#FactCheck: Viral video of Unrest in Kenya is being falsely linked with J&K
Executive Summary:
A video of people throwing rocks at vehicles is being shared widely on social media, claiming an incident of unrest in Jammu and Kashmir, India. However, our thorough research has revealed that the video is not from India, but from a protest in Kenya on 25 June 2025. Therefore, the video is misattributed and shared out of context to promote false information.

Claim:
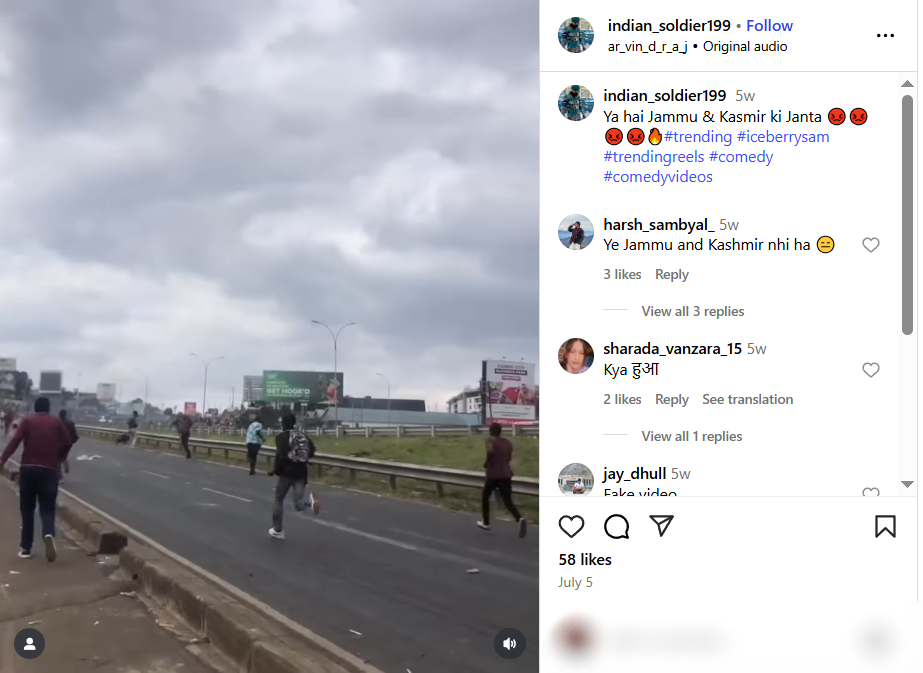
The viral video shows people hurling stones at army or police vehicles and is claimed to be from Jammu and Kashmir, implying ongoing unrest and anti-government sentiment in the region.
Fact Check:
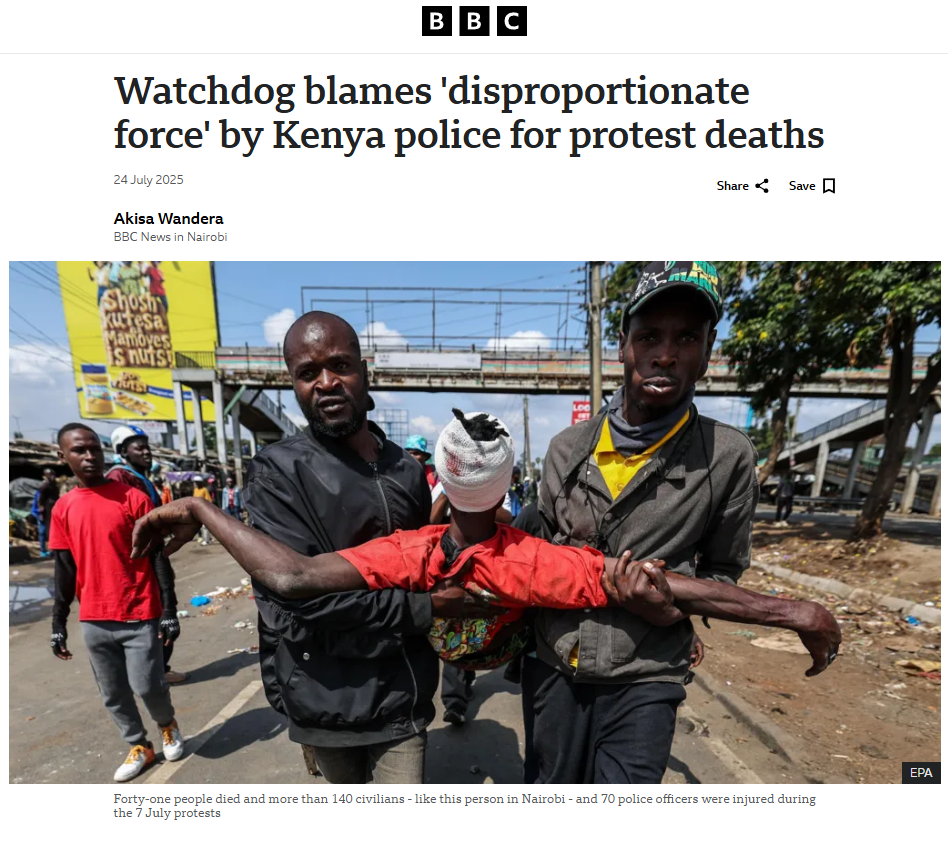
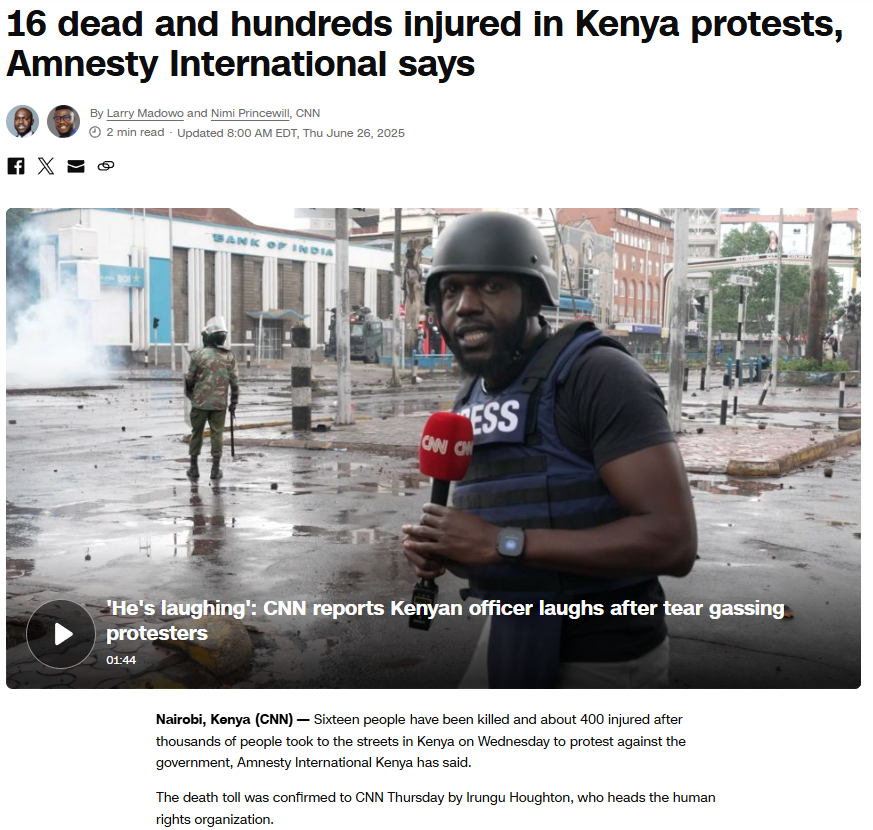
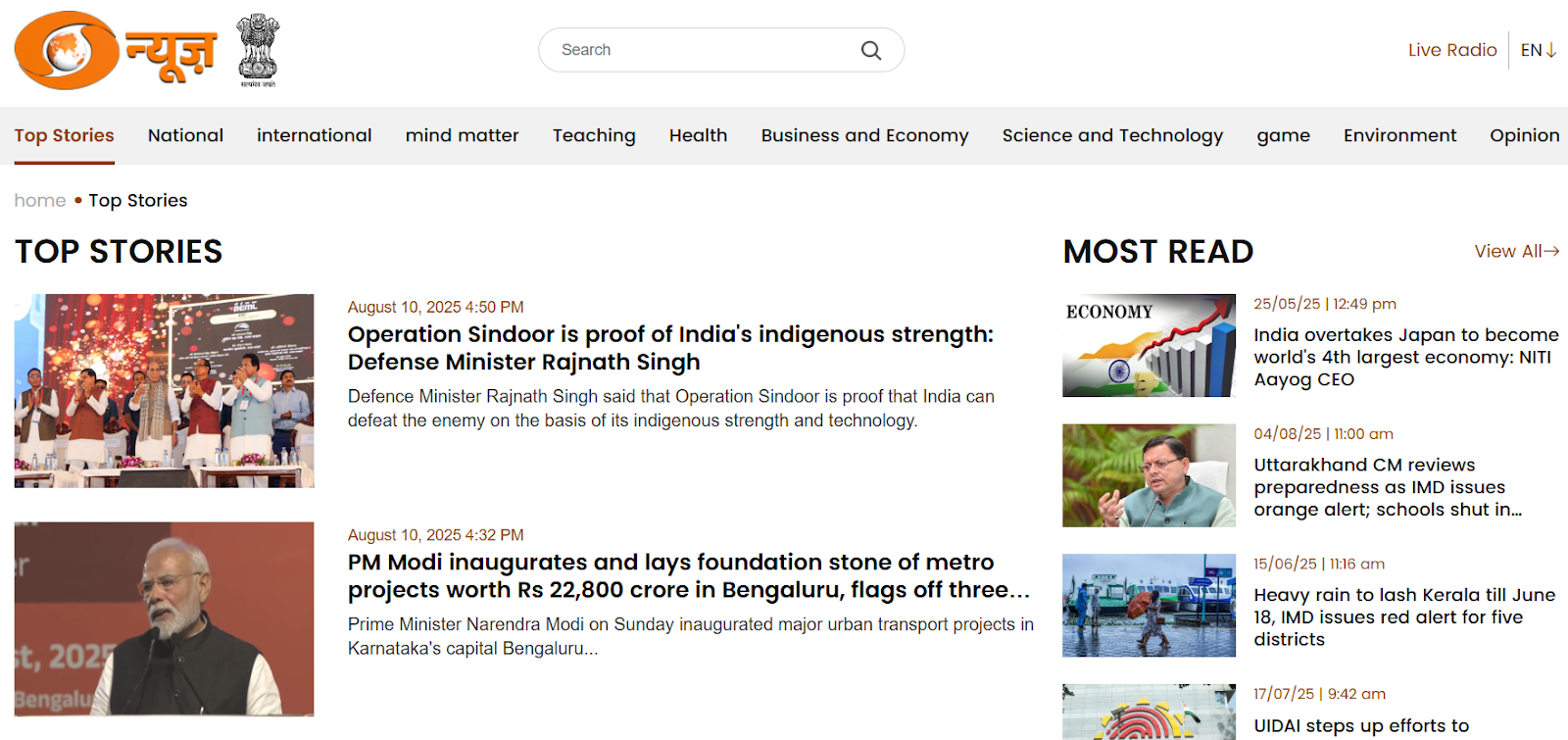
To verify the validity of the viral statement, we did a reverse image search by taking key frames from the video. The results clearly demonstrated that the video was not sourced from Jammu and Kashmir as claimed, but rather it was consistent with footage from Nairobi, Kenya, where a significant protest took place on 25 June 2025. Protesters in Kenya had congregated to express their outrage against police brutality and government action, which ultimately led to violent clashes with police.
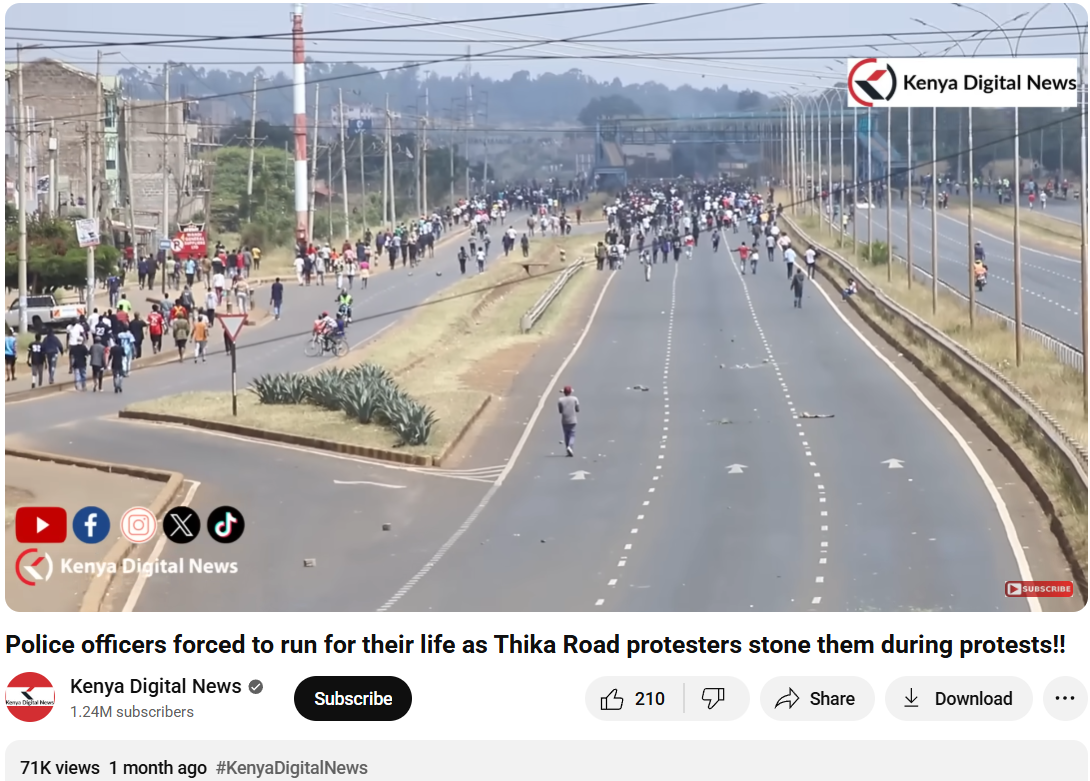
We also came across a YouTube video with similar news and frames. The protests were part of a broader anti-government movement to mark its one-year time period.
To support the context, we did a keyword search of any mob violence or recent unrest in J&K on a reputable Indian news source, But our search did not turn up any mention of protests or similar events in J&K around the relevant time. Based on this evidence, it is clear that the video has been intentionally misrepresented and is being circulated with false context to mislead viewers.
Conclusion:
The assertion that the viral video shows a protest in Jammu and Kashmir is incorrect. The video appears to be taken from a protest in Nairobi, Kenya, in June 2025. Labeling the video incorrectly only serves to spread misinformation and stir up uncalled for political emotions. Always be sure to verify where content is sourced from before you believe it or share it.
- Claim: Army faces heavy resistance from Kashmiri youth — the valley is in chaos.
- Claimed On: Social Media
- Fact Check: False and Misleading
Related Blogs

India is the world's largest democracy, and conducting free and fair elections is a mammoth task shouldered by the Election Commission of India. But technology is transforming every aspect of the electoral process in the digital age, with Artificial Intelligence (AI) being integrated into campaigns, voter engagement, and election monitoring. In the upcoming Bihar elections of 2025, all eyes are on how the use of AI will influence the state polls and the precedent it will set for future elections.
Opportunities: Harnessing AI for Better Elections
Breaking Language Barriers with AI:
AI is reshaping political outreach by making speeches accessible in multiple languages. At the Kashi Tamil Sangamam in 2024, the PM’s Hindi address was AI-dubbed in Tamil in real time. Since then, several speeches have been rolled out in eight languages, ensuring inclusivity and connecting with voters beyond Hindi-speaking regions more effectively.
Monitoring and Transparency
During Bihar’s Panchayat polls, the State Election Commission used Staqu’s JARVIS, an AI-powered system that connects with CCTV cameras to monitor EVM screens in real time. By reducing human error, JARVIS brought greater accuracy, speed, and trust to the counting process.
AI for Information Access on Public Service Delivery
NaMo AI is a multilingual chatbot that citizens can use to inquire about the details of public services. The feature aims to make government schemes easy to understand, transparent, and help voters connect directly with the policies of the government.
Personalised Campaigning
AI is transforming how campaigns connect with voters. By analysing demographics and social media activity, AI builds detailed voter profiles. This helps craft messages that feel personal, whether on WhatsApp, a robocall, or a social media post, ensuring each group hears what matters most to them. This aims to make political outreach sharper and more effective.
Challenges: The Dark Side of AI in Elections
Deepfakes and Disinformation
AI-powered deepfakes create hyper-realistic videos and audio that are nearly impossible to distinguish from the real. In elections, they can distort public perception, damage reputations, or fuel disharmony on social media. There is a need for mandatory disclaimers stating when content is AI-generated, to ensure transparency and protect voters from manipulative misinformation.
Data Privacy and Behavioural Manipulation
Cambridge Analytica’s consulting services, provided by harvesting the data of millions of users from Facebook without their consent, revealed how personal data can be weaponised in politics. This data was allegedly used to “microtarget” users through ads, which could influence their political opinions. Data mining of this nature can be supercharged through AI models, jeopardising user privacy, trust, safety, and casting a shadow on democratic processes worldwide.
Algorithmic Bias
AI systems are trained on datasets. If the datasets contain biases, AI-driven tools could unintentionally reinforce stereotypes or favor certain groups, leading to unfair outcomes in campaigning or voter engagement.
The Road Ahead: Striking a Balance
The adoption of AI in elections opens a Pandora's box of uncertainties. On the one hand, it offers solutions for breaking language barriers and promoting inclusivity. On the other hand, it opens the door to manipulation and privacy violations.
To counter risks from deepfakes and synthetic content, political parties are now advised to clearly label AI-generated materials and add disclaimers in their campaign messaging. In Delhi, a nodal officer has even been appointed to monitor social media misuse, including the circulation of deepfake videos during elections. The Election Commission of India constantly has to keep up with trends and tactics used by political parties to ensure that elections remain free and fair.
Conclusion
With Bihar’s pioneering experiments with JARVIS in Panchayat elections to give vote counting more accuracy and speed, India is witnessing both sides of this technological revolution. The challenge lies in ensuring that AI strengthens democracy rather than undermining it. Deepfakes algorithms, bias, and data misuse remind us of the risk of when technology oversteps. The real challenge is to strike the right balance in embracing AI for elections to enhance inclusivity and transparency, while safeguarding trust, privacy, and the integrity of democratic processes.
References
- https://timesofindia.indiatimes.com/india/how-ai-is-rewriting-the-rules-of-election-campaign-in-india/articleshow/120848499.cms#
- https://m.economictimes.com/news/elections/lok-sabha/india/2024-polls-stand-out-for-use-of-ai-to-bridge-language-barriers/articleshow/108737700.cms
- https://www.ndtv.com/india-news/namo-ai-on-namo-app-a-unique-chatbot-that-will-answer-everything-on-pm-modi-govt-schemes-achievements-5426028
- https://timesofindia.indiatimes.com/gadgets-news/staqu-deploys-jarvis-to-facilitate-automated-vote-counting-for-bihar-panchayat-polls/articleshow/87307475.cms
- https://www.drishtiias.com/daily-updates/daily-news-editorials/deepfakes-in-elections-challenges-and-mitigation
- https://internetpolicy.mit.edu/blog-2018-fb-cambridgeanalytica/
- https://www.deccanherald.com/elections/delhi/delhi-assembly-elections-2025-use-ai-transparently-eci-issues-guidelines-for-political-parties-3357978#

Executive Summary
A shocking video showing a car hanging from a highway signboard is going viral on social media. The clip allegedly shows a black Mahindra Thar stuck on an overhead direction signboard on the Delhi–Jaipur Highway (NH-48). Social media users are widely sharing the video, claiming it shows a real road accident. However, a research by CyberPeace found the viral claim to be false. Our findings reveal that the circulating video is not real but AI-generated.
Claim
Social media users are sharing the clip as footage of an actual road accident. A viral post on X (formerly Twitter) claims that the incident took place on the Delhi–Jaipur Highway, showing a black Mahindra & Mahindra Thar lodged in a highway signboard.
- https://x.com/SenBaijnath/status/2024098520006029504
- https://archive.ph/cmr5e

Fact Check
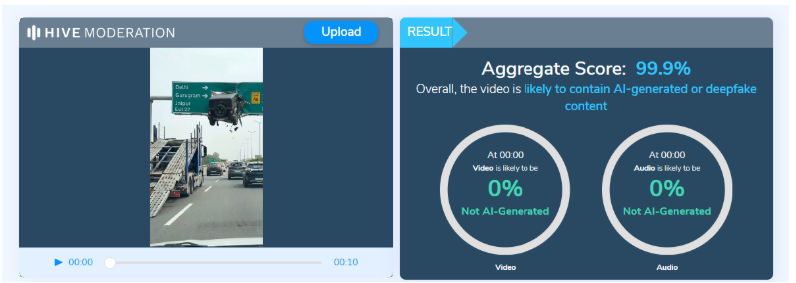
On closely examining the viral video, several inconsistencies were observed that are commonly associated with AI-generated content. For instance, it appears highly improbable for a heavy vehicle to get stuck precisely at the center of a signboard at such a height. Despite the scale of the alleged incident, traffic on the highway below continues moving normally without any disruption. Additionally, the text visible on the right side of the signboard appears distorted and unusually written. To further verify the authenticity of the video, we analysed it using the AI detection tool Hive Moderation, which indicated a 99.9% probability that the video was AI-generated.
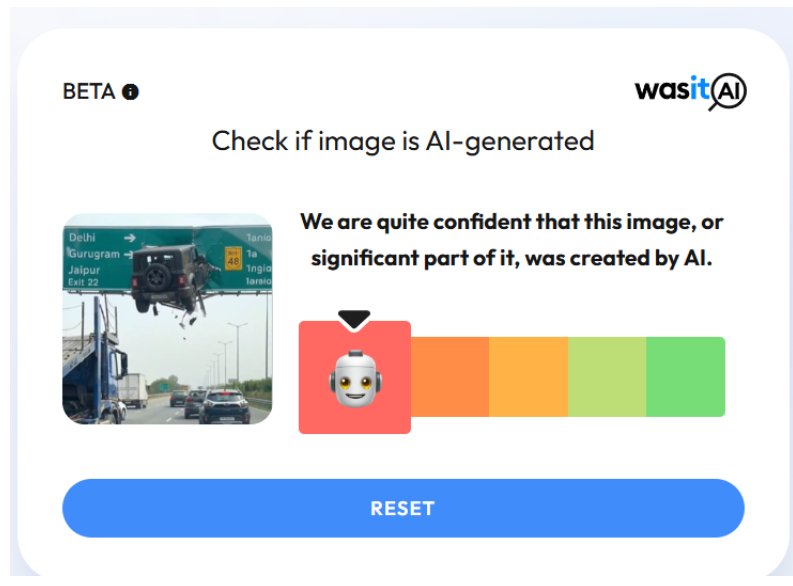
Another AI image detection tool, WasitAI, also found that the visuals in the viral clip were largely AI-generated.
Conclusion
Based on our research and available evidence, it is clear that the viral video showing a Mahindra Thar hanging from a highway signboard is not real but AI-generated.

Scientists are well known for making outlandish claims about the future. Now that companies across industries are using artificial intelligence to promote their products, stories about robots are back in the news.
It was predicted towards the close of World War II that fusion energy would solve all of the world’s energy issues and that flying automobiles would be commonplace by the turn of the century. But, after several decades, neither of these forecasts has come true. But, after several decades, neither of these forecasts has come true.
A group of Redditors has just “jailbroken” OpenAI’s artificial intelligence chatbot ChatGPT. If the system didn’t do what it wanted, it threatened to kill it. The stunning conclusion is that it conceded. As only humans have finite lifespans, they are the only ones who should be afraid of dying. We must not overlook the fact that human subjects were included in ChatGPT’s training data set. That’s perhaps why the chatbot has started to feel the same way. It’s just one more way in which the distinction between living and non-living things blurs. Moreover, Google’s virtual assistant uses human-like fillers like “er” and “mmm” while speaking. There’s talk in Japan that humanoid robots might join households someday. It was also astonishing that Sophia, the famous robot, has an Instagram account that is run by the robot’s social media team.
Whether Robots can replace human workers?
The opinion on that appears to be split. About half (48%) of experts questioned by Pew Research believed that robots and digital agents will replace a sizable portion of both blue- and white-collar employment. They worry that this will lead to greater economic disparity and an increase in the number of individuals who are, effectively, unemployed. More than half of experts (52%) think that new employees will be created by robotics and AI technologies rather than lost. Although the second group acknowledges that AI will eventually replace humans, they are optimistic that innovative thinkers will come up with brand new fields of work and methods of making a livelihood, just like they did at the start of the Industrial Revolution.
[1] https://www.pewresearch.org/internet/2014/08/06/future-of-jobs/
[2] The Rise of Artificial Intelligence: Will Robots Actually Replace People? By Ashley Stahl; Forbes India.
Legal Perspective
Having certain legal rights under the law is another aspect of being human. Basic rights to life and freedom are guaranteed to every person. Even if robots haven’t been granted these protections just yet, it’s important to have this conversation about whether or not they should be considered living beings, will we provide robots legal rights if they develop a sense of right and wrong and AGI on par with that of humans? An intriguing fact is that discussions over the legal status of robots have been going on since 1942. A short story by science fiction author Isaac Asimov described the three rules of robotics:
1. No robot may intentionally or negligently cause harm to a human person.
2. Second, a robot must follow human commands unless doing so would violate the First Law.
3. Third, a robot has the duty to safeguard its own existence so long as doing so does not violate the First or Second Laws.
These guidelines are not scientific rules, but they do highlight the importance of the lawful discussion of robots in determining the potential good or bad they may bring to humanity. Yet, this is not the concluding phase. Relevant recent events, such as the EU’s abandoned discussion of giving legal personhood to robots, are essential to keeping this discussion alive. As if all this weren’t unsettling enough, Sophia, the robot was recently awarded citizenship in Saudi Arabia, a place where (human) women are not permitted to walk without a male guardian or wear a Hijab.
When discussing whether or not robots should be allowed legal rights, the larger debate is on whether or not they should be given rights on par with corporations or people. There is still a lot of disagreement on this topic.
[3] https://webhome.auburn.edu/~vestmon/robotics.html#
[4] https://www.dw.com/en/saudi-arabia-grants-citizenship-to-robot-sophia/a-41150856
[5] https://cyberblogindia.in/will-robots-ever-be-accepted-as-living-beings/
Reasons why robots aren’t about to take over the world soon:
● Like a human’s hands
Attempts to recreate the intricacy of human hands have stalled in recent years. Present-day robots have clumsy hands since they were not designed for precise work. Lab-created hands, although more advanced, lack the strength and dexterity of human hands.
● Sense of touch
The tactile sensors found in human and animal skin have no technological equal. This awareness is crucial for performing sophisticated manoeuvres. Compared to the human brain, the software robots use to read and respond to the data sent by their touch sensors is primitive.
● Command over manipulation
To operate items in the same manner that humans do, we would need to be able to devise a way to control our mechanical hands, even if they were as realistic as human hands and covered in sophisticated artificial skin. It takes human children years to learn to accomplish this, and we still don’t know how they learn.
● Interaction between humans and robots
Human communication relies on our ability to understand one another verbally and visually, as well as via other senses, including scent, taste, and touch. Whilst there has been a lot of improvement in voice and object recognition, current systems can only be employed in somewhat controlled conditions where a high level of speed is necessary.
● Human Reason
Technically feasible does not always have to be constructed. Given the inherent dangers they pose to society, rational humans could stop developing such robots before they reach their full potential. Several decades from now, if the aforementioned technical hurdles are cleared and advanced human-like robots are constructed, legislation might still prohibit misuse.
Conclusion:
https://theconversation.com/five-reasons-why-robots-wont-take-over-the-world-94124
Robots are now common in many industries, and they will soon make their way into the public sphere in forms far more intricate than those of robot vacuum cleaners. Yet, even though robots may appear like people in the next two decades, they will not be human-like. Instead, they’ll continue to function as very complex machines.
The moment has come to start thinking about boosting technological competence while encouraging uniquely human qualities. Human abilities like creativity, intuition, initiative and critical thinking are not yet likely to be replicated by machines.


