#Factcheck-False Claims of Houthi Attack on Israel’s Ashkelon Power Plant
Executive Summary:
A post on X (formerly Twitter) has gained widespread attention, featuring an image inaccurately asserting that Houthi rebels attacked a power plant in Ashkelon, Israel. This misleading content has circulated widely amid escalating geopolitical tensions. However, investigation shows that the footage actually originates from a prior incident in Saudi Arabia. This situation underscores the significant dangers posed by misinformation during conflicts and highlights the importance of verifying sources before sharing information.

Claims:
The viral video claims to show Houthi rebels attacking Israel's Ashkelon power plant as part of recent escalations in the Middle East conflict.

Fact Check:
Upon receiving the viral posts, we conducted a Google Lens search on the keyframes of the video. The search reveals that the video circulating online does not refer to an attack on the Ashkelon power plant in Israel. Instead, it depicts a 2022 drone strike on a Saudi Aramco facility in Abqaiq. There are no credible reports of Houthi rebels targeting Ashkelon, as their activities are largely confined to Yemen and Saudi Arabia.

This incident highlights the risks associated with misinformation during sensitive geopolitical events. Before sharing viral posts, take a brief moment to verify the facts. Misinformation spreads quickly and it’s far better to rely on trusted fact-checking sources.
Conclusion:
The assertion that Houthi rebels targeted the Ashkelon power plant in Israel is incorrect. The viral video in question has been misrepresented and actually shows a 2022 incident in Saudi Arabia. This underscores the importance of being cautious when sharing unverified media. Before sharing viral posts, take a moment to verify the facts. Misinformation spreads quickly, and it is far better to rely on trusted fact-checking sources.
- Claim: The video shows massive fire at Israel's Ashkelon power plant
- Claimed On:Instagram and X (Formerly Known As Twitter)
- Fact Check: False and Misleading
Related Blogs
.webp)
Executive Summary:
A viral video claims to show a massive cumulonimbus cloud over Gurugram, Haryana, and Delhi NCR on 3rd September 2025. However, our research reveals the claim is misleading. A reverse image search traced the visuals to Lviv, Ukraine, dating back to August 2021. The footage matches earlier reports and was even covered by the Ukrainian news outlet 24 Kanal, which published the story under the headline “Lviv Covered by Unique Thundercloud: Amazing Video”. Thus, the viral claim linking the phenomenon to a recent event in India is false.
Claim:
A viral video circulating on social media claims to show a massive cloud formation over Gurugram, Haryana, and the Delhi NCR region on 3rd September 2025. The cloud appears to be a cumulonimbus formation, which is typically associated with heavy rainfall, thunderstorms, and severe weather conditions.

Fact Check:
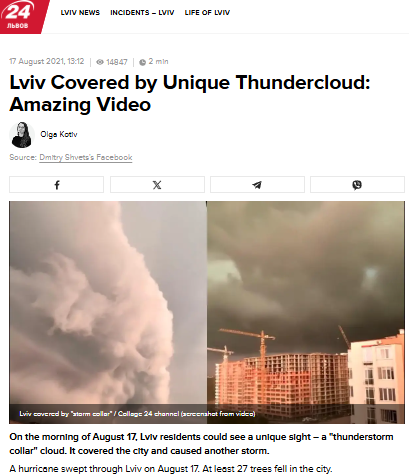
After conducting a reverse image search on key frames of the viral video, we found matching visuals from videos that attribute the phenomenon to Lviv, a city in Ukraine. These videos date back to August 2021, thereby debunking the claim that the footage depicts a recent weather event over Gurugram, Haryana, or the Delhi NCR region.
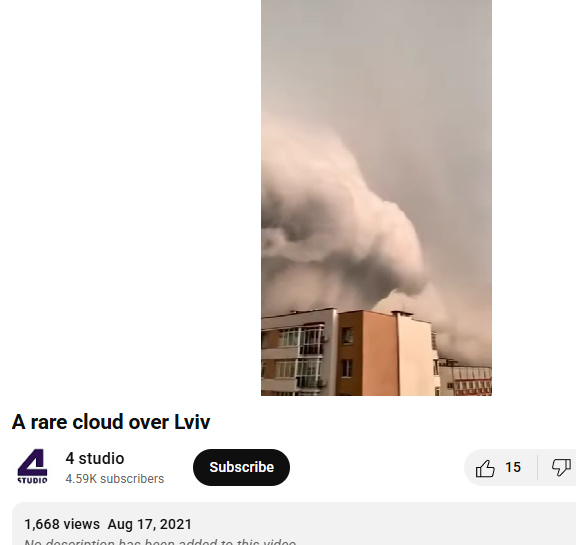

Further research revealed that a Ukrainian news channel named 24 Kanal, had reported on the Lviv thundercloud phenomenon in August 2021. The report was published under the headline “Lviv Covered by Unique Thundercloud: Amazing Video” ( original in Russian, translated into English).
Conclusion:
The viral video does not depict a recent weather event in Gurugram or Delhi NCR, but rather an old incident from Lviv, Ukraine, recorded in August 2021. Verified sources, including Ukrainian media coverage, confirm this. Hence, the circulating claim is misleading and false.
- Claim: Old Thundercloud Video from Lviv city in Ukraine Ukraine (2021) Falsely Linked to Delhi NCR, Gurugram and Haryana.
- Claimed On: Social Media
- Fact Check: False and Misleading.
.webp)
Introduction
With the advent of the internet, the world revealed the promise of boundless connection and the ability to bridge vast distances with a single click. However, as we wade through the complex layers of the digital age, we find ourselves facing a paradoxical realm where anonymity offers both liberation and a potential for unforeseen dangers. Omegle, a chat and video messaging platform, epitomizes this modern conundrum. Launched over a decade ago in 2009, it has burgeoned into a popular avenue for digital interaction, especially amidst the heightened need for human connection spurred by the COVID-19 pandemic's social distancing requirements. Yet, this seemingly benign tool of camaraderie, tragically, doubles as a contemporary incarnation of Pandora's box, unleashing untold risks upon the online privacy and security landscape. Omegle shuts down its operations permanently after 14 years of its service.
The Rise of Omegle
The foundations of this nebulous virtual dominion can be traced back to the very architecture of Omegle. Introduced to the world as a simple, anonymous chat service, Omegle has since evolved, encapsulating the essence of unpredictable human interaction. Users enter this digital arena, often with the innocent desire to alleviate the pangs of isolation or simply to satiate curiosity; yet they remain blissfully unaware of the potential cybersecurity maelstrom that awaits them.
As we commence a thorough inquiry into the psyche of Omegle's vast user base, we observe a digital diaspora with staggering figures. The platform, in May 2022, counted 51.7 million unique visitors, a testament to its sprawling reach across the globe. Delve a bit deeper, and you will uncover that approximately 29.89% of these digital nomads originate from the United States. Others, in varying percentages, flock from India, the Philippines, the United Kingdom, and Germany, revealing a vast, intricate mosaic of international engagement.
Such statistics beguile the uninformed observer with the lie of demographic diversity. Yet we must proceed with caution, for while the platform boasts an impressive 63.91% male patronage, we cannot overlook the notable surge in female participation, which has climbed to 36.09% during the pandemic era. More alarming still is the revelation, borne out of a BBC investigation in February 2021, that children as young as seven have trespassed into Omegle's adult sections—a section purportedly guarded by a minimum age limit of thirteen. How we must ask, has underage presence burgeoned on this platform? A sobering pointer finger towards the platform's inadvertent marketing on TikTok, where youthful influencers, with abandon, promote their Omegle exploits under the #omegle hashtag.
The Omegle Allure
Omegle's allure is further compounded by its array of chat opportunities. It flaunts an adult section awash with explicit content, a moderated chat section that, despite the platform's own admissions, remains imperfectly patrolled, and an unmoderated section, its entry pasted with forewarnings of an 18+ audience. Beyond these lies the college chat option, a seemingly exclusive territory that only admits individuals armed with a verified '.edu' email address.
The effervescent charm of Omegle's interface, however, belies its underlying treacheries. Herein lies a digital wilderness where online predators and nefarious entities prowl, emboldened by the absence of requisite registration protocols. No email address, no unique identifier—pestilence to any notion of accountability or safeguarding. Within this unchecked reality, the young and unwary stand vulnerable, a hapless game for exploitation.
Threat to Users
Venture even further into Omegle's data fiefdom, and the spectre of compromise looms larger. Users, particularly the youth, risk exposure to unsuitable content, and their naivety might lead to the inadvertent divulgence of personal information. Skulking behind the facade of connection, opportunities abound for coercion, blackmail, and stalking—perils rendered more potent as every video exchange and text can be captured, and recorded by an unseen adversary. The platform acts as a quasi-familiar confidante, all the while harvesting chat logs, cookies, IP addresses, and even sensory data, which, instead of being ephemeral, endure within Omegle's databases, readily handed to law enforcement and partnered entities under the guise of due diligence.
How to Combat the threat
In mitigating these online gorgons, a multi-faceted approach is necessary. To thwart incursion into your digital footprint, adults, seeking the thrills of Omegle's roulette, would do well to cloak their activities with a Virtual Private Network (VPN), diligently pore over the privacy policy, deploy robust cybersecurity tools, and maintain an iron-clad reticence on personal disclosures. For children, the recommendation gravitates towards outright avoidance. There, a constellation of parental control mechanisms await the vigilant guardian, ready to shield their progeny from the internet's darker alcoves.
Conclusion
In the final analysis, Omegle emerges as a microcosm of the greater web—a vast, paradoxical construct proffering solace and sociability, yet riddled with malevolent traps for the uninformed. As digital denizens, our traverse through this interconnected cosmos necessitates a relentless guarding of our private spheres and the sober acknowledgement that amidst the keystrokes and clicks, we must tread with caution lest we unseal the perils of this digital Pandora's box.
References:
.webp)
Introduction
In July 2025, the Digital Defence Report prepared by Microsoft raised an alarm that India is part of the top target countries in AI-powered nation-state cyberattacks with malicious agents automating phishing, creating convincing deepfakes, and influencing opinion with the help of generative AI (Microsoft Digital Defence Report, 2025). Most of the attention in the world has continued to be on the United States and Europe, but Asia-Pacific and especially India have become a major target in terms of AI-based cyber activities. This blog discusses the role of AI in espionage, redefining the threat environment of India, the reaction of the government, and what India can learn by looking at the example of cyber giants worldwide.
Understanding AI-Powered Cyber Espionage
Conventional cyber-espionage intends to hack systems, steal information or bring down networks. With the emergence of generative AI, these strategies have changed completely. It is now possible to automate reconnaissance, create fake voices and videos of authorities and create highly advanced phishing campaigns which can pass off as genuine even to a trained expert. According to the report made by Microsoft, AI is being used by state-sponsored groups to expand their activities and increase accuracy in victims (Microsoft Digital Defence Report, 2025). Based on SQ Magazine, almost 42 percent of state-based cyber campaigns in 2025 had AIs like adaptive malware or intelligent vulnerability scanners (SQ Magazine, 2025).
AI is altering the power dynamic of cyberspace. The tools previously needing significant technical expertise or substantial investments have become ubiquitous, and smaller countries can conduct sophisticated cyber operations as well as non-state actors. The outcome is the speeding up of the arms race with AI serving as the weapon and the armour.
India’s Exposure and Response
The weakness of the threat landscape lies in the growing online infrastructure and geopolitical location. The attack surface has expanded the magnitude of hundreds of millions of citizens with the integration of platforms like DigiLocker and CoWIN. Financial institutions, government portals and defence networks are increasingly becoming targets of cyber attacks that are more sophisticated. Faking videos of prominent figures, phishing letters with the official templates, and manipulation of the social media are currently all being a part of disinformation campaigns (Microsoft Digital Defence Report, 2025).
According to the Data Security Council of India (DSCI), the India Cyber Threat Report 2025 reported that attacks using AI are growing exponentially, particularly in the shape of malicious behaviour and social engineering (DSCI, 2025). The nodal cyber-response agency of India, CERT-In, has made several warnings regarding scams related to AI and AI-generated fake content that is aimed at stealing personal information or deceiving the population. Meanwhile, enforcement and red-teaming actions have been intensified, but the communication between central agencies and state police and the private platforms is not even. There is also an acute shortage of cybersecurity talents in India, as less than 20 percent of cyber defence jobs are occupied by qualified specialists (DSCI, 2025).
Government and Policy Evolution
The government response to AI-enabled threats is taking three forms, namely regulation, institutional enhancing, and capacity building. The Digital Personal Data Protection Act 2023 saw a major move in defining digital responsibility (Government of India, 2023). Nonetheless, threats that involve AI-specific issues like data poisoning, model manipulation, or automated disinformation remain grey areas. The following National Cybersecurity Strategy will attempt to remedy them by establishing AI-government guidelines and responsibility standards to major sectors.
At the institutional level, the efforts of such organisations as the National Critical Information Infrastructure Protection Centre (NCIIPC) and the Defence Cyber Agency are also being incorporated into their processes with the help of AI-based monitoring. There is also an emerging public-private initiative. As an example, the CyberPeace Foundation and national universities have signed a memorandum of understanding that currently facilitates the specialised training in AI-driven threat analysis and digital forensics (Times of India, August 2025). Even after these positive indications, India does not have any cohesive system of reporting cases of AI. The publication on arXiv in September 2025 underlines the importance of the fact that legal approaches to AI-failure reporting need to be developed by countries to approach AI-initiated failures in such fields as national security with accountability (arXiv, 2025).
Global Implications and Lessons for India
Major economies all over the world are increasing rapidly to integrate AI innovation with cybersecurity preparedness. The United States and United Kingdom are spending big on AI-enhanced military systems, performing machine learning in security operations hubs and organising AI-based “red team” exercises (Microsoft Digital Defence Report, 2025). Japan is testing cross-ministry threat-sharing platforms that utilise AI analytics and real-time decision-making (Microsoft Digital Defence Report, 2025).
Four lessons can be distinguished as far as India is concerned.
- To begin with, the cyber defence should shift to proactive intelligence in place of reactive investigation. It is not only possible to detect the adversary behaviour after the attacks, but to simulate them in advance using AI.
- Second, teamwork is essential. The issue of cybersecurity cannot be entrusted to government enforcement. The private sector that maintains the majority of the digital infrastructure in India must be actively involved in providing information and knowledge.
- Third, there is the issue of AI sovereignty. Building or hosting its own defensive AI tools in India will diminish dependence on foreign vendors, and minimise the possible vulnerabilities of the supply-chain.
- Lastly, the initial defence is digital literacy. The citizens should be trained on how to detect deepfakes, phishing, and other manipulated information. The importance of creating human awareness cannot be underestimated as much as technical defences (SQ Magazine, 2025).
Conclusion
AI has altered the reasoning behind cyber warfare. There are quicker attacks, more difficult to trace and scalable as never before. In the case of India, it is no longer about developing better firewalls but rather the ability to develop anticipatory intelligence to counter AI-powered threats. This requires a national policy that incorporates technology, policy and education.
India can transform its vulnerability to strength with the sustained investment, ethical AI governance, and healthy cooperation between the government and the business sector. The following step in cybersecurity does not concern who possesses more firewalls than the other but aims to learn and adjust more quickly and successfully in a world where machines already belong to the battlefield (Microsoft Digital Defence Report, 2025).
References:
- Microsoft Digital Defense Report 2025
- India Cyber Threat Report 2025, DSCI
- Lucknow based organisations to help strengthen cybercrime research training policy ecosystem
- AI Cyber Attacks Statistics 2025: How Attacks, Deepfakes & Ransomware Have Escalated, SQ Magazine
- Incorporating AI Incident Reporting into Telecommunications Law and Policy: Insights from India.
- The Digital Personal Data Protection Act, 2023


