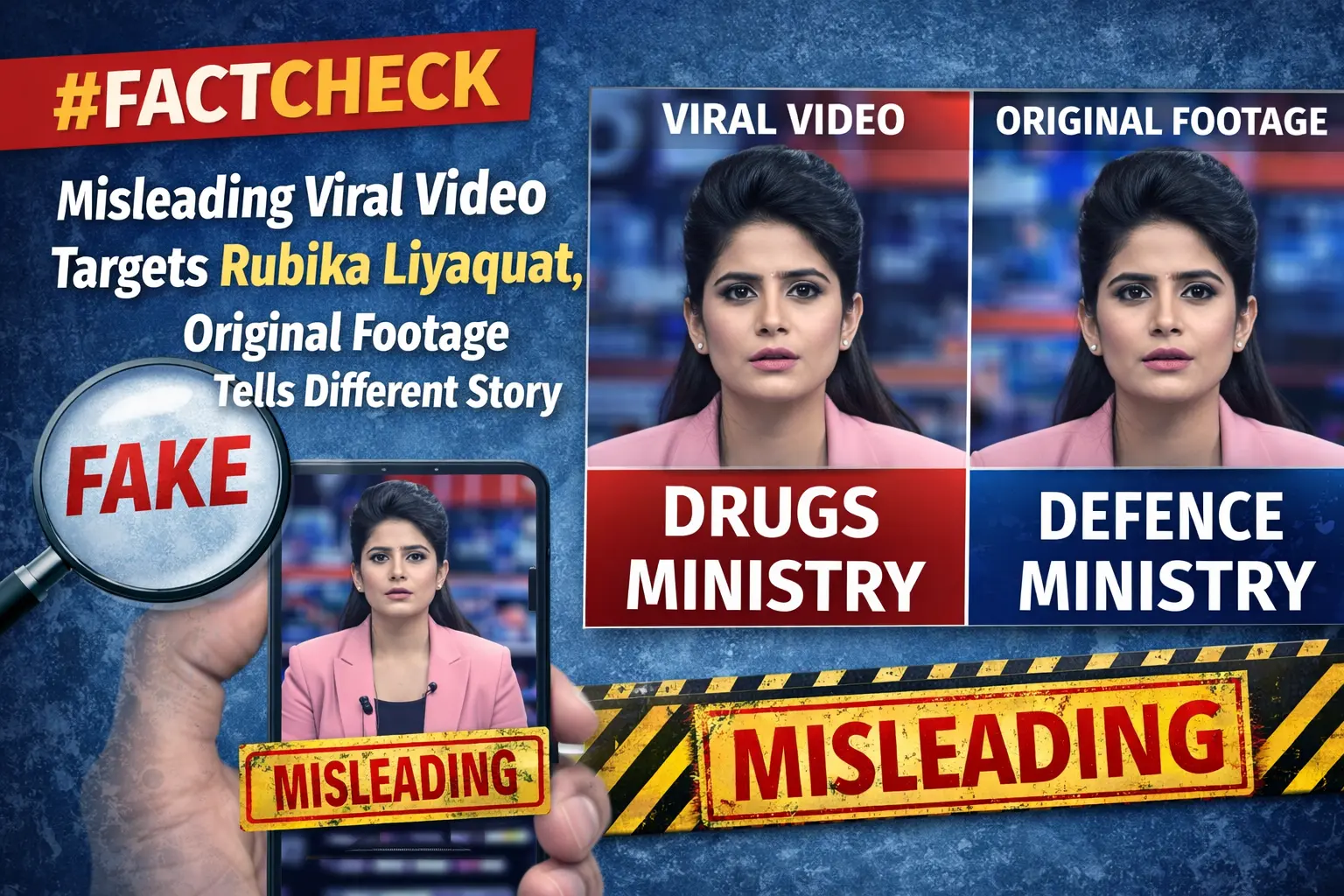
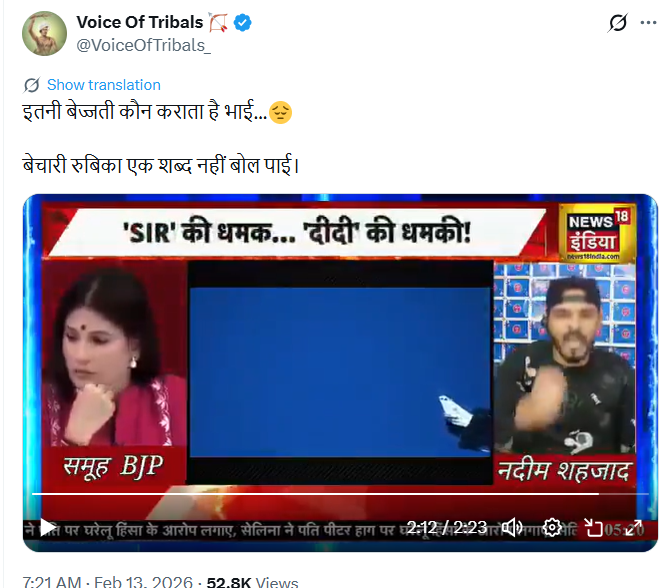
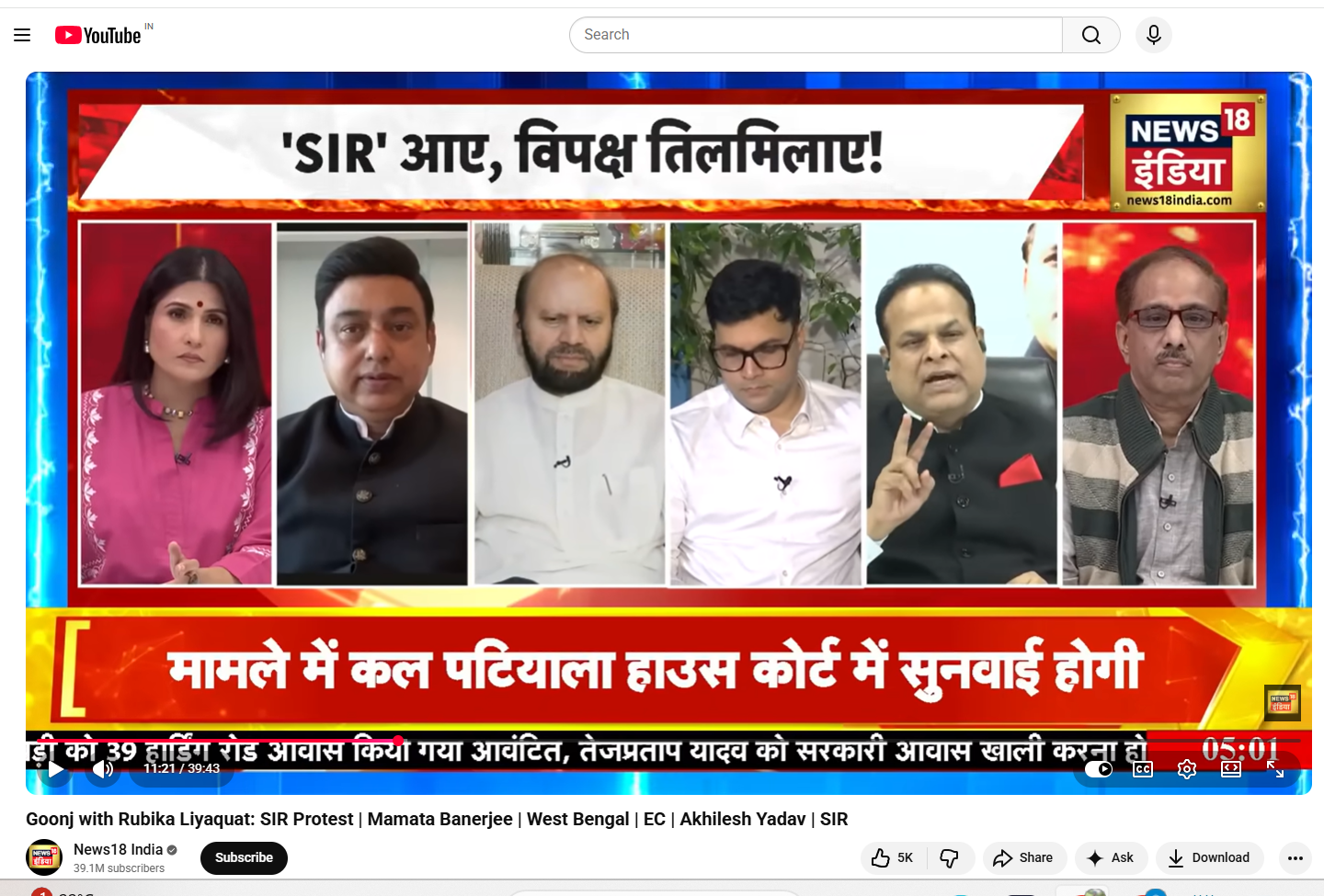
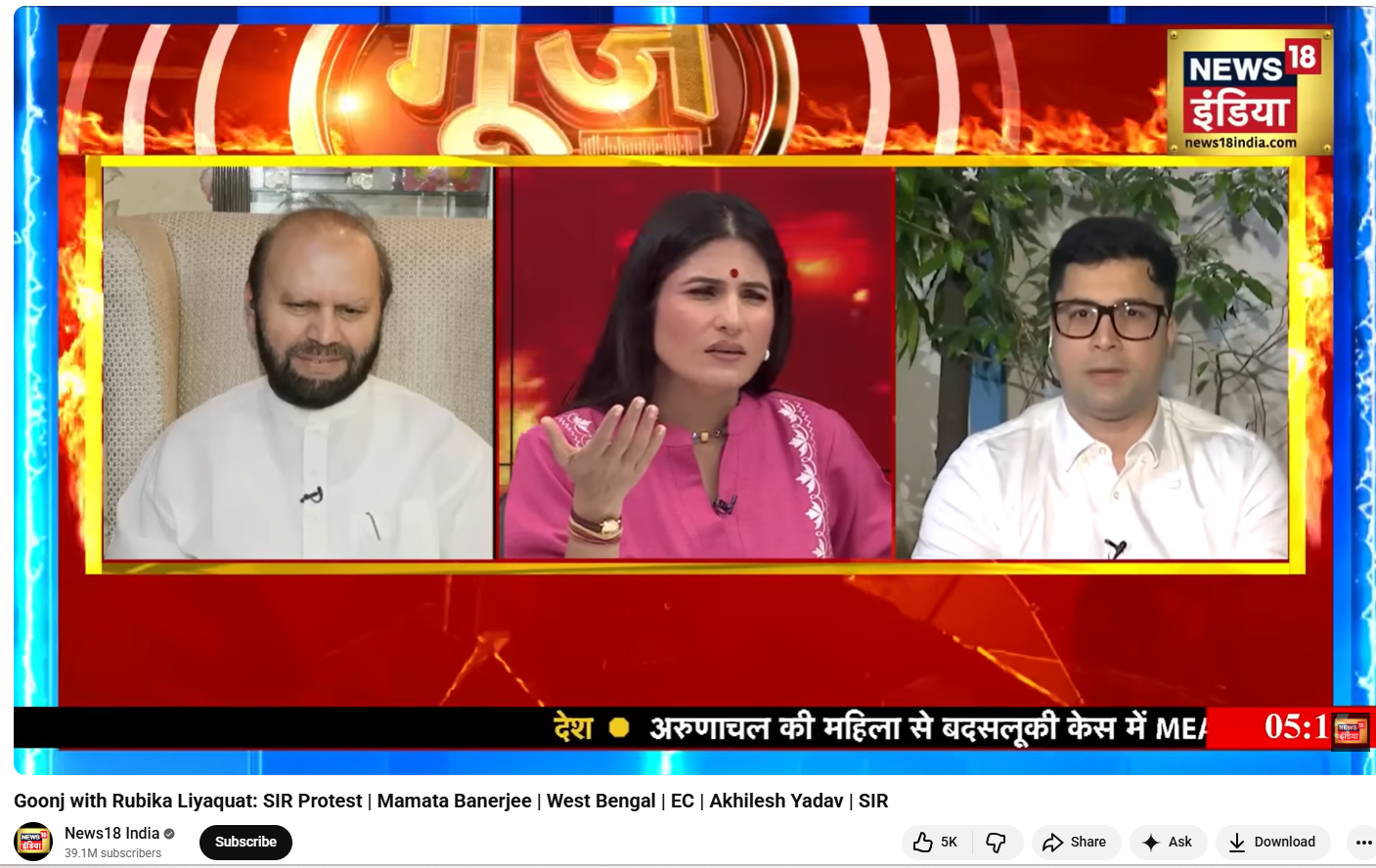
The Enigma of StripedFly Malware
In the tapestry of our modern digital ecosystem, a silent, pervasive conflict simmers beneath the surface, where the quest for cyber resilience seems Sisyphean at times. It is in this interconnected cyber dance that the obscure orchestrator, StripedFly, emerges as the maestro of stealth and disruption, spinning a complex, mostly unseen web of digital discord. StripedFly is not some abstract concept; it represents a continual battle against the invisible forces that threaten the sanctity of our digital domain.
This saga of StripedFly is not a tale of mere coincidence or fleeting concern. It is emblematic of a fundamental struggle that defines the era of interconnected technology—a struggle that is both unyielding and unforgiving in its scope. Over the past half-decade, StripedFly has slithered its way into over a million devices, creating a clandestine symphony of cybersecurity breaches, data theft, and unintentional complicity in its agenda. Let's delve deep into this grand odyssey to unravel the odious intricacies of StripedFly and assess the reverberations felt across our collective pursuit of cyber harmony.
The StripedFly malware represents the epitome of a digital chameleon, a master of cyber camouflage, masquerading as a mundane cryptocurrency miner while quietly plotting the grand symphony of digital bedlam. Its deceptive sophistication has effortlessly skirted around the conventional tripwires laid by our cybersecurity guardians for years. The Russian cybersecurity giant Kaspersky's encounter with StripedFly in 2017 brought this ghostly figure into the spotlight—hitherto, a phantom whistling past the digital graveyard of past threats.
How Does it work
Distinctive in its composition, StripedFly conceals within its modular framework the potential for vast infiltration—an exploitation toolkit designed to puncture the fortifications of both Linux and Windows systems. In an emboldened maneuver, it utilizes a customized version of the EternalBlue SMBv1 exploit—a technique notoriously linked to the enigmatic Equation Group. Through such nefarious channels, StripedFly not only deploys its malicious code but also tenaciously downloads binary files and executes PowerShell scripts with a sinister adeptness unbeknownst to its victims.
Despite its insidious nature, perhaps its most diabolical trait lies in its array of plugin-like functions. It's capable of exfiltrating sensitive information, erasing its tracks, and uninstalling itself with almost supernatural alacrity, leaving behind a vacuous space where once tangible evidence of its existence resided.
In the intricate chess game of cyber threats, StripedFly plays the long game, prioritizing persistence over temporary havoc. Its tactics are calculated—the meticulous disabling of SMBv1 on compromised hosts, the insidious utilization of pilfered keys to propagate itself across networks via SMB and SSH protocols, and the creation of task scheduler entries on Windows systems or employing various methods to assert its nefarious influence within Linux environments.
The Enigma around the Malware
This dualistic entity couples its espionage with monetary gain, downloading a Monero cryptocurrency miner and utilizing the shadowy veils of DNS over HTTPS (DoH) to camouflage its command and control pool servers. This intricate masquerade serves as a cunning, albeit elaborate, smokescreen, lulling security mechanisms into complacency and blind spots.
StripedFly goes above and beyond in its quest to minimize its digital footprint. Not only does it store its components as encrypted data on code repository platforms, deftly dispersed among the likes of Bitbucket, GitHub, and GitLab, but it also harbors a bespoke, efficient TOR client to communicate with its cloistered C2 server out of sight and reach in the labyrinthine depths of the TOR network.
One might speculate on the genesis of this advanced persistent threat—its nuanced approach to invasion, its parallels to EternalBlue, and the artistic flare that permeates its coding style suggest a sophisticated architect. Indeed, the suggestion of an APT actor at the helm of StripedFly invites a cascade of questions concerning the ultimate objectives of such a refined, enduring campaign.
How to deal with it
To those who stand guard in our ever-shifting cyber landscape, the narrative of StripedFly is a clarion call. StObjective reminders of the trench warfare we engage in to preserve the oasis of digital peace within a desert of relentless threats. The StripedFly chronicle stands as a persistent, looming testament to the necessity for heeding the sirens of vigilance and precaution in cyber practice.
Reaffirmation is essential in our quest to demystify the shadows cast by StripedFly, as it punctuates the critical mission to nurture a more impregnable digital habitat. Awareness and dedication propel us forward—the acquisition of knowledge regarding emerging threats, the diligent updating and patching of our systems, and the fortification of robust, multilayered defenses are keystones in our architecture of cyber defense. Together, in concert and collaboration, we stand a better chance of shielding our digital frontier from the dim recesses where threats like StripedFly lurk, patiently awaiting their moment to strike.
References:
https://thehackernews.com/2023/11/stripedfly-malware-operated-unnoticed.html?m=1