#FactCheck - Viral Video Misleadingly Tied to Recent Taiwan Earthquake
Executive Summary:
In the context of the recent earthquake in Taiwan, a video has gone viral and is being spread on social media claiming that the video was taken during the recent earthquake that occurred in Taiwan. However, fact checking reveals it to be an old video. The video is from September 2022, when Taiwan had another earthquake of magnitude 7.2. It is clear that the reversed image search and comparison with old videos has established the fact that the viral video is from the 2022 earthquake and not the recent 2024-event. Several news outlets had covered the 2022 incident, mentioning additional confirmation of the video's origin.

Claims:
There is a news circulating on social media about the earthquake in Taiwan and Japan recently. There is a post on “X” stating that,
“BREAKING NEWS :
Horrific #earthquake of 7.4 magnitude hit #Taiwan and #Japan. There is an alert that #Tsunami might hit them soon”.

Similar Posts:


Fact Check:
We started our investigation by watching the videos thoroughly. We divided the video into frames. Subsequently, we performed reverse search on the images and it took us to an X (formally Twitter) post where a user posted the same viral video on Sept 18, 2022. Worth to notice, the post has the caption-
“#Tsunami warnings issued after Taiwan quake. #Taiwan #Earthquake #TaiwanEarthquake”

The same viral video was posted on several news media in September 2022.

The viral video was also shared on September 18, 2022 on NDTV News channel as shown below.

Conclusion:
To conclude, the viral video that claims to depict the 2024 Taiwan earthquake was from September 2022. In the course of the rigorous inspection of the old proof and the new evidence, it has become clear that the video does not refer to the recent earthquake that took place as stated. Hence, the recent viral video is misleading . It is important to validate the information before sharing it on social media to prevent the spread of misinformation.
Claim: Video circulating on social media captures the recent 2024 earthquake in Taiwan.
Claimed on: X, Facebook, YouTube
Fact Check: Fake & Misleading, the video actually refers to an incident from 2022.
Related Blogs
.webp)
Introduction
In today's digital economy, data is not only a business asset but also the fuel for innovation, decision-making, and consumer trust. However, the digitisation of services has made personal or sensitive data a top target for cybercriminals. The stakes are high: a data breach can cost millions of fines, cause damage to reputation and devastate the confidence of consumers. Therefore, regulatory compliance and data protection have become a strategic imperative.
From the General Data Protection Regulation (GDPR) in the EU to the Digital Personal Data Protection (DPDP) Act of India, various sector-specific regulations like HIPAA for healthcare in the US, companies are now subject to a web of data protection and compliance laws. The challenge is to balance compliance efforts with strong security, a balance that demands both policy restraint and technical resilience. This blog examines pivotal pillars, shifting trends and actionable best practices for dominating data protection and compliance in 2025 and beyond.
Why Data Protection and Compliance Matter More Than Ever
Data protection isn't just about keeping fines at bay, it's about preserving the relationship with customers, partners and regulators. A 2024 IBM report says the average data-breach cost has now exceeded USD 4.5 million, with regulatory fines constituting a large portion of the cost. In addition to economics, breaches tend to result in intellectual property loss, customer loss and long-term brand attenuation. Compliance ensures organisations remain within certain legislative necessities for collecting, holding, transferring and setting of personal and sensitive information. Failure to conformity can lead to serious penalties: under GDPR, fines could be up to 4% of the company's annual turnover or €20 million, whichever is higher. In regulated sectors like banking and healthcare, compliance breaches can also lead to the suspension of licenses.
Important Regulatory Frameworks Informing 2025
- GDPR and Its Global Ripple Effect
GDPR was enacted in 2018 and continues to have a ripple effect on privacy legislation worldwide. Its tenets of lawfulness, transparency, data minimisation and purpose limitation have been replicated in many jurisdictions such as Brazil's LGPD and South Korea's PIPA.
- India's DPDP Act
The DPDP Act, 2023, gives high importance to consent-based processing of data, transparent notice rules and fiduciary responsibilities for data. With a penalty for default of up to INR 250 crore, it's amongst the most impactful laws for digital personal data protection.
- Sectoral Regulations
- HIPAA for healthcare information in the US.
- PCI DSS for payment card security.
- DORA (Digital Operational Resilience Act) in the EU for financial organisations.
- These industry-specific models generate overlapping compliance responsibilities, making cross-enterprise compliance programs vital.
Key Pillars of a Sound Data Protection & Compliance Program
- Data Governance and Classification
Having insight into what data you have to store, where it is stored and who can have access to it is the keystone of compliance. Organisations need to have data classification policies in place to group information based on sensitivity and impose more rigorous controls on sensitive data.
- Security Controls and Privacy by Design
Strong technical defences, encryption, multi-factor authentication, and intrusion detection are the initial defences. Privacy by design integrated in product development guarantees compliance is thought through from the initial stage, not added on afterwards.
- Consent and Transparency
Contemporary data legislation highlights informed consent. This entails simple, non-technical privacy notices, detailed opt-in choices, and straightforward withdrawal options. Transparency produces trust and lessens legal danger.
- Incident Response and Breach Notification
Most laws demand timely breach notifications, and GDPR insists on reporting within 72 hours. Having a documented incident response plan maintains legal deadlines and reduces harm.
- Employee Training and Awareness
Human mistake is the top source of data breaches. Ongoing training in prevention of phishing, password management, basic cyber hygiene and compliance requirements is crucial.
Upcoming Trends in 2025
- AI-Powered Compliance Monitoring
Organisations are embracing AI-powered solutions to systematically monitor data flows, identify policy breaches and auto-create compliance reports. The solutions assist in closing the loop between IT security teams and compliance officers.
- Cross-Border Data Transfer Mechanisms
With increasingly severe regulations, companies are spending more on secure cross-border data transfer frameworks like Standard Contractual Clauses (SCCs) and Binding Corporate Rules (BCRs).
- Privacy-Enhancing Technologies (PETs)
Methods such as homomorphic encryption and differential privacy are picking up steam, enabling organisations to sift through datasets without revealing sensitive personal data.
- ESG and Data Ethics
Data handling is increasingly becoming a part of Environmental, Social and Governance (ESG) reporting. Ethical utilisation of customer data, not just compliance, has become a reputational differentiator.
Challenges in Implementation
Despite having transparent frameworks, data protection plans encounter challenges like jurisdictions having competing needs, and global compliance is becoming expensive. The emerging technologies, such as generative AI, often bring privacy threats that haven’t been fully covered by legislation. Small and micro enterprises have neither the budget nor the skills to implement enterprise-level compliance programs. Qualifying these challenges often needs a risk-based strategy, allocations of resources to top areas of impact and automating the compliance chores wherever possible.
Best Practices for 2025 and Beyond
In 2025, regulatory compliance and data protection are no longer a precaution or a response to a breach but are strategic drivers of resilience and trust. As regulatory analysis rises, cyber threats evolve, and consumer expectations grow, administrations need to integrate compliance into the very fabric of their actions. By bringing governance and technology together, organisations can break free from a "checklist" mentality and instead adopt a proactive and risk-sensitive approach. Eventually, data protection is not just about not getting in trouble; it's about developing a kind that succeeds in the digital era.
References
- GDPR – Official EU Regulation Page: https://gdpr.eu
- India’s DPDP Act Overview – MeitY: https://www.meity.gov.in/data-protection-framework
- HIPAA – US Department of Health & Human Services: https://www.hhs.gov/hipaa
- PCI DSS Standards: https://www.pcisecuritystandards.org
- IBM Cost of a Data Breach Report 2024: https://www.ibm.com/reports/data-breach
- OECD – Privacy Guidelines: https://www.oecd.org/sti/privacy-guidelines

Introduction
In today’s hyper-connected world, information spreads faster than ever before. But while much attention is focused on public platforms like Facebook and Twitter, a different challenge lurks in the shadows: misinformation circulating on encrypted and closed-network platforms such as WhatsApp and Telegram. Unlike open platforms where harmful content can be flagged in public, private groups operate behind a digital curtain. Here, falsehoods often spread unchecked, gaining legitimacy because they are shared by trusted contacts. This makes encrypted platforms a double-edged sword. It is essential for privacy and free expression, yet uniquely vulnerable to misuse.
As Prime Minister Narendra Modi rightly reminded,
“Think 10 times before forwarding anything,” warning that even a “single fake news has the capability to snowball into a matter of national concern.”
The Moderation Challenge with End-to-End Encryption
Encrypted messaging platforms were built to protect personal communication. Yet, the same end-to-end encryption that shields users’ privacy also creates a blind spot for moderation. Authorities, researchers, and even the platforms themselves cannot view content circulating in private groups, making fact-checking nearly impossible.
Trust within closed groups makes the problem worse. When a message comes from family, friends, or community leaders, people tend to believe it without questioning and quickly pass it along. Features like large group chats, broadcast lists, and “forward to many” options further speed up its spread. Unlike open networks, there is no public scrutiny, no visible counter-narrative, and no opportunity for timely correction.
During the COVID-19 pandemic, false claims about vaccines spread widely through WhatsApp groups, undermining public health campaigns. Even more alarming, WhatsApp rumors about child kidnappers and cow meat in India triggered mob lynchings, leading to the tragic loss of life.
Encrypted platforms, therefore, represent a unique challenge: they are designed to protect privacy, but, unintentionally, they also protect the spread of dangerous misinformation.
Approaches to Curbing Misinformation on End-to-End Platforms
- Regulatory: Governments worldwide are exploring ways to access encrypted data on messaging platforms, creating tensions between the right to user privacy and crime prevention. Approaches like traceability requirements on WhatsApp, data-sharing mandates for platforms in serious cases, and stronger obligations to act against harmful viral content are also being considered.
- Technological Interventions: Platforms like WhatsApp have introduced features such as “forwarded many times” labels and limits on mass forwarding. These tools can be expanded further by introducing AI-driven link-checking and warnings for suspicious content.
- Community-Based Interventions: Ultimately, no regulation or technology can succeed without public awareness. People need to be inoculated against misinformation through pre-bunking efforts and digital literacy campaigns. Fact-checking websites and tools also have to be taught.
Best Practices for Netizens
Experts recommend simple yet powerful habits that every user can adopt to protect themselves and others. By adopting these, ordinary users can become the first line of defence against misinformation in their own communities:
- Cross-Check Before Forwarding: Verify claims from trusted platforms & official sources.
- Beware of Sensational Content: Headlines that sound too shocking or dramatic probably need checking. Consult multiple sources for a piece of news. If only one platform/ channel is carrying sensational news, it is likely to be clickbait or outright false.
- Stick to Trusted News Sources: Verify news through national newspapers and expert commentary. Remember, not everything on the internet/television is true.
- Look Out for Manipulated Media: Now, with AI-generated deepfakes, it becomes more difficult to tell the difference between original and manipulated media. Check for edited images, cropped videos, or voice messages without source information. Always cross-verify any media received.
- Report Harmful Content: Report misinformation to the platform it is being circulated on and PIB’s Fact Check Unit.
Conclusion
In closed, unmonitored groups, platforms like WhatsApp and Telegram often become safe havens where people trust and forward messages from friends and family without question. Once misinformation takes root, it becomes extremely difficult to challenge or correct, and over time, such actions can snowball into serious social, economic and national concerns.
Preventing this is a matter of shared responsibility. Governments can frame balanced regulations, but individuals must also take initiative: pause, think, and verify before sharing. Ultimately, the right to privacy must be upheld, but with reasonable safeguards to ensure it is not misused at the cost of societal trust and safety.
References
- India WhatsApp ‘child kidnap’ rumours claim two more victims (BBC) The people trying to fight fake news in India (BBC)
- Press Information Bureau – PIB Fact Check
- Brookings Institution – Encryption and Misinformation Report (2021)
- Curtis, T. L., Touzel, M. P., Garneau, W., Gruaz, M., Pinder, M., Wang, L. W., Krishna, S., Cohen, L., Godbout, J.-F., Rabbany, R., & Pelrine, K. (2024). Veracity: An Open-Source AI Fact-Checking System. arXiv.
- NDTV – PM Modi cautions against fake news (2022)
- Times of India – Govt may insist on WhatsApp traceability (2019)
- Medianama – Telegram refused to share ISIS channel data (2019)

A video is being widely shared on social media showing a monkey, with users claiming that the animal is immersed in devotion to Lord Hanuman. The clip is being circulated with assertions that the monkey was seen participating in Hanuman Aarti. Cyber Peace Foundation’s research found that the viral claim is fake. Our investigation revealed that the video is not real and has been generated using artificial intelligence tools.
Claim
On January 6, 2026, Facebook users shared the viral video claiming, “A monkey was seen immersed in devotion during Hanuman Aarti.”
- Post link: https://www.facebook.com/reel/1261813845766976
- Archived link: https://archive.ph/anid5
Screenshots of the post can be seen below.

FactCheck:
When we closely examined the viral video, we noticed several visual inconsistencies. These anomalies raised suspicion that the video might be AI-generated. To verify this, we scanned the video using the AI detection tool Hive Moderation. According to the results, the video was found to be 97 percent AI-generated.
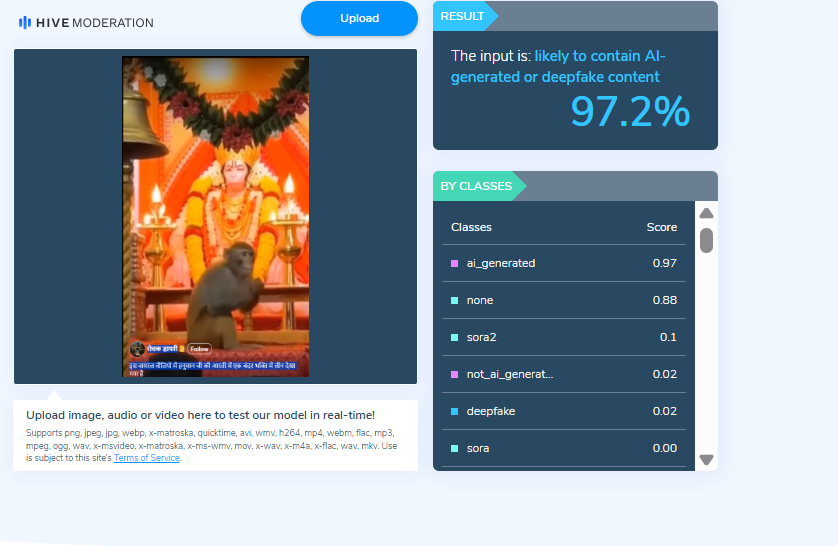
Further, we analysed the video using another AI detection tool, Sightengine. The tool’s assessment indicated that the viral video is 98 percent AI-generated.
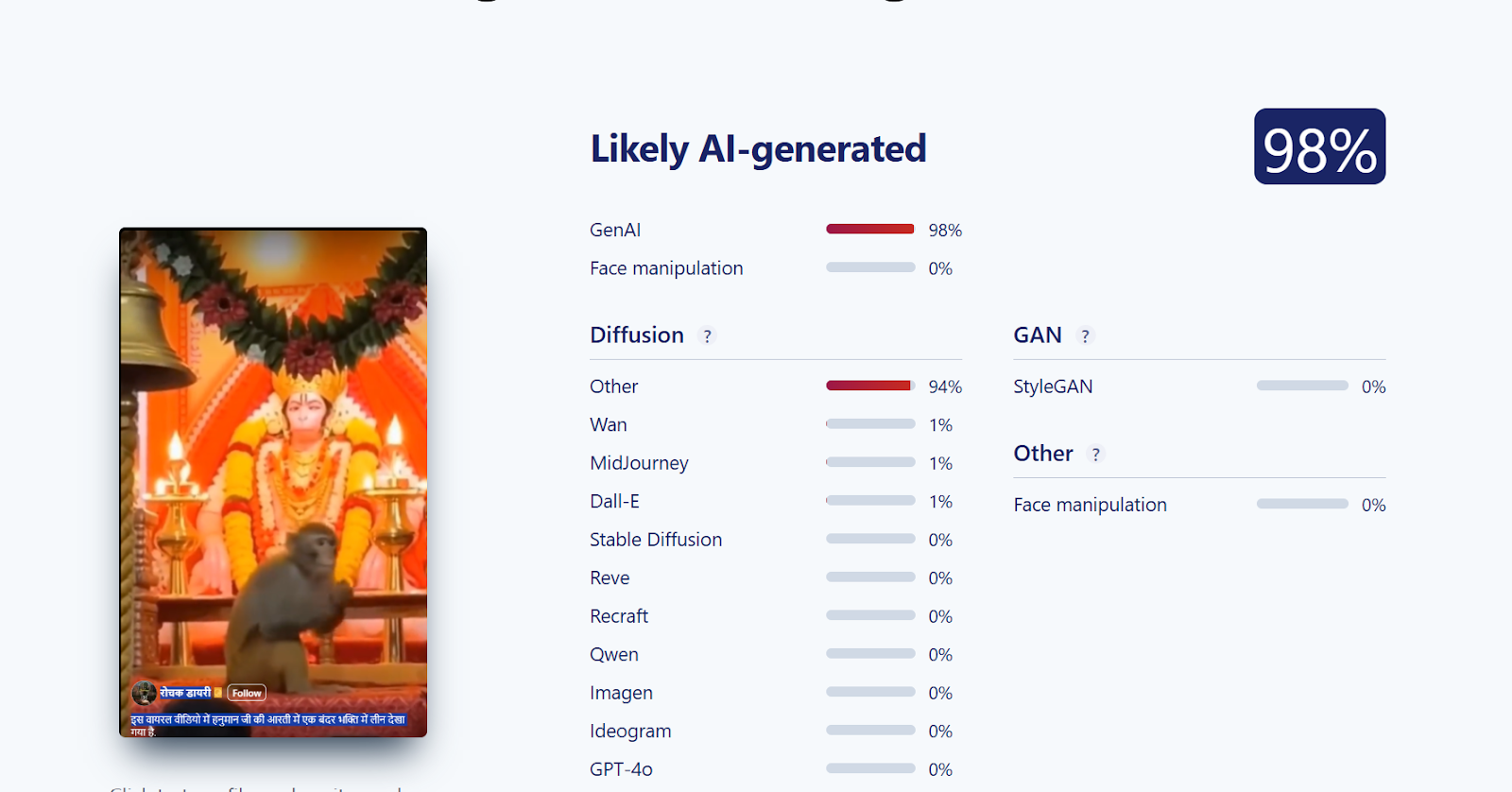
Conclusion
Our investigation confirms that the viral video claiming to show a monkey immersed in devotion to Lord Hanuman is AI-generated and not real. The claim circulating on social media is false and misleading.


