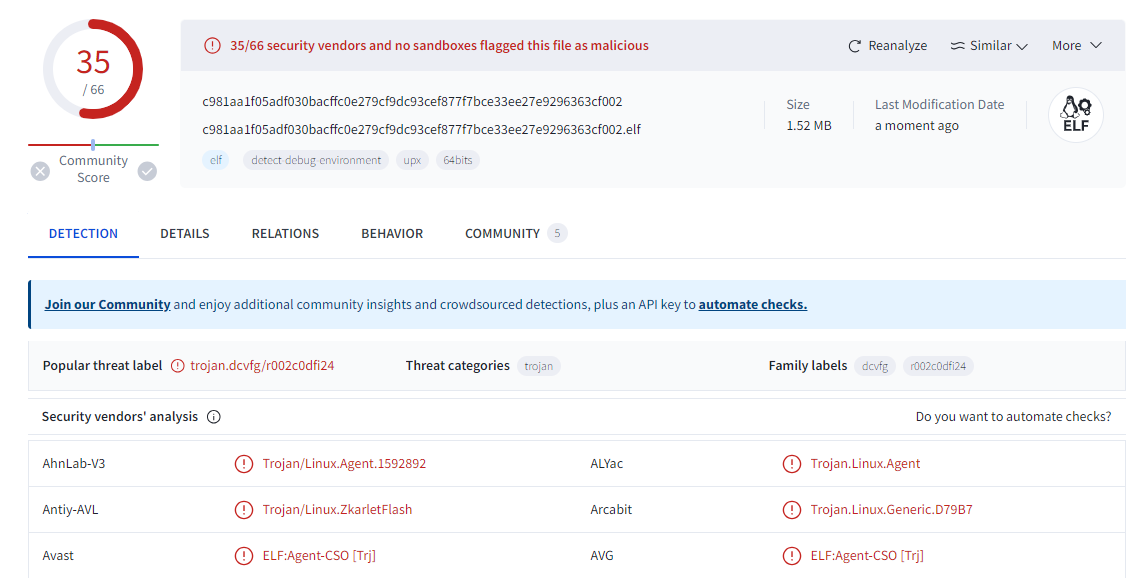
The analysis was carried out for one of the indicator of compromised SHA-256 hash file- C981aa1f05adf030bacffc0e279cf9dc93cef877f7bce33ee27e9296363cf002.
It is found that most of the vendors have marked the file as trojan in virustotal and the graph explains the malicious nature of the contacted domains and IPs.
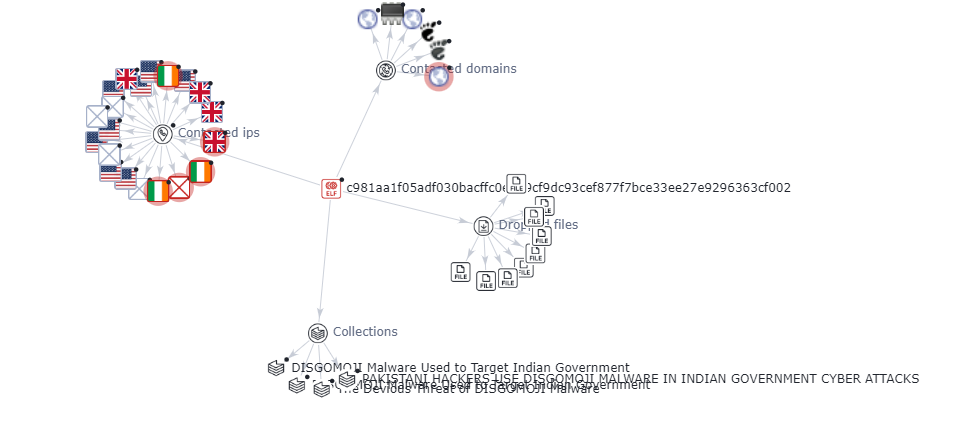
Discord & C2 Communication for UTA0137:
- Stealthiness: Discord is a well-known messaging platform used for different purposes, which means that sending any messages or files on the server should not attract suspicion. Such stealthiness makes it possible for UTA0137 to remain dormant for greater periods before launching an attack.
- Customization: UTA0137 connected to Discord is able to create specific channels for distinct victims on the server. Such a framework allows the attackers to communicate with each of the victims individually to make a process more accurate and efficient.
- Emoji-based protocol: For C2 communication, emojis really complicates the attempt that Discord might make to interfere with the operations of the malware. In case the malicious server gets banned, malware could easily be recovered, especially by using the Discord credentials from the C2 server.
- Persistence: The malware, as stated above, has the ability to perpetually exist to hack the system and withstand rebooting of systems so that the virus can continue to operate without being detected by the owner of the hacked system.
- Advanced capabilities: Other features of DISGOMOJI are the Network Map using Nmap scanner, network tunneling through Chisel and Ligolo and Data Exfiltration by File Sharing services. These capabilities thus help in aiding the espionage goals of UTA0137.
- Social engineering: The virus and the trojan can show the pop-up windows and prompt messages, for example the fake update for firefox and similar applications, where the user can be tricked into inputting the password.
- Dynamic credential fetching: The malware does not write the hardcoded values of the credentials in order to connect it to the discord server. This also inconveniences analysts as they are unable to easily locate the position of the C2 server.
- Bogus informational and error messages: They never show any real information or errors because they do not want one to decipher the malicious behavior easily.
Recommendations to mitigate the risk of UTA0137:
- Regularly Update Software and Firmware: It is essential to regularly update all the application software and firmware of different devices, particularly, routers, to prevent hackers from exploiting the discovered and disclosed flaws. This includes fixing bugs such as CVE-2024-3080 and CVE-2024-3912 on ASUS routers, which basically entails solving a set of problems.
- Implement Multi-Factor Authentication: There are statistics that show how often user accounts are attacked, it is important to incorporate multi-factor authentication to further secure the accounts.
- Deploy Advanced Malware Protection: Provide robust guard that will help the user recognize and prevent the execution of the DISGOMOJI malware and similar threats.
- Enhance Network Segmentation: Utilize stringent network isolation mechanisms that seek to compartmentalize the key systems and data from the rest of the network in order to minimize the attack exposure.
- Monitor Network Activity: Scanning Network hour to hour for identifying and handling the security breach and the tools such as Nmap, Chisel, Ligolo etc can be used.
- Utilize Threat Intelligence: To leverage advanced threats intelligence which will help you acquire knowledge on previous threats and vulnerabilities and take informed actions.
- Secure Communication Channels: Mitigate the problem of the leakage of developers’ credentials and ways of engaging with the discord through loss of contact to prevent abusing attacks or gaining control over Discord as an attack vector.
- Enforce Access Control: Regularly review and update the user authentication processes by adopting stricter access control measures that will allow only the right personnel to access the right systems and information.
- Conduct Regular Security Audits: It is important to engage in security audits periodically in an effort to check some of the weaknesses present within the network or systems.
- Implement Incident Response Plan: Conduct a risk assessment, based on that design and establish an efficient incident response kit that helps in the early identification, isolation, and management of security breaches.
- Educate Users: Educate users on cybersecurity hygiene, opportunities to strengthen affinity with the University, and conduct retraining on threats like phishing and social engineering.
Conclusion:
The new threat actor named UTA0137 from Pakistan who was utilizing DISGOMOJI malware to attack Indian government institutions using embedded emojis with a command line through the Discord app was discovered by Volexity. It has the capability to exfiltrate and aims to steal the data of government entities. The UTA0137 was continuously improved over time to permanently communicate with victims. It underlines the necessity of having strong protection from viruses and hacker attacks, using secure passwords and unique codes every time, updating the software more often and having high-level anti-malware tools. Organizations can minimize advanced threats, the likes of DISGOMOJI and protect sensitive data by improving network segmentation, continuous monitoring of activities, and users’ awareness.
References:
https://otx.alienvault.com/pulse/66712446e23b1d14e4f293eb
https://thehackernews.com/2024/06/pakistani-hackers-use-disgomoji-malware.html?m=1
https://cybernews.com/news/hackers-using-emojis-to-command-malware/
https://www.volexity.com/blog/2024/06/13/disgomoji-malware-used-to-target-indian-government/

Technology has revolutionized our lives, offering countless benefits and conveniences that make our daily lives more accessible and connected. However, with these benefits come potential challenges and risks that can impact our digital experiences. In this article, we have gathered expert advice on the impact of technology use in our daily lives, including the importance of warranties and tech protection in safeguarding our technology investments. Our experts offer invaluable insights and guidance on using technology safely and effectively while protecting us from unexpected costs or problems. Whether you’re a casual user or a technology enthusiast, our experts’ insights will help you navigate the world of technology with confidence and peace of mind.
How to protect kids from online abuse in the modern era of technology?
“As parents, it’s important to acknowledge that online child abuse is a widespread problem that we need to address. But does this mean we should ban technology from our children’s lives? Absolutely not! Technology is an integral part of our children’s lives, providing numerous benefits. Instead, we should think of practical ways to minimize the risks of online abuse. Many parents today depend on parental control apps like Mobicip to safeguard their children’s online activities and build healthy digital habits. These apps allow parents to supervise their child’s online behavior, restrict screen time, prevent access to certain websites and applications, filter inappropriate content, and get instant notifications about dangerous interactions or inappropriate content. Parents feel reassured and free of worry, knowing that their children’s online surroundings are secure and protected. In addition to using a parental control app, we must also focus on building a strong connection with our kids. By initiating conversations about their digital lives, we can understand their digital world, educate them about the potential risks and dangers of the internet, and teach them how to stay safe. By being proactive and engaged in our children’s digital lives, we can protect them from online abuse while still allowing them to benefit from technology.”
How to increase engagement in online classes via technology?
“Online classes have gained immense popularity in recent years due to their many advantages. However, online educators face several challenges that can impede the effectiveness of their classes, one of which is the lack of engagement from students. To address this challenge, it is crucial to adopt certain strategies that can increase student engagement and create a more meaningful learning environment.
One effective strategy is to limit the number of chokepoints that students may face while enrolling in a class. This can be achieved by using booking and scheduling technology that provides students with a hassle-free experience. The system sends regular reminders and notifications to learners about upcoming classes and assignments, helping them stay organized and committed to their learning.
Technology plays a vital role in improving communication between students and teachers and in increasing student engagement and participation during a session. Utilizing technology such as polling, chat boxes, and breakout rooms enables learners to actively participate in the class and share their perspectives, leading to more effective learning.
Personalization is also essential in creating a meaningful learning environment. A scheduling system can help create customized learning paths for each student, where they can progress at their own pace and focus on topics that interest them. This ensures that each student receives individual attention and is able to learn in a way that suits their learning style.
Moreover, gamification techniques can be used to make the learning process more fun and engaging. This includes using badges, points, and leaderboards to motivate learners to achieve their goals while competing with each other.”
Dr. Sukanya Kakoty, Omnify
How to choose the best due diligence software for your business?
“With a variety of solutions on the market, finding the best due diligence software for your business can be a tedious task. In addition to the software’s capabilities meeting your needs, there are other factors to consider when picking the right solution for your business. As due diligence involves the sharing of sensitive information, security is a key factor to consider. When browsing solutions, it is important to consider if their security features are up to industry standards. User-friendliness is another factor to consider when adopting a new due diligence software. Introducing a new tool should increase team efficiency, not disrupt your existing workflow. When searching for the perfect due diligence solution, pick one that meets the above criteria and more. DealRoom is a lifecycle deal management solution, providing pipeline, diligence, integration, and document management all under one platform. DealRoom’s user-friendly and intuitive features allow for customizable workflows to fit the specific needs of each user. DealRoom also offers industry-leading security features, including data encryption, granular permissions, and detailed audit logs, guaranteeing that your information is always protected. When choosing the best due diligence software for your business, consider a user-friendly, flexible, and secure solution.”
Why are backups important, and what is the safest way of doing them?
“Backups are important for several reasons. They help to protect against data loss, which can be caused by a variety of reasons, such as hardware failure, software corruption, natural disasters, or cyber-attacks. Backups also help to ensure that important data is available when needed, such as in the case of an emergency or system failure. Additionally, backups provide a way to recover deleted or corrupted files. This is also important because the loss of data can result in consequences such as financial loss, damage to reputation, and even legal issues. If not these, then loss of data may also lead to emotional effects in certain cases. A backup, however, can restore data quickly and avoid any significant disruption, emotional or otherwise. The safest way of doing backups is by following the 3-2-1 backup rule. This rule states that you should have at least three copies of your data, stored on at least two different storage media, with one copy stored offsite. This provides redundancy in case of a failure of one storage medium or location.
There are several methods of backing up data, including:
- External hard drives or USB drives: These are inexpensive and portable, making them a popular choice for personal backups. However, they can be lost or damaged, so it is important to keep them in a safe location and make regular backups.
- Cloud backups: These store data on remote servers, which can be accessed from anywhere with an internet connection. This provides an offsite backup solution, but it is important to choose a reputable provider and to ensure that the data is encrypted and secure.
- Network-attached storage (NAS): These are devices that connect to a network and provide centralized storage for multiple devices. They can be configured to automatically back up data from multiple devices on the network.
- Tape backups: These are less common but are still used by some businesses for the long-term storage of large amounts of data.
Regardless of the backup method chosen, it is important to regularly test backups regularly to ensure that they can be successfully restored in case of an emergency.”
What are the best trending electric toys for kids in 2023?
“Augmented Reality (AR) Toys: These toys blend the physical and digital world, providing an immersive experience. Popular examples include AR-enabled building sets and interactive storybooks that come to life through an app.
Educational Robotics: Robotics toys like the LEGO Mindstorms Robot Inventor and Sphero’s programmable robots have gained popularity for teaching coding, engineering, and problem-solving skills through hands-on play.”
Aside from security, what are some of the features of a VPN?
“Accessing geo-restricted content: One of the main benefits of using a VPN is its ability to bypass geographical restrictions in the world of flight prices, content, gaming, and more. Many websites and online services are only available in certain countries or regions. With a VPN, you can change your virtual location and access content that is otherwise blocked or unavailable in your country. Imagine you’re playing a game with friends; by using a VPN, you can improve your gaming experience by connecting to a server closer to the game’s host location and bypassing regional restrictions to access features unavailable in your region.
Increased privacy and anonymity: While security and privacy go hand in hand, VPNs offer more than just encryption. They also provide a level of anonymity by masking your IP address and making it difficult for websites and online services to track your online activity. This can be particularly useful for users who are concerned about their online privacy or who want to avoid targeted ads.
Faster internet speeds: Believe it or not, using a VPN can actually improve your internet speed in certain situations. If your internet service provider (ISP) is throttling your internet speed, a VPN can help you bypass this by encrypting your traffic and hiding it from your ISP. Additionally, some VPN providers offer dedicated servers that are optimized for faster speeds, reducing buffering and improving download and upload speeds.”
How does creating a website can help a home business?
“As a digital marketing consultant, I once worked with a client who had a home-based bakery business. She struggled to reach new customers beyond her local community and wanted to expand her reach and grow her business. After assessing her needs, I recommended that she create a website for her business. With the website, she could showcase her unique baked goods, provide a platform for online ordering, and expand her reach to customers beyond her local community. The website was designed to be visually appealing and user-friendly while effectively showcasing the brand and products in an attractive way. Additionally, the website was optimized for search engines and integrated with social media platforms to increase visibility and drive traffic to the site. Within a few months of launching the website, she saw an increase in orders. Customers could easily place orders through the website and leave reviews, which provided social proof and helped build trust with potential customers. Also used data analytics to track customer behavior and make data-driven decisions to improve the website and marketing strategy. The website became a valuable asset for her business, helping her to expand her reach, increase sales, and gather valuable customer data. Overall, creating a website helped her home-based business to grow and thrive in a competitive marketplace.”
Lito James, MassivePeak.com
How can technology be utilized to enhance productivity for remote teams working from home?
“Our team facilitates strategic planning sessions and we’re frequently working with teams that are working remotely. Here are a few of our best tips for productivity:
- Clear strategy: As teams have fewer touch points, it’s critical they are aligned and bought into the direction of the organization.
- Clear big rocks for the week. Make sure you’re not just busy but doing things that will move the needle on your strategic goals
- Clear accountability: Basecamp or other project management tools to help make sure nothing falls through the cracks
- Clear communication: Schedule the right meetings, so you are connecting at the right times to deliver important work and align on important topics.
- Clear agendas: When you do meet, make sure you’re coming together, staying focused, and getting the most important information across
Creating the right strategy and the right structure to keep it moving forward will help your team drive your most important outcomes, regardless of if you’re working in an office or remotely.
Anthony Taylor, SME Strategy Consulting
How to monitor your kids’ activities online?
“As a father of two kids and the founder of TheSweetBits.com, a website dedicated to providing guides on software and apps, I have extensive experience in monitoring my children’s online activities. Over the years, I have tested and reviewed numerous parental control apps and software to ensure my children’s online safety. When it comes to monitoring your kids’ activity online, it’s crucial to find a balance between keeping them safe and respecting their privacy. One of the most effective ways to achieve this balance is by using parental control software that allows you to set limits on their device usage, restrict access to inappropriate content, and monitor their online activity. However, it’s important to note that parental control software is not a substitute for good communication with your kids. You should have regular conversations with them about online safety and the potential dangers of the internet. By establishing trust and open communication, you can work together to create a safe and responsible online environment for your family. As I always say, ‘Parental control software is just one tool in the toolbox of responsible parenting’.”
How to plan the best online date with the help of technology?
“To plan a date online with the help of technology, we recommend using a reservation app like OpenTable to make dinner reservations. Not only will this let her know you thought ahead with the smaller details, but it will also ensure a smooth date by eliminating a long waiting time for a table to open up.”
What are the benefits of teaching kids to code and how to make it fun?
“The ability to code has become increasingly important in the modern world due to the rapid advancement of technology and its integration into nearly every aspect of our lives. This is something that will only continue as our children grow up and enter the world at large as the demand for workers with coding skills continues to grow rapidly. Teaching kids to code offers numerous benefits beyond just developing technical skills and getting them future-ready. It promotes problem-solving abilities, critical thinking, and logical reasoning, all of which are essential in today’s digital age. Additionally, coding can increase creativity and encourage children to think outside the box. However, it’s important to make coding fun and engaging for kids rather than a dull and tedious task. One way to make it exciting is to introduce gamification elements, such as incorporating fun characters or adding game-like challenges, and there are loads of great apps to get them started with. We love CodeSpark Academy, Lego Boost, and Tynker. Another approach is to encourage group work or peer learning, where children can work together to solve problems and learn from each other. Ultimately, making coding fun and enjoyable can ignite children’s interest in technology and set them on a path to explore new and exciting opportunities in the future.”
Are dating apps useful in the modern dating era and how to find the correct one?
“Dating apps have become a popular tool for modern daters to find potential partners. However, they also come with their own set of problems. One of the biggest issues with current dating apps is that they focus too much on superficial factors such as sexual attraction, rather than deeper compatibility and true attraction. This can lead to frustration and disappointment for users who are seeking more meaningful connections. Fortunately, AI technology is starting to offer solutions to these problems. By using machine learning algorithms and data analysis, apps like Iris Dating are able to help users find potential matches based on more than just superficial qualities. Iris uses a process called “iris training” to learn each user’s unique preferences and suggest compatible matches accordingly. This approach allows users to connect with people to whom they are really attracted, leading to more meaningful and lasting relationships. When it comes to finding the right dating app, it’s important to do your research and choose one that aligns with your values and preferences. Look for apps that prioritize true attraction and use AI technology to help you find meaningful matches. Don’t be afraid to try out multiple apps until you find one that feels right for you. Overall, while dating apps have their flaws, AI-powered apps like Iris offer hope for a more personalized and meaningful dating experience. By leveraging the power of technology, we can make the search for love a little bit easier and a lot more enjoyable.”
What are some IT risk management tips for home businesses?
“As more and more people turn to home-based businesses, IT security for these operations is becoming an increasingly important concern. From data breaches to cyberattacks, the risks you face as a home business owner are the same as those faced by larger enterprises. So, what are some IT risk management tips for home businesses? First, consider using a virtual private network or VPN to enhance the security of your online communications. Additionally, enable two-factor authentication for all of your accounts, including any cloud services you use. Practice good password hygiene, regularly updating passwords and avoiding easily guessable or common passwords. Finally, consider investing in cybersecurity insurance to protect your business in the event of a cyberattack or data breach. By taking these steps to mitigate IT risks, you can help ensure your home business stays secure and successful. Below are some additional suggestions to help you stay vigilant and set up your home business for longevity.
-Keep Your Software Up to Date: One of the best ways to reduce your risk of being hacked is to keep your software up to date. This includes both your operating system and any applications you have installed.
-Use a Firewall: A firewall is a piece of software that helps to block incoming connections from untrusted sources. By blocking these connections, you can help to prevent hackers from gaining access to your system.
-Use Anti-Virus Software: In addition to using a firewall, you should also use anti-virus software. Anti-virus software helps to protect your system from viruses and other malware. These programs work by scanning your system for known threats and then quarantining or deleting any files that are found to be infected.
-Back Up Your Data Regularly: Finally, it is important to back up your data regularly. This way, if your system is ever compromised, you will not lose any important files or data.
-Encrypt Your Data: If you are storing sensitive data on your computer, it is important to encrypt it to protect it from being accessed by unauthorized individuals. Encryption is a process of transforming data into a format that cannot be read without a decryption key. There are many different encryption algorithms that you can use, so make sure to choose one that is appropriate for the type of data you are encrypting.”
What are the benefits of giving your child a smartphone?
“If you’re teetering back and forth on getting your child a smartphone, consider these benefits as you make your decision:
• Connection. Smartphones keep kids in contact with friends and family—for fun and function! From school to extracurricular activities, kids can easily let their parents and caregivers know about late pickups, ride requests, and other changes of plans.
• Safety. If your child or someone they’re with gets hurt, their smartphone could save a life! And with built-in GPS, their location is always accessible. Plus, parental controls and other smartphone safeguards offer even more protection.
• Convenience. Life is a little easier when your child has a smartphone, plain and simple! You can call each other, send texts, and always know where they are.
• Acceptance. These days, it’s uncommon for kids to not have smartphones. With a smartphone, your child feels belonging and inclusion among their peers.
• Development. Having something as valuable as a smartphone teaches children responsibility and accountability. And with a smartphone of their own, your child will learn how to use technology in an appropriate, safe, and disciplined way.
• Education. Smartphones are incredible teaching tools! Educational apps, videos, and games can keep kids sharp. Plus, smartphones can introduce them to new hobbies and interests!”
How is technology promoting health and wellness?
“Technology has revolutionized the healthcare industry and is playing an increasingly important role in promoting health and wellness. Here are some ways in which technology has helped:
Wearable technology: Wearable devices, such as fitness trackers and smartwatches, are becoming increasingly popular. These devices can track a person’s physical activity, sleep patterns, heart rate, and more. They provide valuable insights into a person’s health and wellness and can help motivate them to make positive lifestyle changes.
Telehealth: Telemedicine allows patients to receive medical care remotely through video conferencing, phone calls, or other digital means. It has also allowed fitness professionals to work with more people who aren’t in a local market via video conferencing, webinars, etc.
Mobile Apps: There are a plethora of mobile apps available that promote health and wellness. These apps can help users track their diet and exercise, manage chronic conditions, and access medical information.
Virtual Reality: Virtual reality (VR) is being used in healthcare to treat conditions such as anxiety, phobias, and PTSD. VR can also be used for physical therapy and rehabilitation.
Overall, technology is playing an increasingly important role in promoting health and wellness, and it is likely that we will see even more innovative uses of technology in the healthcare industry in the future.”


