#FactCheck - Viral Photos Falsely Linked to Iranian President Ebrahim Raisi's Helicopter Crash
Executive Summary:
On 20th May, 2024, Iranian President Ebrahim Raisi and several others died in a helicopter crash that occurred northwest of Iran. The images circulated on social media claiming to show the crash site, are found to be false. CyberPeace Research Team’s investigation revealed that these images show the wreckage of a training plane crash in Iran's Mazandaran province in 2019 or 2020. Reverse image searches and confirmations from Tehran-based Rokna Press and Ten News verified that the viral images originated from an incident involving a police force's two-seater training plane, not the recent helicopter crash.
Claims:
The images circulating on social media claim to show the site of Iranian President Ebrahim Raisi's helicopter crash.



Fact Check:
After receiving the posts, we reverse-searched each of the images and found a link to the 2020 Air Crash incident, except for the blue plane that can be seen in the viral image. We found a website where they uploaded the viral plane crash images on April 22, 2020.

According to the website, a police training plane crashed in the forests of Mazandaran, Swan Motel. We also found the images on another Iran News media outlet named, ‘Ten News’.
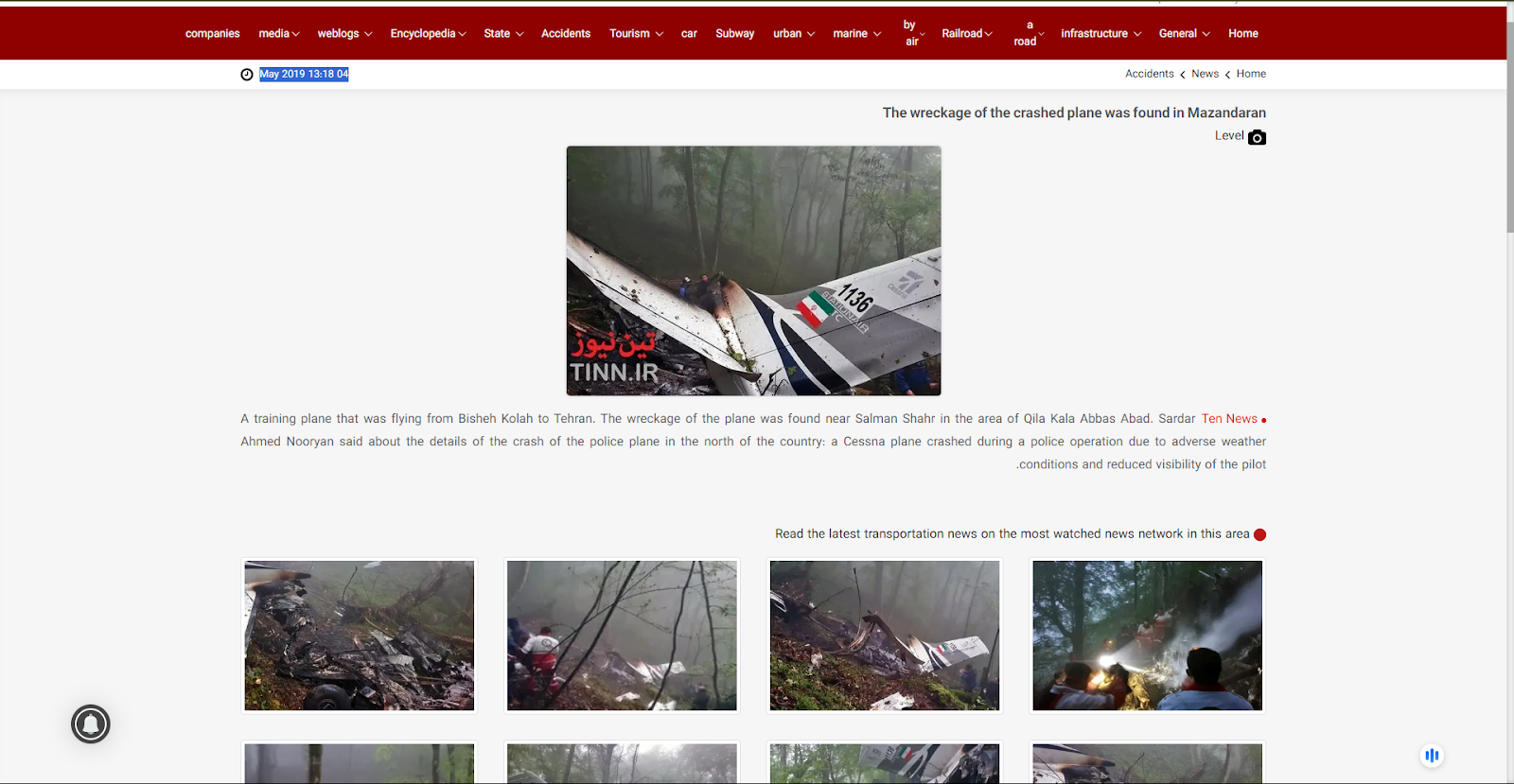
The Photos uploaded on to this website were posted in May 2019. The news reads, “A training plane that was flying from Bisheh Kolah to Tehran. The wreckage of the plane was found near Salman Shahr in the area of Qila Kala Abbas Abad.”
Hence, we concluded that the recent viral photos are not of Iranian President Ebrahim Raisi's Chopper Crash, It’s false and Misleading.
Conclusion:
The images being shared on social media as evidence of the helicopter crash involving Iranian President Ebrahim Raisi are incorrectly shown. They actually show the aftermath of a training plane crash that occurred in Mazandaran province in 2019 or 2020 which is uncertain. This has been confirmed through reverse image searches that traced the images back to their original publication by Rokna Press and Ten News. Consequently, the claim that these images are from the site of President Ebrahim Raisi's helicopter crash is false and Misleading.
- Claim: Viral images of Iranian President Raisi's fatal chopper crash.
- Claimed on: X (Formerly known as Twitter), YouTube, Instagram
- Fact Check: Fake & Misleading
Related Blogs

Introduction
India's Computer Emergency Response Team (CERT-In) has unfurled its banner of digital hygiene, heralding the initiative 'Cyber Swachhta Pakhwada,' a clarion call to the nation's citizens to fortify their devices against the insidious botnet scourge. The government's Cyber Swachhta Kendra (CSK)—a Botnet Cleaning and Malware Analysis Centre—stands as a bulwark in this ongoing struggle. It is a digital fortress, conceived under the aegis of the National Cyber Security Policy, with a singular vision: to engender a secure cyber ecosystem within India's borders. The CSK's mandate is clear and compelling—to detect botnet infections within the subcontinent and to notify, enable cleaning, and secure systems of end users to stymie further infections.
What are Bots?
Bots are automated rogue software programs crafted with malevolent intent, lurking in the shadows of the internet. They are the harbingers of harm, capable of data theft, disseminating malware, and orchestrating cyberattacks, among other digital depredations.
A botnet infection is like a parasitic infestation within the electronic sinews of our devices—smartphones, computers, tablets—transforming them into unwitting soldiers in a hacker's malevolent legion. Once ensnared within the botnet's web, these devices become conduits for a plethora of malicious activities: the dissemination of spam, the obstruction of communications, and the pilfering of sensitive information such as banking details and personal credentials.
How, then, does one's device fall prey to such a fate? The vectors are manifold: an infected email attachment opened in a moment of incaution, a malicious link clicked in haste, a file downloaded from the murky depths of an untrusted source, or the use of an unsecured public Wi-Fi network. Each action can be the key that unlocks the door to digital perdition.
In an era where malware attacks and scams proliferate like a plague, the security of our personal devices has ascended to a paramount concern. To address this exigency and to aid individuals in the fortification of their smartphones, the Department of Telecommunications(DoT) has unfurled a suite of free bot removal tools. The government's outreach extends into the ether, dispatching SMS notifications to the populace and disseminating awareness of these digital prophylactics.
Stay Cyber Safe
To protect your device from botnet infections and malware, the Government of India, through CERT-In, recommends downloading the 'Free Bot Removal Tool' at csk.gov.in.' This SMS is not merely a reminder but a beacon guiding users to a safe harbor in the tumultuous seas of cyberspace.
Cyber Swachhta Kendra
The Cyber Swachhta Kendra portal emerges as an oasis in the desert of digital threats, offering free malware detection tools to the vigilant netizen. This portal, also known as the Botnet Cleaning and Malware Analysis Centre, operates in concert with Internet Service Providers (ISPs) and antivirus companies, under the stewardship ofCERT-In. It is a repository of knowledge and tools, a digital armoury where users can arm themselves against the specters of botnet infection.
To extricate your device from the clutches of a botnet or to purge the bots and malware that may lurk within, one must embark on a journey to the CSK website. There, under the 'Security Tools' tab, lies the arsenal of antivirus companies, each offering their own bot removal tool. For Windows users, the choice includes stalwarts such as eScan Antivirus, K7 Security, and Quick Heal. Android users, meanwhile, can venture to the Google Play Store and seek out the 'eScan CERT-IN Bot Removal ' tool or 'M-Kavach2,' a digital shield forged by C-DAC Hyderabad.
Once the chosen app is ensconced within your device, it will commence its silent vigil, scanning the digital sinews for any trace of malware, excising any infections with surgical precision. But the CSK portal's offerings extend beyond mere bot removal tools; it also proffers other security applications such as 'USB Pratirodh' and 'AppSamvid.' These tools are not mere utilities but sentinels standing guard over the sanctity of our digital lives.
USB Pratirodh
'USB Pratirodh' is a desktop guardian, regulating the ingress and egress of removable storage media. It demands authentication with each new connection, scanning for malware, encrypting data, and allowing changes to read/write permissions. 'AppSamvid,' on the other hand, is a gatekeeper for Windows users, permitting only trusted executables and Java files to run, safeguarding the system from the myriad threats that lurk in the digital shadows.
Conclusion
In this odyssey through the digital safety frontier, the Cyber Swachhta Kendra stands as a testament to the power of collective vigilance. It is a reminder that in the vast, interconnected web of the internet, the security of one is the security of all. As we navigate the dark corners of the internet, let us equip ourselves with knowledge and tools, and may our devices remain steadfast sentinels in the ceaseless battle against the unseen adversaries of the digital age.
References
- https://timesofindia.indiatimes.com/gadgets-news/five-government-provided-botnet-and-malware-cleaning-tools/articleshow/107951686.cms
- https://indianexpress.com/article/technology/tech-news-technology/cyber-swachhta-kendra-free-botnet-detection-removal-tools-digital-india-8650425/

Introduction
Your iPhone isn’t just a device: it’s a central hub for almost everything in your life. From personal photos and videos to sensitive data, it holds it all. You rely on it for essential services, from personal to official communications, sharing of information, banking and financial transactions, and more. With so much critical information stored on your device, protecting it from cyber threats becomes essential. This is where the iOS Lockdown Mode feature comes in as a digital bouncer to keep cyber crooks at bay.
Apple introduced the ‘lockdown’ mode in 2022. It is a new optional security feature and is available on iPhones, iPads, and Mac devices. It works as an extreme and optional protection mechanism for a certain segment of users who might be at a higher risk of being targeted by serious cyber threats and intrusions into their digital security. So people like journalists, activists, government officials, celebrities, cyber security professionals, law enforcement professionals, and lawyers etc are some of the intended beneficiaries of the feature. Sometimes the data on their devices can be highly confidential and it can cause a lot of disruption if leaked or compromised by cyber threats. Given how prevalent cyber attacks are in this day and age, the need for such a feature cannot be overstated. This feature aims at providing an additional firewall by limiting certain functions of the device and hence reducing the chances of the user being targeted in any digital attack.
How to Enable Lockdown Mode in Your iPhone
On your iPhone running on iOS 16 Developer Beta 3, you just need to go to Settings - Privacy and Security - Lockdown Mode. Tap on Turn on Lockdown Mode, and read all the information regarding the features that will be unavailable on your device if you go forward, and if you’re satisfied with the same all you have to do is scroll down and tap on Turn on Lockdown Mode. Your iPhone will get restarted with Lockdown Mode enabled.
Easy steps to enable lockdown mode are as follows:
- Open the Settings app.
- Tap Privacy & Security.
- Scroll down, tap Lockdown Mode, then tap Turn On Lockdown Mode.
How Lockdown Mode Protects You
Lockdown Mode is a security feature that prevents certain apps and features from functioning properly when enabled. For example, your device will not automatically connect to Wi-Fi networks without security and will disconnect from a non-secure network when Lockdown Mode is activated. Many other features may be affected because the system will prioritise security standards above the typical operational functions. Since lockdown mode restricts certain features and activities, one can exclude a particular app or website in Safari from being impacted and limited by restrictions. Only exclude trusted apps or websites if necessary.
References:
- https://support.apple.com/en-in/105120#:~:text=Tap%20Privacy%20%26%20Security.,then%20enter%20your%20device%20passcode
- https://www.business-standard.com/technology/tech-news/apple-lockdown-mode-what-is-it-and-how-it-prevents-spyware-attacks-124041200667_1.html

THREE CENTRES OF EXCELLENCE IN ARTIFICIAL INTELLIGENCE:
India’s Finance Minister, Mrs. Nirmala Sitharaman, with a vision of ‘Make AI for India’ and ‘Make AI work for India, ’ announced during the presentation of Union Budget 2023 that the Indian Government is planning to set up three ‘Centre of Excellence’ for Artificial Intelligence in top Educational Institutions to revolutionise fields such as health, agriculture, etc.
Under the ‘Amirt Kaal,’ i.e., the budget of 2023 is a stepping stone by the government to have a technology-driven knowledge-based economy and the seven priorities that have been set up by the government called ‘Saptarishi’ such as inclusive development, reaching the last mile, infrastructure investment, unleashing potential, green growth, youth power, and financial sector will guide the nation in this endeavor along with leading industry players that will partner in conducting interdisciplinary research, developing cutting edge applications and scalable problem solutions in such areas.
The government has already formed the roadmap for AI in the nation through MeitY, NASSCOM, and DRDO, indicating that the government has already started this AI revolution. For AI-related research and development, the Centre for Artificial Intelligence and Robotics (CAIR) has already been formed, and biometric identification, facial recognition, criminal investigation, crowd and traffic management, agriculture, healthcare, education, and other applications of AI are currently being used.
Even a task force on artificial intelligence (AI) was established on August 24, 2017. The government had promised to set up Centers of Excellence (CoEs) for research, education, and skill development in robotics, artificial intelligence (AI), digital manufacturing, big data analytics, quantum communication, and the Internet of Things (IoT) and by announcing the same in the current Union budget has planned to fulfill the same.
The government has also announced the development of 100 labs in engineering institutions for developing applications using 5G services that will collaborate with various authorities, regulators, banks, and other businesses.
Developing such labs aims to create new business models and employment opportunities. Among others, it will also create smart classrooms, precision farming, intelligent transport systems, and healthcare applications, as well as new pedagogy, curriculum, continual professional development dipstick survey, and ICT implementation will be introduced for training the teachers.
POSSIBLE ROLES OF AI:
The use of AI in top educational institutions will help students to learn at their own pace, using AI algorithms providing customised feedback and recommendations based on their performance, as it can also help students identify their strengths and weaknesses, allowing them to focus their study efforts more effectively and efficiently and will help train students in AI and make the country future-ready.
The main area of AI in healthcare, agriculture, and sustainable cities would be researching and developing practical AI applications in these sectors. In healthcare, AI can be effective by helping medical professionals diagnose diseases faster and more accurately by analysing medical images and patient data. It can also be used to identify the most effective treatments for specific patients based on their genetic and medical history.
Artificial Intelligence (AI) has the potential to revolutionise the agriculture industry by improving yields, reducing costs, and increasing efficiency. AI algorithms can collect and analyse data on soil moisture, crop health, and weather patterns to optimise crop management practices, improve yields and the health and well-being of livestock, predict potential health issues, and increase productivity. These algorithms can identify and target weeds and pests, reducing the need for harmful chemicals and increasing sustainability.
ROLE OF AI IN CYBERSPACE:
Artificial Intelligence (AI) plays a crucial role in cyberspace. AI technology can enhance security in cyberspace, prevent cyber-attacks, detect and respond to security threats, and improve overall cybersecurity. Some of the specific applications of AI in cyberspace include:
- Intrusion Detection: AI-powered systems can analyse large amounts of data and detect signs of potential cyber-attacks.
- Threat Analysis: AI algorithms can help identify patterns of behaviour that may indicate a potential threat and then take appropriate action.
- Fraud Detection: AI can identify and prevent fraudulent activities, such as identity theft and phishing, by analysing large amounts of data and detecting unusual behaviour patterns.
- Network Security: AI can monitor and secure networks against potential cyber-attacks by detecting and blocking malicious traffic.
- Data Security: AI can be used to protect sensitive data and ensure that it is only accessible to authorised personnel.
CONCLUSION:
Introducing AI in top educational institutions and partnering it with leading industries will prove to be a stepping stone to revolutionise the development of the country, as Artificial Intelligence (AI) has the potential to play a significant role in the development of a country by improving various sectors and addressing societal challenges. Overall, we hope to see an increase in efficiency and productivity across various industries, leading to increased economic growth and job creation, improved delivery of healthcare services by increasing access to care and, improving patient outcomes, making education more accessible and effective as AI has the potential to improve various sectors of a country and contribute to its overall development and progress. However, it’s important to ensure that AI is developed and used ethically, considering its potential consequences and impact on society.


