#FactCheck - AI-Generated Video Falsely Shared as ‘Multi-Hooded Snake’ Sighting in Vrindavan
A video is being widely shared on social media showing devotees seated in a boat appearing stunned as a massive, multi-hooded snake—resembling the mythical Sheshnag—suddenly emerges from the middle of a water body.
The video captures visible panic and astonishment among the devotees. Social media users are sharing the clip claiming that it is from Vrindavan, with some portraying the sight as a divine or supernatural event. However, research conducted by the Cyber Peace Foundation found the viral claim to be false. Our research revealed that the video is not authentic and has been generated using artificial intelligence (AI).
Claim
On January 17, 2026, a user shared the viral video on Instagram with the caption suggesting that God had appeared again in the age of Kalyug. The post claims that a terrifying video from Vrindavan has surfaced in which devotees sitting in a boat were shocked to see a massive multi-hooded snake emerge from the water. The caption further states that devotees are hailing the creature as an incarnation of Sheshnag or Vasuki Nag, raising religious slogans and questioning whether the sight represents a divine sign. (The link to the post, its archive link, and screenshots are available.)
- https://www.instagram.com/reel/DTngN9FkoX0/?igsh=MTZvdTN1enI2NnFydA%3D%3D
- https://archive.ph/UuAqB
Fact Check:
Upon closely examining the viral video, we suspected that it might be AI-generated. To verify this, the video was scanned using the AI detection tool SIGHTENGINE, which indicated that the visual is 99 per cent AI-generated.
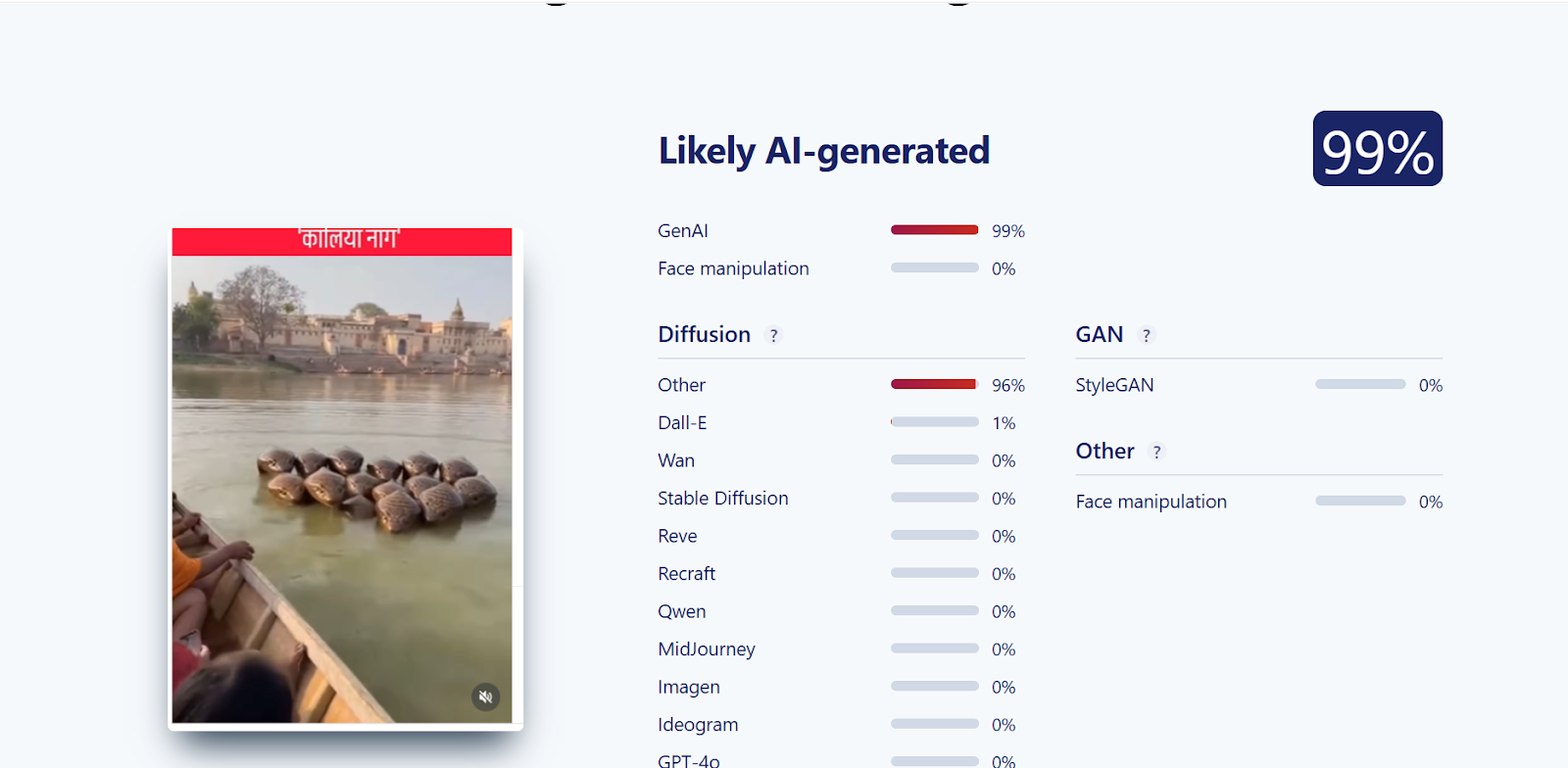
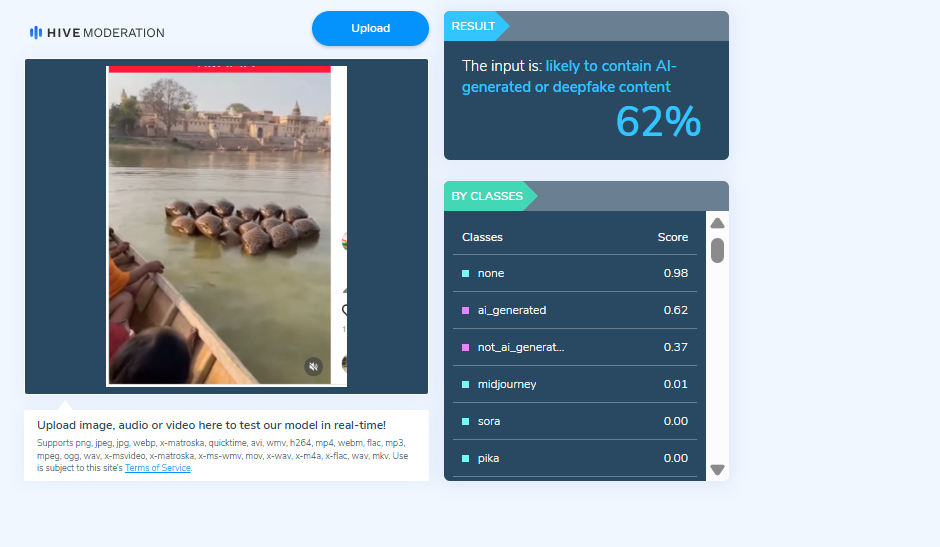
In the next step of the research , the video was analysed using another AI detection tool, HIVE Moderation. According to the results obtained, the video was found to be 62 per cent AI-generated.
Conclusion
Our research clearly establishes that the viral video claiming to show a multi-hooded snake in Vrindavan is not real. The clip has been created using artificial intelligence and is being falsely shared on social media with religious and sensational claims.
Related Blogs

Executive Summary:
Given that AI technologies are evolving at a fast pace in 2024, an AI-oriented phishing attack on a large Indian financial institution illustrated the threats. The documentation of the attack specifics involves the identification of attack techniques, ramifications to the institution, intervention conducted, and resultant effects. The case study also turns to the challenges connected with the development of better protection and sensibilisation of automatized threats.
Introduction
Due to the advancement in AI technology, its uses in cybercrimes across the world have emerged significant in financial institutions. In this report a serious incident that happened in early 2024 is analysed, according to which a leading Indian bank was hit by a highly complex, highly intelligent AI-supported phishing operation. Attack made use of AI’s innate characteristic of data analysis and data persuasion which led into a severe compromise of the bank’s internal structures.
Background
The chosen financial institution, one of the largest banks in India, had a good background regarding the extremity of its cybersecurity policies. However, these global cyberattacks opened up new threats that AI-based methods posed that earlier forms of security could not entirely counter efficiently. The attackers concentrated on the top managers of the bank because it is evident that controlling such persons gives the option of entering the inner systems as well as financial information.
Attack Execution
The attackers utilised AI in sending the messages that were an exact look alike of internal messages sent between employees. From Facebook and Twitter content, blog entries, and lastly, LinkedIn connection history and email tenor of the bank’s executives, the AI used to create these emails was highly specific. Some of these emails possessed official formatting, specific internal language, and the CEO’s writing; this made them very realistic.
It also used that link in phishing emails that led the users to a pseudo internal portal in an attempt to obtain the login credentials. Due to sophistication, the targeted individuals thought the received emails were genuine, and entered their log in details easily to the bank’s network, thus allowing the attackers access.
Impact
It caused quite an impact to the bank in every aspect. Numerous executives of the company lost their passwords to the fake emails and compromised several financial databases with information from customer accounts and transactions. The break-in permitted the criminals to cease a number of the financial’s internet services hence disrupting its functions and those of its customers for a number of days.
They also suffered a devastating blow to their customer trust because the breach revealed the bank’s weakness against contemporary cyber threats. Apart from managing the immediate operations which dealt with mitigating the breach, the financial institution was also toppling a long-term reputational hit.
Technical Analysis and Findings
1. The AI techniques that are used in generation of the phishing emails are as follows:
- The attack used powerful NLP technology, which was most probably developed using the large-scaled transformer, such as GPT (Generative Pre-trained Transformer). Since these models are learned from large data samples they used the examples of the conversation pieces from social networks, emails and PC language to create quite credible emails.
Key Technical Features:
- Contextual Understanding: The AI was able to take into account the nature of prior interactions and thus write follow up emails that were perfectly in line with prior discourse.
- Style Mimicry: The AI replicated the writing of the CEO given the emails of the CEO and then extrapolated from the data given such elements as the tone, the language, and the format of the signature line.
- Adaptive Learning: The AI actively adapted from the mistakes, and feedback to tweak the generated emails for other tries and this made it difficult to detect.
2. Sophisticated Spear-Phishing Techniques
Unlike ordinary phishing scams, this attack was phishing using spear-phishing where the attackers would directly target specific people using emails. The AI used social engineering techniques that significantly increased the chances of certain individuals replying to certain emails based on algorithms which machine learning furnished.
Key Technical Features:
- Targeted Data Harvesting: Cyborgs found out the employees of the organisation and targeted messages via the public profiles and messengers were scraped.
- Behavioural Analysis: The latest behaviour pattern concerning the users of the social networking sites and other online platforms were used by the AI to forecast the courses of action expected to be taken by the end users such as clicking on the links or opening of the attachments.
- Real-Time Adjustments: These are times when it was determined that the response to the phishing email was necessary and the use of AI adjusted the consequent emails’ timing and content.
3. Advanced Evasion Techniques
The attackers were able to pull off this attack by leveraging AI in their evasion from the normal filters placed in emails. These techniques therefore entailed a modification of the contents of the emails in a manner that would not be easily detected by the spam filters while at the same time preserving the content of the message.
Key Technical Features:
- Dynamic Content Alteration: The AI merely changed the different aspects of the email message slightly to develop several versions of the phishing email that would compromise different algorithms.
- Polymorphic Attacks: In this case, polymorphic code was used in the phishing attack which implies that the actual payloads of the links changed frequently, which means that it was difficult for the AV tools to block them as they were perceived as threats.
- Phantom Domains: Another tactic employed was that of using AI in generating and disseminating phantom domains, that are actual web sites that appear to be legitimate but are in fact short lived specially created for this phishing attack, adding to the difficulty of detection.
4. Exploitation of Human Vulnerabilities
This kind of attack’s success was not only in AI but also in the vulnerability of people, trust in familiar language and the tendency to obey authorities.
Key Technical Features:
- Social Engineering: As for the second factor, AI determined specific psychological principles that should be used in order to maximise the chance of the targeted recipients opening the phishing emails, namely the principles of urgency and familiarity.
- Multi-Layered Deception: The AI was successfully able to have a two tiered approach of the emails being sent as once the targeted individuals opened the first mail, later the second one by pretext of being a follow up by a genuine company/personality.
Response
On sighting the breach, the bank’s cybersecurity personnel spring into action to try and limit the fallout. They reported the matter to the Indian Computer Emergency Response Team (CERT-In) to find who originated the attack and how to block any other intrusion. The bank also immediately started taking measures to strengthen its security a bit further, for instance, in filtering emails, and increasing the authentication procedures.
Knowing the risks, the bank realised that actions should be taken in order to enhance the cybersecurity level and implement a new wide-scale cybersecurity awareness program. This programme consisted of increasing the awareness of employees about possible AI-phishing in the organisation’s info space and the necessity of checking the sender’s identity beforehand.
Outcome
Despite the fact and evidence that this bank was able to regain its functionality after the attack without critical impacts with regards to its operations, the following issues were raised. Some of the losses that the financial institution reported include losses in form of compensation of the affected customers and costs of implementing measures to enhance the financial institution’s cybersecurity. However, the principle of the incident was significantly critical of the bank as customers and shareholders began to doubt the organisation’s capacity to safeguard information in the modern digital era of advanced artificial intelligence cyber threats.
This case depicts the importance for the financial firms to align their security plan in a way that fights the new security threats. The attack is also a message to other organisations in that they are not immune from such analysis attacks with AI and should take proper measures against such threats.
Conclusion
The recent AI-phishing attack on an Indian bank in 2024 is one of the indicators of potential modern attackers’ capabilities. Since the AI technology is still progressing, so are the advances of the cyberattacks. Financial institutions and several other organisations can only go as far as adopting adequate AI-aware cybersecurity solutions for their systems and data.
Moreover, this case raises awareness of how important it is to train the employees to be properly prepared to avoid the successful cyberattacks. The organisation’s cybersecurity awareness and secure employee behaviours, as well as practices that enable them to understand and report any likely artificial intelligence offences, helps the organisation to minimise risks from any AI attack.
Recommendations
- Enhanced AI-Based Defences: Financial institutions should employ AI-driven detection and response products that are capable of mitigating AI-operation-based cyber threats in real-time.
- Employee Training Programs: CYBER SECURITY: All employees should undergo frequent cybersecurity awareness training; here they should be trained on how to identify AI-populated phishing.
- Stricter Authentication Protocols: For more specific accounts, ID and other security procedures should be tight in order to get into sensitive ones.
- Collaboration with CERT-In: Continued engagement and coordination with authorities such as the Indian Computer Emergency Response Team (CERT-In) and other equivalents to constantly monitor new threats and valid recommendations.
- Public Communication Strategies: It is also important to establish effective communication plans to address the customers of the organisations and ensure that they remain trusted even when an organisation is facing a cyber threat.
Through implementing these, financial institutions have an opportunity for being ready with new threats that come with AI and cyber terrorism on essential financial assets in today’s complex IT environments.

Introduction
The Telecom Regulatory Authority of India (TRAI) has directed all telcos to set up detection systems based on Artificial Intelligence and Machine Learning (AI/ML) technologies in order to identify and control spam calls and text messages from unregistered telemarketers (UTMs).
The TRAI Directed telcos
The telecom regulator, TRAI, has directed all Access Providers to detect Unsolicited commercial communication (UCC)by systems, which is based on Artificial Intelligence and Machine Learning to detect, identify, and act against senders of Commercial Communication who are not registered in accordance with the provisions of the Telecom Commercial Communication Customer Preference Regulations, 2018 (TCCCPR-2018). Unregistered Telemarketers (UTMs) are entities that do not register with Access Providers and use 10-digit mobile numbers to send commercial communications via SMS or calls.
TRAI steps to curb Unsolicited commercial communication
TRAI has taken several initiatives to reduce Unsolicited Commercial Communication (UCC), which is a major source of annoyance for the public. It has resulted in fewer complaints filed against Registered Telemarketers (RTMs). Despite the TSPs’ efforts, UCC from Unregistered Telemarketers (UTMs) continues. Sometimes, these UTMs use messages with bogus URLs and phone numbers to trick clients into revealing crucial information, leading to financial loss.
To detect, identify, and prosecute all Unregistered Telemarketers (UTMs), the TRAI has mandated that Access Service Providers implement the UCC.
Detect the System with the necessary functionalities within the TRAI’s Telecom Commercial Communication Customer Preference Regulations, 2018 framework.
Access service providers have implemented such detection systems based on their applicability and practicality. However, because UTMs are constantly creating new strategies for sending unwanted communications, the present UCC detection systems provided by Access Service providers cannot detect such UCC.
TRAI also Directs Telecom Providers to Set Up Digital Platform for Customer Consent to Curb Promotional Calls and Messages.
Unregistered Telemarketers (UTMs) sometimes use messages with fake URLs and phone numbers to trick customers into revealing essential information, resulting in financial loss.

TRAI has urged businesses like banks, insurance companies, financial institutions, and others to re-verify their SMS content templates with telcos within two weeks. It also directed telecom companies to stop misusing commercial messaging templates within the next 45 days.
The telecom regulator has also instructed operators to limit the number of variables in a content template to three. However, if any business intends to utilise more than three variables in a content template for communicating with their users, this should be permitted only after examining the example message, as well as adequate justifications and justification.
In order to ensure consistency in UCC Detect System implementations, TRAI has directed all Access Providers to deploy UCC and detect systems based on artificial intelligence and Machine Learning that are capable of constantly evolving to deal with new signatures, patterns, and techniques used by UTMs.
Access Providers have also been directed to use the DLT platform to share intelligence with others. Access Providers have also been asked to ensure that such UCC Detect System detects senders that send unsolicited commercial communications in bulk and do not comply with the requirements. All Access Providers are directed to follow the instructions and provide an update on actions done within thirty days.
The move by TRAI is to curb the menacing calls as due to this, the number of scam cases is increasing, and now a new trend of scams started as recently, a Twitter user reported receiving an automated call from +91 96681 9555 with the message “This call is from Delhi Police.” It then asked her to stay in the queue since some of her documents needed to be picked up. Then he said he works as a sub-inspector at the Kirti Nagar police station in New Delhi. He then inquired whether she had recently misplaced her Aadhaar card, PAN card, or ATM card, to which she replied ‘no’. The scammer then poses as a cop and requests that she authenticate the last four digits of her card because they have found a card with her name on it. And a lot of other people tweeted about it.

Conclusion
TRAI directed the telcos to check the calls and messages from Unregistered numbers. This step of TRAI will curb the pesky calls and messages and catch the Frauds who are not registered with the regulation. Sometimes the unregistered sender sends fraudulent links, and through these fraudulent calls and messages, the sender tries to take the personal information of the customers, which results in financial losses.

Introduction
Digital Public Infrastructure (DPI) serves as the backbone of e-governance, enabling governments to deliver services more efficiently, transparently, and inclusively. By leveraging information and communication technology (ICT), digital governance systems reconfigure traditional administrative processes, making them more accessible and citizen-centric. However, the successful implementation of such systems hinges on overcoming several challenges, from ensuring data security to fostering digital literacy and addressing infrastructural gaps.
This article delves into the key enablers that drive effective DPI and outlines the measures already undertaken by the government to enhance its functionality. Furthermore, it outlines strategies for their enhancement, emphasizing the need for a collaborative, secure, and adaptive approach to building robust e-governance systems.
Key Enablers of DPI
Digital Public Infrastructure (DPI), the foundation for e-governance, relies on common design, robust governance, and private sector participation for efficiency and inclusivity. This requires common principles, frameworks for collaboration, capacity building, and the development of common standards. Some of the key measures undertaken by the government in this regard include:
- Data Protection Framework: The Digital Personal Data Protection (DPDP) Act of 2023 establishes a framework to ensure consent-based data sharing and regulate the processing of digital personal data. It delineates the responsibilities of data fiduciaries in safeguarding users' digital personal data.
- Increasing Public-Private Partnerships: Refining collaboration between the government and the private sector has accelerated the development, maintenance, expansion, and trust of the infrastructure of DPIs, such as the AADHAR, UPI, and Data Empowerment and Protection Architecture (DEPA). For example, the Asian Development Bank attributes the success of UPI to its “consortium ownership structure”, which enables the wide participation of major financial stakeholders in the country.
- Coordinated Planning: The PM-Gati Shakti establishes a clear coordination framework involving various inter-governmental stakeholders at the state and union levels. This aims to significantly reduce project duplications, delays, and cost escalations by streamlining communication, harmonizing project appraisal and approval processes, and providing a comprehensive database of major infrastructure projects in the country. This database called the National Master Plan, is jointly accessible by various government stakeholders through APIs.
- Capacity Building for Government Employees: The National e-Governance Division of the Ministry of Electronics and Information Technology routinely rolls out multiple training programs to build the technological and managerial skills required by government employees to manage Digital Public Goods (DPGs). For instance, it recently held a program on “Managing Large Digital Transformative Projects”. Additionally, the Ministry of Personnel, Public Grievances, and Pensions has launched the Integrated Government Online Training platform (iGOT) Karmayogi for the continuous learning of civil servants across various domains.
Digital Governance; Way Forward
E-governance utilizes information and communication technology (ICT) such as Wide Area Networks, the Internet, and mobile computing to implement existing government activities, reconfiguring the structures and processes of governance systems. This warrants addressing certain inter-related challenges such as :
- Data Security: The dynamic and ever-changing landscape of cyber threats necessitates regular advancements in data and information security technologies, policy frameworks, and legal provisions. Consequently, the digital public ecosystem must incorporate robust data cybersecurity measures, advanced encryption technologies, and stringent privacy compliance standards to safeguard against data breaches.
- Creating Feedback Loops: Regular feedback surveys will help government agencies improve the quality, efficiency, and accessibility of digital governance services by tailoring them to be more user-friendly and enhancing administrative design. This is necessary to build trust in government services and improve their uptake among beneficiaries. Conducting the decennial census is essential to gather updated data that can serve as a foundation for more informed and effective decision-making.
- Capacity Building for End-Users: The beneficiaries of key e-governance projects like Aadhar and UPI may have inadequate technological skills, especially in regions with weak internet network infrastructure like hilly or rural areas. This can present challenges in the access to and usage of technological solutions. Robust capacity-building campaigns for beneficiaries can provide an impetus to the digital inclusion efforts of the government.
- Increasing the Availability of Real-Time Data: By prioritizing the availability of up-to-date information, governments and third-party enterprises can enable quick and informed decision-making. They can effectively track service usage, assess quality, and monitor key metrics by leveraging real-time data. This approach is essential for enhancing operational efficiency and delivering improved user experience.
- Resistance to Change: Any resistance among beneficiaries or government employees to adopt digital governance goods may stem from a limited understanding of digital processes and a lack of experience with transitioning from legacy systems. Hand-holding employees during the transitionary phase can help create more trust in the process and strengthen the new systems.
Conclusion
Digital governance is crucial to transforming public services, ensuring transparency, and fostering inclusivity in a rapidly digitizing world. The successful implementation of such projects requires addressing challenges like data security, skill gaps, infrastructural limitations, feedback mechanisms, and resistance to change. Addressing these challenges with a strategic, multi-stakeholder approach can ensure the successful execution and long-term impact of large digital governance projects. By adopting robust cybersecurity frameworks, fostering public-private partnerships, and emphasizing capacity building, governments can create efficient and resilient systems that are user-centric, secure, and accessible to all.
References
- https://www.adb.org/sites/default/files/publication/865106/adbi-wp1363.pdf
- https://www.jotform.com/blog/government-digital-transformation-challenges/
- https://aapti.in/wp-content/uploads/2024/06/AaptixONI-DPIGovernancePlaybook_compressed.pdf
- https://community.nasscom.in/sites/default/files/publicreport/Digital%20Public%20Infrastructure%2022-2-2024_compressed.pdf
- https://proteantech.in/articles/Decoding-Digital-Public-Infrastructure-in-India/


