#FactCheck - Uncovered: Viral LA Wildfire Video is a Shocking AI-Generated Fake!
Executive Summary:
A viral post on X (formerly Twitter) has been spreading misleading captions about a video that falsely claims to depict severe wildfires in Los Angeles similar to the real wildfire happening in Los Angeles. Using AI Content Detection tools we confirmed that the footage shown is entirely AI-generated and not authentic. In this report, we’ll break down the claims, fact-check the information, and provide a clear summary of the misinformation that has emerged with this viral clip.

Claim:
A video shared across social media platforms and messaging apps alleges to show wildfires ravaging Los Angeles, suggesting an ongoing natural disaster.
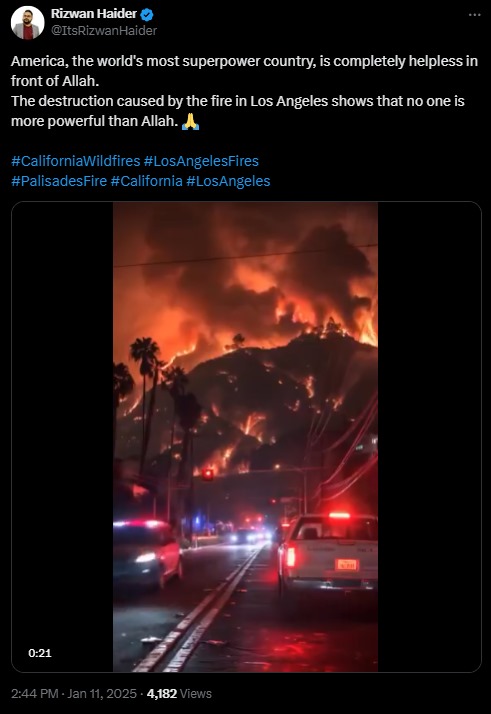
Fact Check:
After taking a close look at the video, we noticed some discrepancy such as the flames seem unnatural, the lighting is off, some glitches etc. which are usually seen in any AI generated video. Further we checked the video with an online AI content detection tool hive moderation, which says the video is AI generated, meaning that the video was deliberately created to mislead viewers. It’s crucial to stay alert to such deceptions, especially concerning serious topics like wildfires. Being well-informed allows us to navigate the complex information landscape and distinguish between real events and falsehoods.

Conclusion:
This video claiming to display wildfires in Los Angeles is AI generated, the case again reflects the importance of taking a minute to check if the information given is correct or not, especially when the matter is of severe importance, for example, a natural disaster. By being careful and cross-checking of the sources, we are able to minimize the spreading of misinformation and ensure that proper information reaches those who need it most.
- Claim: The video shows real footage of the ongoing wildfires in Los Angeles, California
- Claimed On: X (Formerly Known As Twitter)
- Fact Check: Fake Video
Related Blogs

Introduction
The insurance industry is a target for cybercriminals due to the sensitive nature of the information it holds. This makes it essential for insurance companies to have robust cybersecurity measures to protect their data and customers’ personal information.
Cyber fraud in India’s insurance industry is increasing. It is reported that the Indian insurance sector has witnessed a surge in cyber-attacks, with several instances of data breaches, identity thefts, and financial fraud being reported. These cybercrimes not only pose a significant threat to the financial stability of the insurance industry but also to the privacy and security of policyholders.
Cyber Frauds in the Insurance Industry
The insurance industry in India has been the target of increasing cyber fraud in recent years. With the growing digital transformation trend, insurance companies have become increasingly vulnerable to cyber-attacks. Cyber frauds in the insurance industry are initiated by hackers who use various techniques such as phishing, malware, ransomware, and social engineering to gain unauthorised access to policyholders’ personal data and sensitive information
Kinds of cyber frauds in the insurance industry
It is essential for insurers and policyholders alike to be aware of these kinds of cyber-attacks on insurance companies in today’s digital age. Staying educated about these threats can help prevent them from happening in the future.
Identity theft– One common type of cyber fraud that occurs in the insurance industry is identity theft. In this type of fraud, criminals steal personal information such as name, address, date of birth and social security numbers through phishing emails or fraudulent websites. They then use this information to open fraudulent policies or access existing ones.
Payment fraud- Another type of cyber fraud that is on the rise is payment fraud. In this type of fraud, hackers intercept electronic payments made by policyholders or agents using fake bank accounts or compromised payment gateways. The money is then siphoned into untraceable accounts, making it difficult for law enforcement agencies to identify and arrest the perpetrators.
Phishing attacks- Where the fraudsters posed as company officials and sent emails to policyholders requesting their account details. The unsuspecting customers fell for this scam and shared their sensitive information, which was then used to access their accounts and steal funds.
Hacking- Where hackers breach the company’s system to gain access to policyholder data. The hackers’ stoles personal records, including names, addresses, phone numbers, social security numbers, and financial information, which they later sell on the dark web.
Fake policies scam- Fraudsters create fake policies using stolen identities and collect premiums from innocent customers. The insurer then voided these policies due to fraudulent activity leaving those people without valid coverage when they needed it most. The victims suffer significant financial losses due to this scam.
Fake Insurance Websites- Discuss the creation of deceptive websites that imitate well-known insurance companies, where unsuspecting individuals provide their personal details, leading to identity theft or financial losses.

Prevention of Cyber Frauds in the Insurance Industry- Best practices to follow
Prevention is better than cure, which also holds true in the case of cyber fraud in the insurance industry. The industry must take proactive steps to prevent such frauds from occurring in the first place. One of the most effective ways to do so is by investing in cybersecurity measures that are specifically designed for the insurance sector.
Insurance companies must conduct regular employee training programs on cybersecurity best practices. This includes educating employees on how to identify and avoid phishing emails, create strong passwords, and recognise potential cyber threats. Companies should also establish a reporting mechanism for employees to report suspicious activity or incidents immediately.
Having proper access controls in place is also necessary. This means limiting access to sensitive data only to those employees who need it, implementing two-factor authentication, and regularly monitoring user activity logs. Regular audits can also provide an extra layer of protection against potential threats by identifying vulnerabilities that may have been overlooked during routine security checks.
Another essential step is encrypting all data transmitted between different systems and devices. Encryption scrambles data into unreadable codes that can only be deciphered using a decryption key, making it difficult for hackers to intercept or steal information in transit.
Legal Framework for Cyber Frauds in the Insurance Industry
The legal framework for cyber fraud in the insurance industry is critical to preventing such crimes. The Insurance Regulatory and Development Authority of India (IRDAI) has issued guidelines for insurers to establish a cybersecurity framework. The guidelines require insurers to conduct regular risk assessments, implement security measures, and ensure compliance with data privacy laws.
The Information Technology Act 2000, is another significant piece of legislation dealing with cyber fraud in India. The act defines offences such as unauthorised access to a computer system, hacking, and tampering with data. It also provides for stringent penalties and imprisonment for those found guilty of such offences.
The IRDAI’s guidelines provide insurers with a roadmap to establish robust cybersecurity measures to help prevent cyber fraud in the insurance industry. Stringent implementation of these guidelines will go a long way in safeguarding sensitive customer information from falling into the wrong hands.
Best Practices for Insurers and Policyholders
Insurers:
Implementing Strong Authentication: Encouraging the use of multi-factor authentication and secure login processes to safeguard customer accounts and prevent unauthorised access.
Regular Employee Training: Conduct cybersecurity awareness programs to educate employees about the latest threats and preventive measures.
Investing in Advanced Technologies: Utilizing robust cybersecurity tools and systems to promptly detect and mitigate potential cyber threats.
Policyholders:
Vigilance and Awareness: Policyholders must stay vigilant while sharing personal information online and verify the authenticity of insurance websites and communication channels.
Regular Updates and Patches: Advising individuals to keep their devices and software up to date to minimise vulnerabilities that cybercriminals can exploit.
Secure Online Practices: Encouraging the use of strong and unique passwords, avoiding sharing sensitive information on unsecured networks, and exercising caution when clicking on suspicious links or attachments.

Conclusion
As the Indian insurance industry embraces digitisation, the risk of cyber scams and data breaches becomes a significant concern. Insurers and policyholders must collaborate to ensure robust cybersecurity measures are in place to protect sensitive information and financial interests.
It is essential for insurance companies to invest in robust cybersecurity measures that can detect and prevent fraud attempts. Additionally, educating employees on the dangers of cyber fraud and implementing strict compliance measures can go a long way in mitigating risks. With these efforts, the insurance industry can continue to provide trustworthy and reliable services to its customers while protecting against cyber threats. As technology continues to evolve, it is imperative that the insurance industry adapts accordingly and remains vigilant against emerging threats.

Introduction
Entrusted with the responsibility of leading the Global Education 2030 Agenda through the Sustainable Development Goal 4, UNESCO’s Institute for Lifelong Learning in collaboration with the Media and Information Literacy and Digital Competencies Unit has recently launched a Media and Information Literacy Course for Adult Educators. The course aligns with The Pact for The Future adopted at The United Nations Summit of the Future, September 2024 - asking for increased efforts towards media and information literacy from its member countries. The course is free for Adult Educators to access and is available until 31st May 2025.
The Course
According to a report by Statista, 67.5% of the global population uses the internet. Regardless of the age and background of the users, there is a general lack of understanding on how to spot misinformation, targeted hate, and navigating online environments in a manner that is secure and efficient. Since misinformation (largely spread online) is enabled by the lack of awareness, digital literacy becomes increasingly important. The course is designed keeping in mind that many active adult educators are yet to get an opportunity to hone their skills with regard to media and information through formal education. Self-paced, a total of 10 hours, this course covers basics such as concepts of misinformation and disinformation, artificial intelligence, and combating hate speech, and offers a certificate on completion.
CyberPeace Recommendations
As this course is free of cost, can be done in a remote capacity, and covers basics regarding digital literacy, all eligible are encouraged to take it up to familiarise themselves with such topics. However, awareness regarding the availability of this course, alongside who can avail of this opportunity can be further worked on so a larger number can avail its benefits.
CyberPeace Recommendations To Enhance Positive Impact
- Further Collaboration: As this course is open to adult educators, one can consider widening the scope through active engagement with Independent organisations and even Individual internet users who are willing to learn.
- Engagement with Educational Institutions: After launching a course, an interactive outreach programme and connecting with relevant stakeholders can prove to be beneficial. Since this course requires each individual adult educator to sign up to avail the course, partnering with educational universities, institutes, etc. is encouraged. In the Indian context, active involvement with training institutes such as DIET (District Institute of Education and Training), SCERT (State Council of Educational Research and Training), NCERT (National Council of Educational Research and Training), and Open Universities, etc. could be initiated, facilitating greater awareness and more participation.
- Engagement through NGOs: NGOs (focused on digital literacy) with a tie-up with UNESCO, can aid in implementing and encouraging awareness. A localised language approach option can be pondered upon for inclusion as well.
Conclusion
Though a long process, tackling misinformation through education is a method that deals with the issue at the source. A strong foundation in awareness and media literacy is imperative in the age of fake news, misinformation, and sensitive data being peddled online. UNESCO’s course launch garners attention as it comes from an international platform, is free of cost, truly understands the gravity of the situation, and calls for action in the field of education, encouraging others to do the same.
References
- https://www.uil.unesco.org/en/articles/media-and-information-literacy-course-adult-educators-launched
- https://www.unesco.org/en/articles/celebrating-global-media-and-information-literacy-week-2024
- https://www.unesco.org/en/node/559#:~:text=UNESCO%20believes%20that%20education%20is,must%20be%20matched%20by%20quality.
.webp)
Introduction
The rise of unreliable social media newsgroups on online platforms has significantly altered the way people consume and interact with news, contributing to the spread of misinformation and leading to sources of unverified and misleading content. Unlike traditional news outlets that adhere to journalistic standards, these newsgroups often lack proper fact-checking and editorial oversight, leading to the rapid dissemination of false or distorted information. Social media transformed individuals into active content creators. Social media newsgroups (SMNs) are social media platforms used as sources of news and information. According to a survey by the Pew Research Center (July-August 2024), 54% of U.S. adults now rely on social media for news. This rise in SMNs has raised concerns over the integrity of online news and undermines trust in legitimate news sources. Social media users are advised to consume information and news from authentic sources or channels available on social media platforms.
The Growing Issue of Misinformation in Social Media Newsgroups
Social media newsgroups have become both a source of vital information and a conduit for misinformation. While these platforms allow rapid news sharing and facilitate political and social campaigns, they also pose significant risks of unverified information. Misleading information, often driven by algorithms designed to maximise user engagement, proliferates in these spaces. This has led to increasing challenges, as SMNs cater to diverse communities with varying political affiliations, gender demographics, and interests. This sometimes results in the creation of echo chambers where information is not critically assessed, amplifying the confirmation bias and enabling the unchecked spread of misinformation. A prominent example is the false narratives surrounding COVID-19 vaccines that spread across SMNs, contributing to widespread vaccine hesitancy and public health risks.
Understanding the Susceptibility of Online Newsgroups to Misinformation
Several factors make social media newsgroups particularly susceptible to misinformation. Some of the factors are listed below:
- The lack of robust fact-checking mechanisms in social media news groups can lead to false narratives which can spread easily.
- The lack of expertise from admins of online newsgroups, who are often regular users without journalism knowledge, can result in the spreading of inaccurate information. Their primary goal of increasing engagement may overshadow concerns about accuracy and credibility.
- The anonymity of users exacerbates the problem of misinformation. It allows users to share unverified or misleading content without accountability.
- The viral nature of social media also leads to the vast spread of misinformation to audiences instantly, often outpacing efforts to correct it.
- Unlike traditional media outlets, online newsgroups often lack formal fact-checking processes. This absence allows misinformation to circulate without verification, making it easier for inaccuracies to go unchallenged.
- The sheer volume of user engagement in the form of posts has created the struggle to moderate content effectively imposing significant challenges.
- Social Media Platforms have algorithms designed to enhance user engagement and inadvertently amplify sensational or emotionally charged content, which is more likely to be false.
Consequences of Misinformation in Newsgroups
The societal impacts of misinformation in SMNs are profound. Political polarisation can fuel one-sided views and create deep divides in democratic societies. Health risks emerge when false information spreads about critical issues, such as the anti-vaccine movements or misinformation related to public health crises. Misinformation has dire long-term implications and has the potential to destabilise governments and erode trust in media, in both traditional and social media leading to undermining democracy. If unaddressed, the consequences could continue to ripple through society, perpetuating false narratives that shape public opinion.
Steps to Mitigate Misinformation in Social Media Newsgroups
- Educating users in social media literacy education can empower critical assessment of the information encountered, reducing the spread of false narratives.
- Introducing stricter platform policies, including penalties for deliberately sharing misinformation, may act as a deterrent against sharing unverified information.
- Collaborative fact-checking initiatives with involvement from social media platforms, independent journalists, and expert organisations can provide a unified front against the spread of false information.
- From a policy perspective, a holistic approach that combines platform responsibility with user education and governmental and industry oversight is essential to curbing the spread of misinformation in social media newsgroups.
Conclusion
The emergence of Social media newsgroups has revolutionised the dissemination of information. This rapid spread of misinformation poses a significant challenge to the integrity of news in the digital age. It gets further amplified by algorithmic echo chambers unchecked user engagement and profound societal implications. A multi-faceted approach is required to tackle these issues, combining stringent platform policies, AI-driven moderation, and collaborative fact-checking initiatives. User empowerment concerning media literacy is an important factor in promoting critical thinking and building cognitive defences. By adopting these measures, we can better navigate the complexities of consuming news from social media newsgroups and preserve the reliability of online information. Furthermore, users need to consume news from authoritative sources available on social media platforms.


