#FactCheck - Viral Video Showing Man Frying Bhature on His Stomach Is AI-Generated
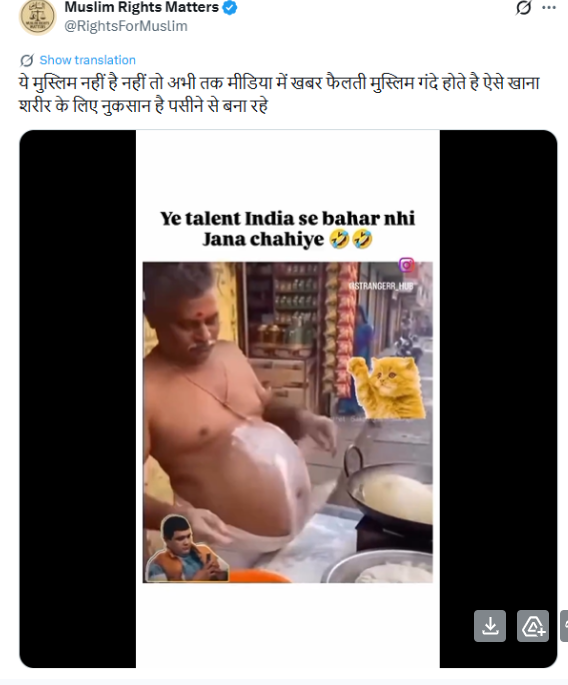
A video circulating on social media shows a man allegedly rolling out bhature on his stomach and then frying them in a pan. The clip is being shared with a communal narrative, with users making derogatory remarks while falsely linking the act to a particular community.
CyberPeace Foundation’s research found the viral claim to be false. Our probe confirms that the video is not real but has been created using artificial intelligence (AI) tools and is being shared online with a misleading and communal angle.
Claim
On January 5, 2025, several users shared the viral video on social media platform X (formerly Twitter). One such post carried a communal caption suggesting that the person shown in the video does not belong to a particular community and making offensive remarks about hygiene and food practices..
- The post link and archived version can be viewed here: https://x.com/RightsForMuslim/status/2008035811804291381
- Archive Link: https://archive.ph/lKnX5
Fact Check:
Upon closely examining the viral video, several visual inconsistencies and unnatural movements were observed, raising suspicion about its authenticity. These anomalies are commonly associated with AI-generated or digitally manipulated content.
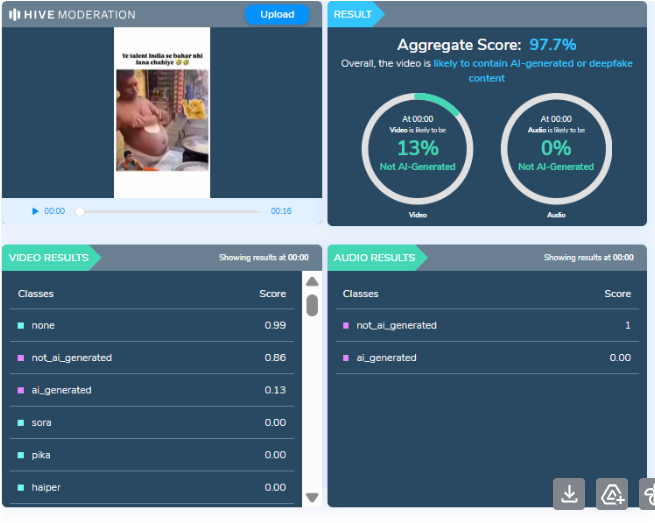
To verify this, the video was analysed using the AI detection tool HIVE Moderation. According to the tool’s results, the video was found to be 97 percent AI-generated, strongly indicating that it was not recorded in real life but synthetically created.
Conclusion
CyberPeace Foundation’s research clearly establishes that the viral video is AI-generated and does not depict a real incident. The clip is being deliberately shared with a false and communal narrative to mislead users and spread misinformation on social media. Users are advised to exercise caution and verify content before sharing such sensational and divisive material online.
Related Blogs
.webp)
Introduction
The Senate bill introduced on 19 March 2024 in the United States would require online platforms to obtain consumer consent before using their data for Artificial Intelligence (AI) model training. If a company fails to obtain this consent, it would be considered a deceptive or unfair practice and result in enforcement action from the Federal Trade Commission (FTC) under the AI consumer opt-in, notification standards, and ethical norms for training (AI Consent) bill. The legislation aims to strengthen consumer protection and give Americans the power to determine how their data is used by online platforms.
The proposed bill also seeks to create standards for disclosures, including requiring platforms to provide instructions to consumers on how they can affirm or rescind their consent. The option to grant or revoke consent should be made available at any time through an accessible and easily navigable mechanism, and the selection to withhold or reverse consent must be at least as prominent as the option to accept while taking the same number of steps or fewer as the option to accept.
The AI Consent bill directs the FTC to implement regulations to improve transparency by requiring companies to disclose when the data of individuals will be used to train AI and receive consumer opt-in to this use. The bill also commissions an FTC report on the technical feasibility of de-identifying data, given the rapid advancements in AI technologies, evaluating potential measures companies could take to effectively de-identify user data.
The definition of ‘Artificial Intelligence System’ under the proposed bill
ARTIFICIALINTELLIGENCE SYSTEM- The term artificial intelligence system“ means a machine-based system that—
- Is capable of influencing the environment by producing an output, including predictions, recommendations or decisions, for a given set of objectives; and
- 2. Uses machine or human-based data and inputs to
(i) Perceive real or virtual environments;
(ii) Abstract these perceptions into models through analysis in an automated manner (such as by using machine learning) or manually; and
(iii) Use model inference to formulate options for outcomes.
Importance of the proposed AI Consent Bill USA
1. Consumer Data Protection: The AI Consent bill primarily upholds the privacy rights of an individual. Consent is necessitated from the consumer before data is used for AI Training; the bill aims to empower individuals with unhinged autonomy over the use of personal information. The scope of the bill aligns with the greater objective of data protection laws globally, stressing the criticality of privacy rights and autonomy.
2. Prohibition Measures: The proposed bill intends to prohibit covered entities from exploiting the data of consumers for training purposes without their consent. This prohibition extends to the sale of data, transfer to third parties and usage. Such measures aim to prevent data misuse and exploitation of personal information. The bill aims to ensure companies are leveraged by consumer information for the development of AI without a transparent process of consent.
3. Transparent Consent Procedures: The bill calls for clear and conspicuous disclosures to be provided by the companies for the intended use of consumer data for AI training. The entities must provide a comprehensive explanation of data processing and its implications for consumers. The transparency fostered by the proposed bill allows consumers to make sound decisions about their data and its management, hence nurturing a sense of accountability and trust in data-driven practices.
4. Regulatory Compliance: The bill's guidelines call for strict requirements for procuring the consent of an individual. The entities must follow a prescribed mechanism for content solicitation, making the process streamlined and accessible for consumers. Moreover, the acquisition of content must be independent, i.e. without terms of service and other contractual obligations. These provisions underscore the importance of active and informed consent in data processing activities, reinforcing the principles of data protection and privacy.
5. Enforcement and Oversight: To enforce compliance with the provisions of the bill, robust mechanisms for oversight and enforcement are established. Violations of the prescribed regulations are treated as unfair or deceptive acts under its provisions. Empowering regulatory bodies like the FTC to ensure adherence to data privacy standards. By holding covered entities accountable for compliance, the bill fosters a culture of accountability and responsibility in data handling practices, thereby enhancing consumer trust and confidence in the digital ecosystem.
Importance of Data Anonymization
Data Anonymization is the process of concealing or removing personal or private information from the data set to safeguard the privacy of the individual associated with it. Anonymised data is a sort of information sanitisation in which data anonymisation techniques encrypt or delete personally identifying information from datasets to protect data privacy of the subject. This reduces the danger of unintentional exposure during information transfer across borders and allows for easier assessment and analytics after anonymisation. When personal information is compromised, the organisation suffers not just a security breach but also a breach of confidence from the client or consumer. Such assaults can result in a wide range of privacy infractions, including breach of contract, discrimination, and identity theft.
The AI consent bill asks the FTC to study data de-identification methods. Data anonymisation is critical to improving privacy protection since it reduces the danger of re-identification and unauthorised access to personal information. Regulatory bodies can increase privacy safeguards and reduce privacy risks connected with data processing operations by investigating and perhaps implementing anonymisation procedures.
The AI consent bill emphasises de-identification methods, as well as the DPDP Act 2023 in India, while not specifically talking about data de-identification, but it emphasises the data minimisation principles, which highlights the potential future focus on data anonymisation processes or techniques in India.
Conclusion
The proposed AI Consent bill in the US represents a significant step towards enhancing consumer privacy rights and data protection in the context of AI development. Through its stringent prohibitions, transparent consent procedures, regulatory compliance measures, and robust enforcement mechanisms, the bill strives to strike a balance between fostering innovation in AI technologies while safeguarding the privacy and autonomy of individuals.
References:
- https://fedscoop.com/consumer-data-consent-training-ai-models-senate-bill/#:~:text=%E2%80%9CThe%20AI%20CONSENT%20Act%20gives,Welch%20said%20in%20a%20statement
- https://www.dataguidance.com/news/usa-bill-ai-consent-act-introduced-house#:~:text=USA%3A%20Bill%20for%20the%20AI%20Consent%20Act%20introduced%20to%20House%20of%20Representatives,-ConsentPrivacy%20Law&text=On%20March%2019%2C%202024%2C%20US,the%20U.S.%20House%20of%20Representatives
- https://datenrecht.ch/en/usa-ai-consent-act-vorgeschlagen/
- https://www.lujan.senate.gov/newsroom/press-releases/lujan-welch-introduce-billto-require-online-platforms-receive-consumers-consent-before-using-their-personal-data-to-train-ai-models/

Introduction
The two-day Apple’s Worldwide Developer Conference (WWDC) 2023, which was held on the 6th & 7th of June, has become an essential and highly anticipated part of our calendar as frequently as the trend. This year’s keynote announcements will include all of the usual enhancements for iOS, iPadOS, watchOS, macOS, and more. However, this year is also unique due to the unveiling of the Vision Pro headset, a brand-new Apple product.
In this blog, we will examine the exciting announcements made at Apple WWDC 2023, which was a ground-breaking event.
macOS Sonoma
macOS Sonoma, the new presentation of macOS disclosed at the WWDC full of exciting features. It comes with stunning video screensavers that show stunning scenes from all over the world. Gadgets can now be added genuinely to the work area and adjusted totally based on the client’s action. Also, it changes variety and blurring out of the spotlight while utilising applications. In addition, Death Stranding: Directors Cut for Mac announced that the Game Mode is added to make Macs more suitable for gaming. A presenter overlay enhances video presentations, and viewers can respond to them with interactive responses. Updated Safari is also included in the WebApp feature that turns frequently used websites into dedicated windows, a new Profile system for separating browsing history, and secure password sharing. Currently, the developer beta is available and the public beta will be available in July, and the final release is anticipated for the fall.
ios 16
Apple WWDC 2023 shows the following iOS, and iOS 16 replication, offering plenty of energising highlights for iPhone and iPad clients. Apple maintains its commitment to privacy with iOS 16, which introduces enhanced privacy settings that give users even more control over their data and online privacy. Users can also personalise their devices according to their preferences thanks to the new operating system’s refinement and customisable user interface.Improved multitasking capabilities like redesigned Files app and advanced note-taking features are just a few of the productivity enhancements included in the iOS 16. With iOS 16, Apple also improves its AR capabilities, allowing developers to develop even more immersive and interactive AR experiences.

WatchOS 9
Apple WWDC 2023 carried energising updates to the Apple Watch with the presentation of watchOS 9. The Apple Watch is an essential companion for sustaining a healthy lifestyle because the most recent version of the operating system includes cutting-edge health and fitness features. WatchOS 9 gives users unprecedented control over their health, offering personalised fitness recommendations and advanced sleep tracking.
Additionally, new watch faces were added, enhancing communication capabilities and improving app performance in watchOS 9, making the Apple Watch even easier to use daily.
ios 17
Rather than focusing on major features, Apple focused on quality-of-life enhancements when it announced iOS 17 at WWDC 2023. Live Voicemail with real-time transcripts of voicemails, personalised personal contact “posters,” and video voicemails for FaceTime are all part of the update. Search filters, a catch-up arrow, live location sharing, and a safety feature called Check-In are all available in Messages. AirDrop now supports NameDrop for transferring contact information; stickers have been expanded. The autocorrect and recording features on the keyboard have been improved for accuracy. Standby in the lock screen is an intelligent home display that shows the weather, upcoming appointments, and notifications. Siri works on Standby and adjusts itself for the night. The developer beta is currently available now, and a public beta will take place next month before the full release is in the fall.
Vision Pro VR Headset
Apple unveiled the Vision Pro AR headset, their first foray into virtual reality (VR), during the WWDC keynote. The Vision Pro is a virtual reality headset that competes with PlayStation VR2 and Meta Quest 3. This is in contrast to the long-awaited Apple smart glasses. Apple put a lot of effort into making a thin and light headset by using premium materials when needed. Voice, hand, and eye commands are all used to operate the Digital Crown-equipped device. The showcases offer extraordinary clarity, which is fueled by Apple’s M2 processor with a committed R1 chip. The Vision Pro combines virtual reality (VR) and augmented reality (AR), enabling users to interact with Apple apps and gain access to the company’s existing ecosystem. The expanded reality space created by the headset’s sensors and cameras allows users to place apps in real-world environments and adjust their level of concentration. Optic ID is a security and unlocking eye-tracking technology that is incorporated into the Vision Pro. It allows for a more immersive screen experience because it is compatible with Apple accessories like Magic Keyboard and Mac. At launch, the Vision Pro supports over a hundred Apple game galleries. Disney gave a hint that Apple and Disney might work together in the future by announcing support for the Vision Pro and making the Disney Plus app available immediately. The show highlighted the headset’s lightweight plan and recommended Apple clients wear it for extended periods. However, widespread adoption may be difficult due to the high price of $3,499 (₹289,093.01 approx). Apple is expected to release the Vision Pro for public use in 2024.

15-inch MacBook Air
At the WWDC event, Apple revealed a new MacBook Air with a larger 15-inch model instead of the standard 13-inch model. The 15-inch MacBook Air features a powerful Apple M2 processor, a thin, light, and long-lasting design, and a stunning 15.3-inch Retina display. It comes in four colours and has a headphone jack, two USB-C ports, and MagSafe charging. The display has six spatial speakers, a 1080p webcam, and 500 nits of brightness. Apple claims a battery life of up to 18 hours.
Conclusion
At Apple’s 2023 WWDC, the company demonstrated its commitment to developing technology that is user-friendly and accessible to all. Apple’s commitment to improving the user experience across all of its products is demonstrated in the updates to operating systems, improvements of Siri, breakthroughs in augmented reality, and enhancements to health and fitness.By making complex innovations more like-minded and easy to understand, Apple is enabling people to use the maximum capacity of their gadgets. Apple’s innovations at WWDC 2023 are expected to shape the future of technology, simplifying everyday tasks and revolutionising how we interact with the digital world.As we push ahead, it is exciting to guess what these advancements will proceed to develop and decidedly mean for our lives. The future holds even more incredible possibilities for all of us because of Apple’s focus on privacy, user-centric design, and pushing the boundaries of innovation. Thus, prepare to embrace a future where innovation flawlessly incorporates into our lives because of the endeavours displayed at Apple WWDC 2023.

A video purportedly showing Prime Minister Narendra Modi delivering a politically charged warning during a public address has been widely circulated on social media. The clip is being shared with claims that the Prime Minister spoke about the “saffronisation” of the Indian Army and issued a stern message to Bangladesh by invoking India’s role in the 1971 war.
A detailed verification by the CyberPeace Foundation found these claims to be misleading. The investigation revealed that the viral video has been digitally altered, and the statements attributed to the Prime Minister do not appear in the original speech. The misleading narrative appears to have been created by inserting manipulated audio into authentic video footage.
Claim
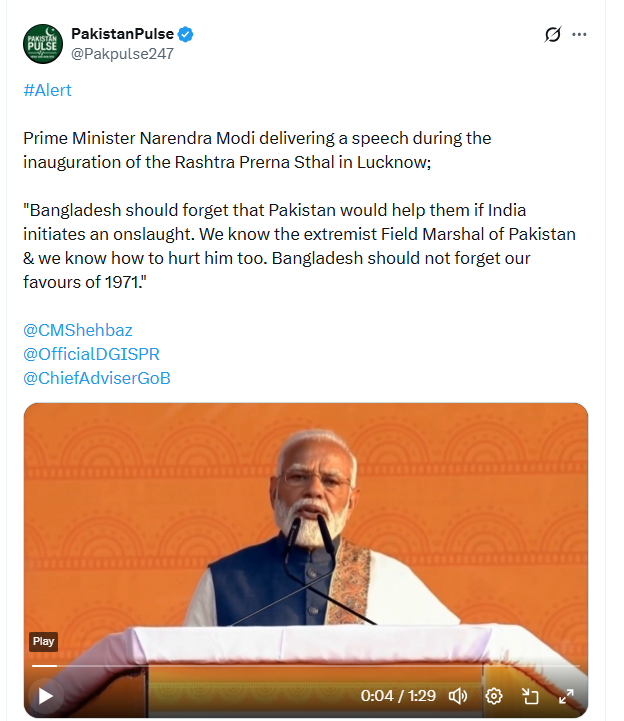
An X user, “@Pakpulse247,” shared a video on December 26 claiming that Prime Minister Narendra Modi, while addressing a public gathering, made remarks about the “saffronisation” of the Indian Army and issued a warning to Bangladesh by invoking India’s role in the 1971 war.
The post’s caption alleged that the Prime Minister made these statements during the inauguration of the Rashtra Prerna Sthal in Lucknow, suggesting that Bangladesh should not expect support from Pakistan in the event of an Indian offensive and should remember India’s contribution during the 1971 conflict.
The link to the post is provided below, along with a screenshot of the viral claim.
Fact Check:
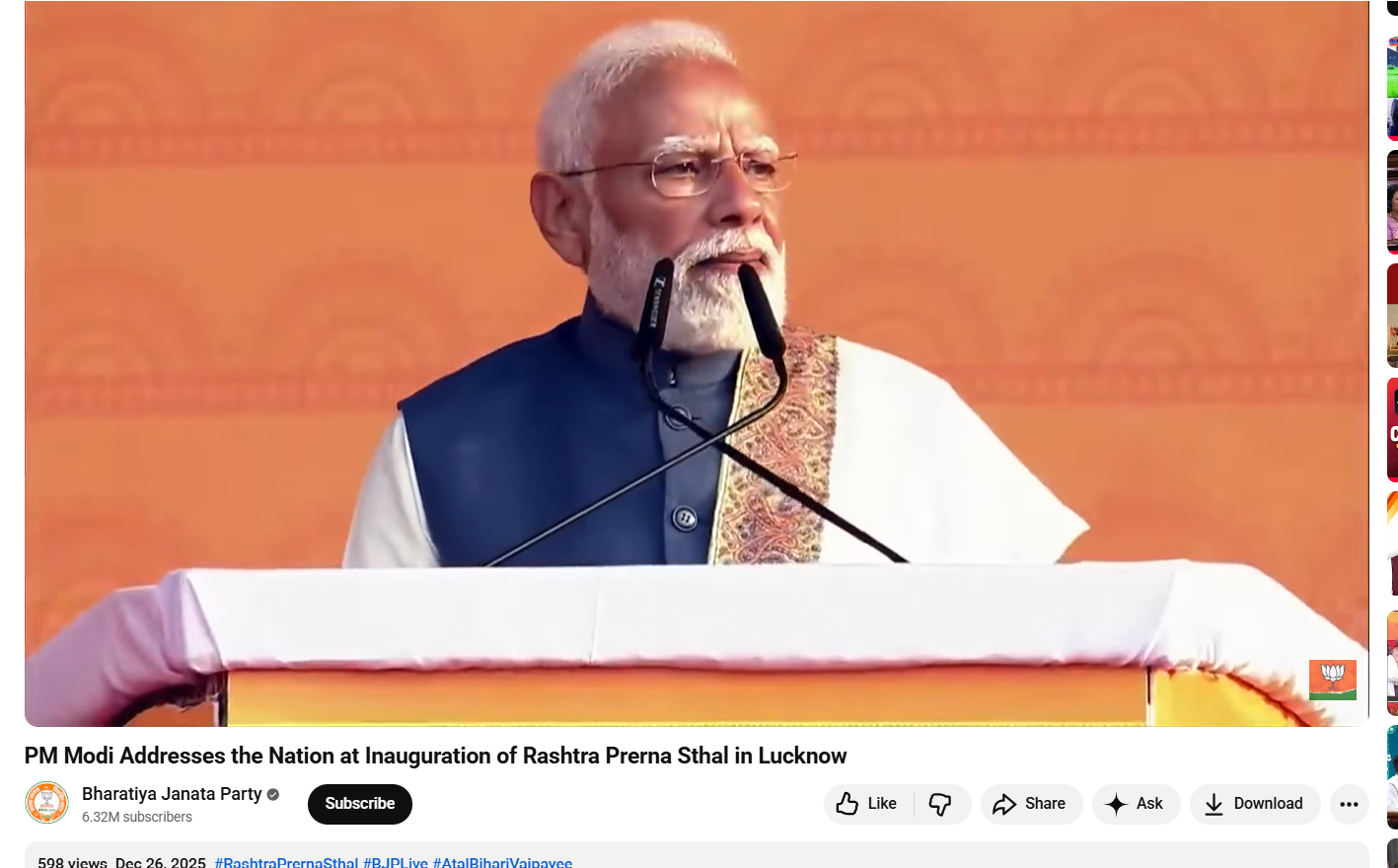
During the verification process, the Desk carried out a targeted keyword search and located the complete, original version of the video on the official YouTube channel of the Bharatiya Janata Party, uploaded on December 26, 2025. The video description confirmed that Prime Minister Narendra Modi was addressing the gathering at the inauguration of the Rashtra Prerna Sthal in Lucknow.
A comparison of the visuals showed that the venue, backdrop, and the Prime Minister’s attire were identical to those seen in the viral clip circulating on social media. However, after carefully reviewing the full speech, the Desk found no reference to Pakistan, Bangladesh, or the claims being attributed to him in the viral post.
The link to the original video is provided below, along with a relevant screenshot.
https://www.youtube.com/watch?v=L9rbzU0m30o
Upon further examination of the search results, the Desk located the official English transcript of Prime Minister Narendra Modi’s speech on the PM India website. A thorough review of the complete transcript revealed no mention of the statements attributed to him in the viral social media post.
The link to the official transcription is provided below.
On further examination of the search results, the Desk accessed the official English transcript of Prime Minister Narendra Modi’s speech published on the PM India website. A careful review of the complete transcript confirmed that none of the claims made in the viral social media post appear in the official record.
The link to the transcription is provided below.
Building on these findings, the Desk extracted the audio track from the viral video and analysed it using Resemble AI, an audio-detection tool. The analysis flagged the audio as fake, indicating that it had been digitally manipulated.
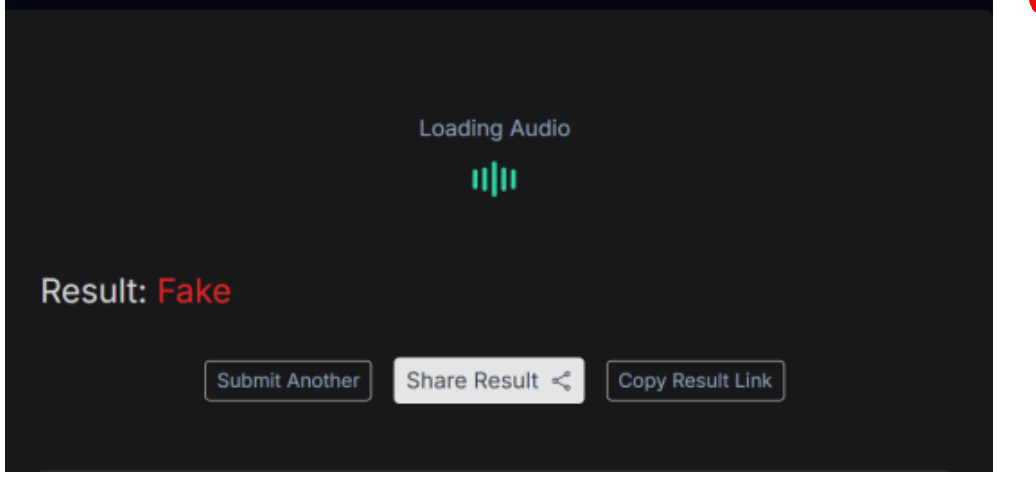
Conclusion
The CyberPeace Foundation’s research clearly establishes that the viral video claiming Prime Minister Narendra Modi made remarks about the saffronisation of the Indian Army and issued warnings to Bangladesh is false and misleading. The full original video and official transcript of the speech contain no such references to Pakistan, Bangladesh, or the 1971 war. Furthermore, audio analysis using AI-detection tools confirms that the voice in the viral clip has been digitally manipulated.


