#FactCheck - Viral video attributed to the Australian Prime Minister is AI-generated; claim of cancelling Pakistani visas is false
A video is being shared on social media, falsely attributing it to Australian Prime Minister Anthony Albanese. The video claims that following the Bondi Beach attack, he decided to cancel the visas of Pakistani citizens.
An investigation by the Cyber Peace Foundation revealed that the viral video was created using AI. In the original video, Anthony Albanese was answering questions related to the Climate Change Bill during a press conference. It is important to note that in the attack that took place last Sunday (14 December) at Bondi Beach in Sydney, New South Wales, Australia, 15 people were killed. According to Australian police, the attack targeted the Jewish community. New South Wales Police Commissioner Mal Lanyon stated that the two accused involved in the attack were father and son—one aged 50 and the other 24. Media reports identified them as Sajid and Naved Akram.
Claim:
On 14 December 2025, a user on the social media platform X shared a video claiming, “After the attack by a Pakistani Islamic terrorist, the Australian Prime Minister has decided to cancel the visas of all Pakistanis. The whole world is troubled by this community, and in India it is said that Abdul cannot buy a house in a Hindu neighbourhood.”
The link to the related post, its archived version, and screenshots can be seen below:
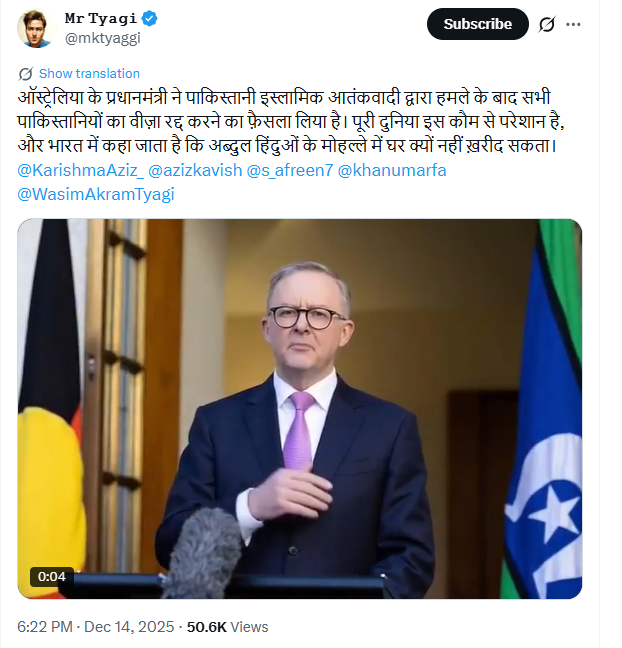
Investigation:Upon closely examining the viral video, we suspected it to be AI-generated. Subsequently, we scanned the video using the AI detection tool aurigin.ai. According to the results provided by the tool, the video was found to be AI-generated.
Related Blogs

Introduction
The much-awaited DPDP Rules have now finally been released in the official Gazette on 3rd January 2025 for consultation. The draft Digital Personal Data Protection Rules, 2025 (DPDP Rules) invites objections and suggestions from stakeholders that can be submitted on MyGov (https://mygov.in) by 18th February 2025.
DPDP Rules at Glance
- Processing of Children's Data: The draft rules say that ‘A Data Fiduciary shall adopt appropriate technical and organisational measures to ensure that verifiable consent of the parent is obtained before the processing of any personal data of a child’. It entails that children below 18 will need parents' consent to create social media accounts.
- The identity of the parents and their age can be verified through reliable details of identity and age available with the Data Fiduciary, voluntarily provided identity proof or virtual token mapped to the same. The data fiduciaries are also required to observe due diligence for checking that the individual identifying themselves as the parent is an adult who is identifiable, if required, in connection with compliance with any law for the time being in force in India. Additionally, the government will also extend exemptions from these specific provisions pertaining to processing of children's data to educational institutions, and child welfare organisations.
- Processing of Personal Data Outside India: The draft rules specify that the transfer of personal data outside India, whether it is processed within the country or outside in connection with offering goods or services to individuals in India, is permitted only if the Data Fiduciary complies with the conditions prescribed by the Central Government through general or specific orders.
- Intimation of Personal Data Breach: On becoming aware of a personal data breach, the Data Fiduciary must promptly notify the affected Data Principals in a clear and concise manner through their user account or registered communication method. This notification should include a description of the breach (nature, extent, timing, and location), potential consequences for the Data Principal, measures taken or planned to mitigate risks, recommended safety actions for the Data Principal, and contact information of a representative to address queries. Additionally, the Data Fiduciary must inform the Board without delay, providing details of the breach, its likely impact, and initial findings. Within 72 hours (or a longer period allowed by the Board upon request), the Data Fiduciary must submit updated information, including the facts and circumstances of the breach, mitigation measures, findings about the cause, steps to prevent recurrence, and a report on notifications given to affected Data Principals.
- Data Protection Board: The draft rules propose establishing the Data Protection Board, which will function as a digital office, enabling remote hearings, and will hold powers to investigate breaches, impose penalties, and perform related regulatory functions.
Journey of Digital Personal Data Protection Act, 2023
The foundation for the single statute legislation on Data Protection was laid down in 2017, in the famous ‘Puttaswami judgment,’ which is also well recognised as the Aadhar Card judgment. In this case, ‘privacy’ was recognised as intrinsic to the right to life and personal liberty, guaranteed by Article 21 of the Constitution of India, thus making ‘Right to Privacy’ a fundamental right. In the landmark Puttaswamy ruling, the apex court of India stressed the need for a comprehensive data protection law.
Eight years on and several draft bills later, the Union Cabinet approved the Digital Personal Data Protection Bill (DPDP) on 5th July 2023. The bill was tabled in the Lok Sabha on 3rd August 2023, and It was passed by Lok Sabha on 7th August, and the bill passed by Rajya Sabha on 9th August and got the president's assent on 11th August 2023; and India finally came up with the ‘Digital Personal Data Protection Act, 2023. This is a significant development that has the potential to bring about major improvements to online privacy and the handling of digital personal data by the platforms.
The Digital Personal Data Protection Act, 2023, is a newly-enacted legislation designed to protect individuals' digital personal data. It aims to ensure compliance by Data Fiduciaries and imposes specific obligations on both Data Principals and Data Fiduciaries. The Act promotes consent-based data collection practices and establishes the Data Protection Board to oversee compliance and address grievances. Additionally, it includes provisions for penalties of up to ₹250 crores in the event of a data breach. However, despite the DPDP Act being passed by parliament last year, the Act has not yet taken effect since its rules and regulations are still not finalised.
Conclusion
It is heartening to see that the Ministry of Electronics and Technology (MeitY) has finally released the draft of the much-awaited DPDP rules for consultation from stakeholders. Though noting certain positive aspects, there is still room for addressing certain gaps and multiple aspects under the draft rules that require attention. The public consultation, including the inputs from the tech platforms, is likely to see critical inputs on multiple aspects under the proposed rules. One such key area of interest will be the requirement of verifiable parental consent, which will likely include recommendations for a balanced approach which maintains children’s safety and mechanisms for the requirement of verifiable consent. The Provisions permitting government access to personal data on grounds of national security are also expected to face scrutiny. The proposed rules, after the consultation process, will be taken into consideration for finalisation after 18th February 2025. The move towards establishing a robust data protection law in India signals a significant step toward enhancing trust and accountability in the digital ecosystem. However, its success will hinge on effective implementation, clear compliance mechanisms, and the adaptability of stakeholders to this evolving regulatory landscape.
References

Introduction:
CDR is a term that refers to Call detail records, The Telecom Industries holds the call details data of the users. As it amounts to a large amount of data, the telecom companies retain the data for a period of 6 months. CDR plays a significant role in investigations and cases in the courts. It can be used as pivotal evidence in court proceedings to prove or disprove certain facts & circumstances. Power of Interception of Call detail records is allowed for reasonable grounds and only by the authorized authority as per the laws.
Admissibility of CDR’s in Courts:
Call Details Records (CDRs) can be used as effective pieces of evidence to assist the court in ascertaining the facts of the particular case and inquiring about the commission of an offence, and according to the judicial pronouncements, it is made clear that CDRs can be used supporting or secondary evidence in the court. However, it cannot be the sole basis of the conviction. Section 92 of the Criminal Procedure Code 1973 provides procedure and empowers certain authorities to apply for court or competent authority intervention to seek the CDR.
Legal provisions to obtain CDR:
The CDR can be obtained under the statutory provisions of law contained in section 92 Criminal Procedure Code, 1973. Or under section 5(2) of Indian Telegraph Act 1885, read with rule 419(A) Indian Telegraph Amendment rule 2007. The guidelines were also issued in 2016 by Ministry of Ministry of Home Affairs for seeking Call details records (CDRs)
How long is CDR stored with telecom Companies (Data Retention)
Call Data is retained by telecom companies for a period of 6 months. As the data amounts to high storage, almost several Petabytes per year, telecom companies store the call details data for a period of 6 months and archive the rest of it to tapes.
New Delhi 25Cr jewellery heist
Recently, an incident took place where a 25-crore jewellery theft was carried out in a jewellery shop in Delhi, It was planned and executed by a man from Chhattisgarh. After committing the crime, the criminal went back to Chhattisgarh. It was a case of a 25Cr heist, and the police started their search & investigation. Police used technology and analysed the mobile numbers which were active at the crime scene. Delhi police used advanced software to analyse data. The police were able to trace the mobile number of thieves or suspects active at the crime scene. They discovered suspected contacts who were active within the range of the crime scene, and it helped in the arrest of the main suspects. From around 5,000 mobile numbers active around the crime scene, police have used advanced software that analyses huge data, and then police found a number registered outside of Delhi. The surveillance on the number has revealed that the suspected criminal has moved to the MP from Delhi, then moved further to Bhilai Chattisgarh. Police have successfully arrested the suspected criminal. This incident highlights how technology or call data can assist law enforcement agencies in investigating and finding the real culprits.
Conclusion:
CDR refers to call detail records retained by telecom companies for a period of 6 months, it can be obtained through lawful procedure and by competent authorities only. CDR can be helpful in cases before the court or law enforcement agencies, to assist the court and law enforcement agencies in ascertaining the facts of the case or to prove or disprove certain things. It is important to reiterated that unauthorized seeking of CDR is not allowed; the intervention of the court or competent authority is required to seek the CDR from the telecom companies. CDRs cannot be unauthorizedly obtained, and there has to be a directive from the court or competent authority to do so.
References:
- https://indianlegalsystem.org/cdr-the-wonder-word/#:~:text=CDR%20is%20admissible%20as%20secondary,the%20Indian%20Evidence%20Act%2C%201872.
- https://timesofindia.indiatimes.com/city/delhi/needle-in-a-haystack-how-cops-scanned-5k-mobile-numbers-to-crack-rs-25cr-heist/articleshow/104055687.cms?from=mdr
- https://www.ndtv.com/delhi-news/just-one-man-planned-executed-rs-25-crore-delhi-heist-another-thief-did-him-in-4436494
.webp)
Introduction
As per the National Crime Records Bureau (NCRB) ‘Cyber Crime In India Report 2022’, A total of 65,893 cases were registered under Cyber Crimes, showing an increase of 24.4% in registration in comparison to 52,974 cases registered in 2021. The crime rate increased from 3.9 in 2021 to 4.8 in 2022. During 2022, 64.8% of cyber-crime cases registered were for the motive of fraud (42,710 out of 65,893 cases), followed by Extortion with 5.5% (3,648 cases) and Sexual Exploitation with 5.2% (3,434 cases). The statistics released by NCRB show the increased rate of cyber crimes in the country, which poses a significant question of safety in the online world. The rise in cybercrime indicates a rise in emerging criminal groups with malicious intentions, creating new cybercrime hotspots in the country where these groups target and commit cyber crimes despite limited resources.
Cyber Crime Hotspots
Police have recently arrested several cyber criminals in a specific region, indicating that certain areas have become hotspots for cybercrime. Mewat region is one such hotspot indicating a growing trend of cybercrime operating from this area. The Mewat gang's modus operandi is quite different; Cybercriminals in Mewat scam mobile owners just using smartphones and SIM cards without kingpins and targeting mobile owners. The scammers also lure people through online marketplaces such as OLX, in which they pretend to sell possessions and then either physically lure victims to pick-up locations or scam them virtually.
A study conducted by Future Crime Research Foundation and IIT Kanpur in 2023 has revealed that Jamatara city, once considered the cyber crime capital of India, is no longer the epicentre. The study found that 35 hotspots in India are actively involved in cybercrime activities. The top 10 cybercrime hotspots in India collectively account for 80% of cybercrime-related cases in India. These districts are strategically located near India's capital or closer to the National Capital Region (NCR). These districts are strategically placed with multiple borders, making them easy targets for criminals.
Online financial fraud and social media-related crimes are the most common in India. Cybercriminals exploit data as a gold mine, using it to commit crimes. For instance, they can obtain banking and insurance data, use simple AI tools to cheat victims, and they can easily impersonate identities to lure innocent people. In cybercrime hotspots, sextortion is a modern way for cybercriminals to record and demand money. Loan app fraud, OLX fraud, and job fraud also originate from these specific regions.
Recommendations
To counter the challenges posed by emerging cybercrime hubs, the following recommendations are to be considered:
- Advanced threat Intelligence: The digital landscape is evolving, and the threat landscape is becoming more complex. AI's role in cybersecurity is becoming increasingly critical, both positively and negatively, as it helps in understanding and addressing advanced threats. AI is capable of proactive threat hunting, real-time anomaly detection, and swift incident response.
- Enhancing capabilities of Law Enforcement Agencies: Law enforcement agencies must be sensitised to advanced tools or techniques to investigate cyber crime cases effectively. The development and implementation of advanced forensic tools and technologies need to be utilised or implemented to keep up with the evolving tactics of cybercrime perpetrators.
- Continuous Monitoring: Continuous cybersecurity monitoring is crucial for detecting anomalies and preventing cyber-attacks. It involves analysing systems and data to establish baseline security, identify deviations, and investigate potential threats. Cybersecurity experts use data observability tools, artificial intelligence, and machine learning to detect unexpected dataset changes.
- Cyber Security Awareness: Public awareness needs to be higher. Cybercrime prevention and cybersecurity is a shared responsibility of all of us by being aware of the threats and following the best practices. The frequent interaction between law enforcement and the public is necessary to raise awareness about safeguarding personal and financial information. Effective campaigns on cyber security are necessary to educate netizens.
Safety Tips for Netizens
Install up-to-date security software and firewalls on devices, use strong passwords for accounts, and regularly update software and applications. Be cautious when clicking on links or downloading files from unknown sources, and be cautious of your personal information.
Conclusion
The rise of Cyber Crime Hotspots in specific regions or districts has significantly exacerbated the issue of increasing cybercrime rates. In order to combat cybercrime more effectively, it is necessary for law enforcement agencies to strengthen their coordination between different states and to adapt advanced technology methods to counter cybercrime threats effectively. Moreover, educating netizens about cyber crime threats and providing best practices is an effective method to counter these threats, considered the first line of defense against cybercrime.
References
- https://ncrb.gov.in/uploads/nationalcrimerecordsbureau/custom/1701607577CrimeinIndia2022Book1.pdf
- https://economictimes.indiatimes.com/tech/technology/no-kingpins-just-a-smartphone-and-sim-card-how-cybercriminals-in-mewat-scam-mobile-owners/articleshow/98062889.cms?from=mdr
- https://www.futurecrime.org/fcrf-cyber-crime-survey-2023
- https://timesofindia.indiatimes.com/city/mumbai/jamtara-loses-crown-as-new-remote-districts-rewrite-indias-cybercrime-map/articleshow/104475868.cms?from=mdr
- https://government.economictimes.indiatimes.com/news/secure-india/80-of-cyber-crimes-from-10-new-districts-iit-report/103921338
- https://www.dw.com/en/how-mewat-became-indias-new-hub-for-cyber-criminals/video-68674527
- https://www.indiatoday.in/from-india-today-magazine/story/into-cybercrime-hotspot-india-mewat-rajasthan-haryana-uttar-pradesh-2381545-2023-05-19
- https://frontline.thehindu.com/the-nation/spotlight-how-nuh-district-in-haryana-became-a-breeding-ground-for-cybercriminals/article67098193.ece
- https://www.opindia.com/2024/04/nuh-mewat-cyber-crime-haryana-police-crackdown/#google_vignette


