#FactCheck - AI-Generated Video Falsely Linked to Protests in Iran
Amid protests against rising inflation in Iran, a video is being widely shared on social media showing people gathering on streets at night while using mobile phone flashlights. The video is being circulated with the claim that it shows recent protests in Iran. Cyber Peace Foundation’s research found that the video being shared as visuals from the ongoing protests in Iran is not real. Our investigation revealed that the viral video is AI-generated and has no connection with actual events on the ground.
Claim
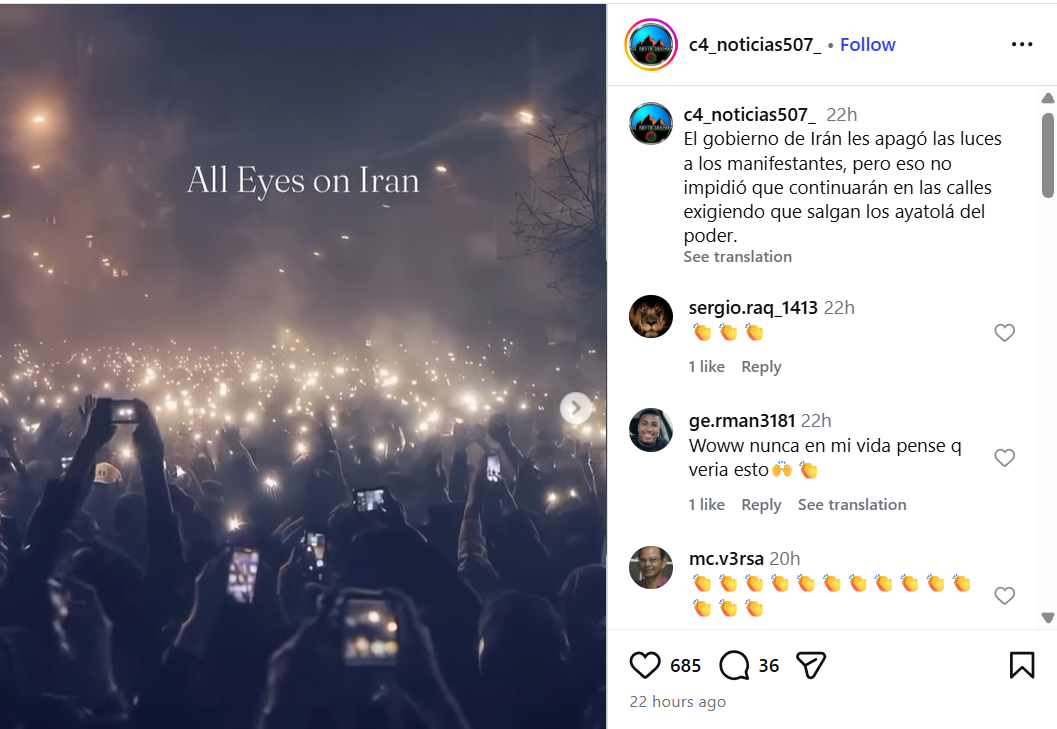
On January 11, 2026, an Instagram user shared the video with a caption written in Spanish. The Hindi translation of the caption reads: “The Iranian government shut down the lights of protesters, but that did not stop them from remaining on the streets demanding that the Ayatollahs step down from power.”The post link, its archived version, and screenshots can be seen below: https://www.instagram.com/p/DTXqzayjqFz/
FactCheck:
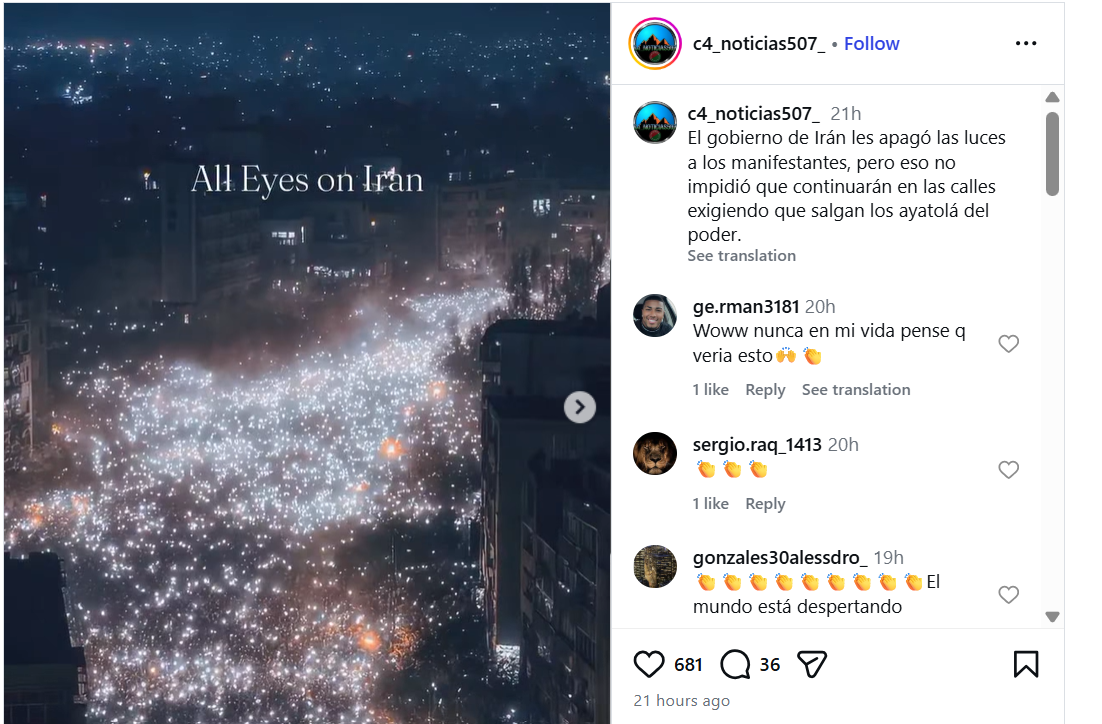
To verify the claim, we extracted keyframes from the viral video and conducted a Google reverse image search.During this process, we found the same video uploaded on Instagram on January 11, 2026. In that post, the user explicitly stated that the video was created using AI. The caption reads that the streetlights were turned off to hide the scale of protesters, but people used their phone lights to show their presence, adding:
“I created this video using AI, inspired by tonight’s protests (January 10, 2026) in Tehran, Iran.” Link to the post and screenshot can be seen below: https://www.instagram.com/p/DTWXsHajNvl/
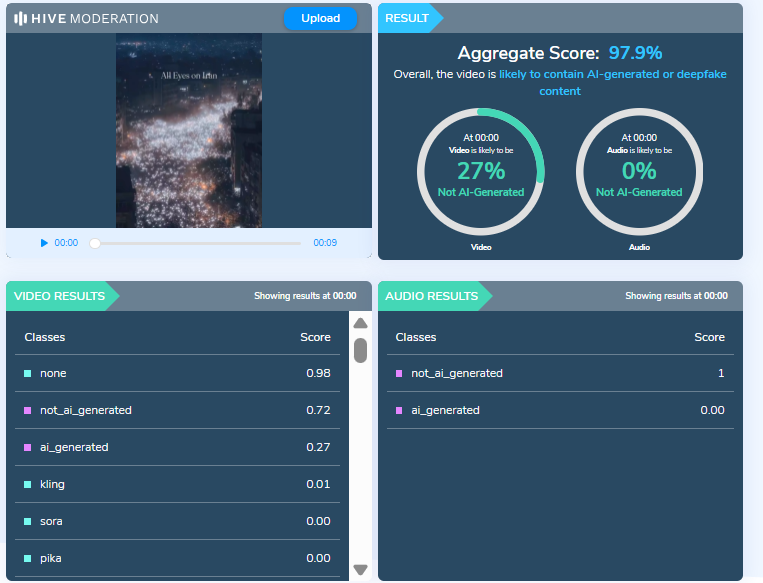
To further verify the authenticity of the video, we scanned it using multiple AI detection tools.Hive Moderation flagged the video as 97 percent AI-generated.
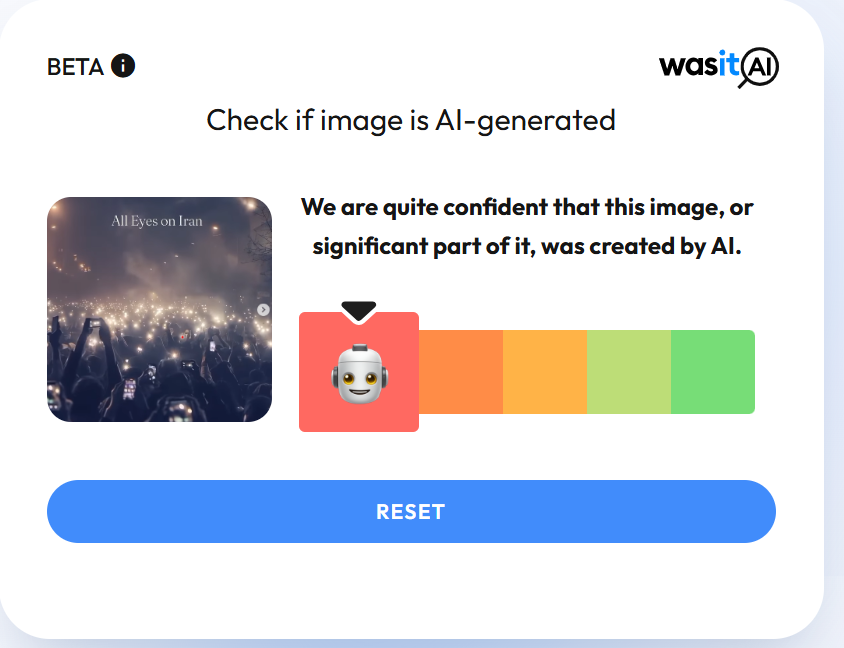
We also scanned the video using another AI detection tool, Wasitai, which likewise identified the video as AI-generated.
Conclusion
Our investigation confirms that the video being shared as footage from protests in Iran is not real. The viral video has been created using artificial intelligence and is being falsely linked to the ongoing protests. The claim circulating on social media is false and misleading.
Related Blogs

Introduction
Indian Cybercrime Coordination Centre (I4C) was established by the Ministry of Home Affairs (MHA) to provide a framework and eco-system for law enforcement agencies (LEAs) to deal with cybercrime in a coordinated and comprehensive manner. The Indian Ministry of Home Affairs approved a scheme for the establishment of the Indian Cyber Crime Coordination Centre (I4C) in October2018, which was inaugurated by Home Minister Amit Shah in January 2020. I4C is envisaged to act as the nodal point to curb Cybercrime in the country. Recently, on 13th March2024, the Centre designated the Indian Cyber Crime Coordination Centre (I4C) as an agency of the Ministry of Home Affairs (MHA) to perform the functions under the Information Technology Act, 2000, to inform about unlawful cyber activities.
The gazetted notification dated 13th March 2024 read as follows:
“In exercise of the powers conferred by clause (b) of sub-section (3) of section 79 of the Information Technology Act 2000, Central Government being the appropriate government hereby designate the Indian Cybercrime Coordination Centre (I4C), to be the agency of the Ministry of Home Affairs to perform the functions under clause (b) of sub-section (3) of section79 of Information Technology Act, 2000 and to notify the instances of information, data or communication link residing in or connected to a computer resource controlled by the intermediary being used to commit the unlawful act.”
Impact
Now, the Indian Cyber Crime Coordination Centre (I4C) is empowered to issue direct takedown orders under 79(b)(3) of the IT Act, 2000. Any information, data or communication link residing in or connected to a computer resource controlled by any intermediary being used to commit unlawful acts can be notified by the I4C to the intermediary. If an intermediary fails to expeditiously remove or disable access to a material after being notified, it will no longer be eligible for protection under Section 79 of the IT Act, 2000.
Safe Harbour Provision
Section79 of the IT Act also serves as a safe harbour provision for the Intermediaries. The safe harbour provision under Section 79 of the IT Act states that "an intermediary shall not be liable for any third-party information, data, or communication link made available or hosted by him". However, it is notable that this legal immunity cannot be granted if the intermediary "fails to expeditiously" take down a post or remove a particular content after the government or its agencies flag that the information is being used to commit something unlawful. Furthermore, Intermediaries are also obliged to perform due diligence on their platforms and comply with the rules & regulations and maintain and promote a safe digital environment on the respective platforms.
Under the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, The government has also mandated that a ‘significant social media intermediary’ must appoint a Chief Compliance Officer (CCO), Resident Grievance Officer (RGO), and Nodal Contact Person and publish periodic compliance report every month mentioning the details of complaints received and action taken thereon.
I4C's Role in Safeguarding Cyberspace
The Indian Cyber Crime Coordination Centre (I4C) is actively working towards initiatives to combat the emerging threats in cyberspace. I4C is one of the crucial extensions of the Ministry of Home Affairs, Government of India, working extensively to combat cyber crimes and ensure the overall safety of netizens. The ‘National Cyber Crime Reporting Portal’ equipped with a 24x7 helpline number 1930, is one of the key component of the I4C.
Components Of The I4C
- National Cyber Crime Threat Analytics Unit
- National Cyber Crime Reporting Portal
- National Cyber Crime Training Centre
- Cyber Crime Ecosystem Management Unit
- National Cyber Crime Research and Innovation Centre
- National Cyber Crime Forensic Laboratory Ecosystem
- Platform for Joint Cyber Crime Investigation Team.
Conclusion
I4C, through its initiatives and collaborative efforts, plays a pivotal role in safeguarding cyberspace and ensuring the safety of netizens. I4C reinforces India's commitment to combatting cybercrime and promoting a secure digital environment. The recent development by designating the I4C as an agency to notify the instances of unlawful activities in cyberspace serves as a significant step to counter cybercrime and promote an ethical and safe digital environment for netizens.
References
- https://www.deccanherald.com/india/centre-designates-i4c-as-agency-of-mha-to-notify-unlawful-activities-in-cyber-world-2936976
- https://www.business-standard.com/india-news/home-ministry-authorises-i4c-to-issue-takedown-notices-under-it-act-124031500844_1.html
- https://www.hindustantimes.com/india-news/it-ministry-empowers-i4c-to-notify-instances-of-cybercrime-101710443217873.html
- https://i4c.mha.gov.in/about.aspx#:~:text=Objectives%20of%20I4C,identifying%20Cybercrime%20trends%20and%20patterns

Introduction
With the increasing reliance on digital technologies in the banking industry, cyber threats have become a significant concern. Cyberlaw plays a crucial role in safeguarding the banking sector from cybercrimes and ensuring the security and integrity of financial systems.
The banking industry has witnessed a rapid digital transformation, enabling convenient services and greater access to financial resources. However, this digitalisation also exposes the industry to cyber threats, necessitating the formulation and implementation of effective cyber law frameworks.
Recent Trends in the Banking Industry
Digital Transformation: The banking industry has embraced digital technologies, such as mobile banking, internet banking, and financial apps, to enhance customer experience and operational efficiency.
Open Banking: The concept of open banking has gained prominence, enabling data sharing between banks and third-party service providers, which introduces new cyber risks.

How Cyber Law Helps the Banking Sector
The banking sector and cyber crime share an unspoken synergy due to the mass digitisation of banking services. Thanks to QR codes, UPI and online banking payments, India is now home to 40% of global online banking transactions. Some critical aspects of the cyber law and banking sector are as follows:
Data Protection: Cyberlaw mandates banks to implement robust data protection measures, including encryption, access controls, and regular security audits, to safeguard customer data.
Incident Response and Reporting: Cyberlaw requires banks to establish incident response plans, promptly report cyber incidents to regulatory authorities, and cooperate in investigations.
Customer Protection: Cyberlaw enforces regulations related to online banking fraud, identity theft, and unauthorised transactions, ensuring that customers are protected from cybercrimes.
Legal Framework: Cyberlaw provides a legal foundation for digitalisation in the banking sector, assuring customers that regulations protect their digital transactions and data.
Cybersecurity Training and Awareness: Cyberlaw encourages banks to conduct regular training programs and create awareness among employees and customers about cyber threats, safe digital practices, and reporting procedures.

RBI Guidelines
The RBI, as India’s central banking institution, has issued comprehensive guidelines to enhance cyber resilience in the banking industry. These guidelines address various aspects, including:
Technology Risk Management
Cyber Security Framework
IT Governance
Cyber Crisis Management Plan
Incident Reporting and Response
Recent Trends in Banking Sector Frauds and the Role of Cyber Law
Phishing Attacks: Cyberlaw helps banks combat phishing attacks by imposing penalties on perpetrators and mandating preventive measures like two-factor authentication.
Insider Threats: Cyberlaw regulations emphasise the need for stringent access controls, employee background checks, and legal consequences for insiders involved in fraudulent activities.
Ransomware Attacks: Cyberlaw frameworks assist banks in dealing with ransomware attacks by enabling legal actions against hackers and promoting preventive measures, such as regular software updates and data backups.
Master Directions on Cyber Resilience and Digital Payment Security Controls for Payment System Operators (PSOs)
Draft of Master Directions on Cyber Resilience and Digital Payment Security Controls for Payment System Operators (PSOs) issued by the Reserve Bank of India (RBI). The directions provide guidelines and requirements for PSOs to improve the safety and security of their payment systems, with a focus on cyber resilience. These guidelines for PSOs include mobile payment service providers like Paytm or digital wallet payment platforms.
Here are the highlights-
The Directions aim to improve the safety and security of payment systems operated by PSOs by providing a framework for overall information security preparedness, with an emphasis on cyber resilience.
The Directions apply to all authorised non-bank PSOs.
PSOs must ensure adherence to these Directions by unregulated entities in their digital payments ecosystem, such as payment gateways, third-party service providers, vendors, and merchants.
The PSO’s Board of Directors is responsible for ensuring adequate oversight over information security risks, including cyber risk and cyber resilience. A sub-committee of the Board may be delegated with primary oversight responsibilities.
PSOs must formulate a Board-approved Information Security (IS) policy that covers roles and responsibilities, measures to identify and manage cyber security risks, training and awareness programs, and more.
PSOs should have a distinct Board-approved Cyber Crisis Management Plan (CCMP) to detect, contain, respond, and recover from cyber threats and attacks.
A senior-level executive, such as a Chief Information Security Officer (CISO), should be responsible for implementing the IS policy and the cyber resilience framework and assessing the overall information security posture of the PSO.
PSOs need to define Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs) to identify potential risk events and assess the effectiveness of security controls. The sub-committee of the Board is responsible for monitoring these indicators.
PSOs should conduct a cyber risk assessment when launching new products, services, technologies, or significant changes to existing infrastructure or processes.
PSOs, including inventory management, identity and access management, network security, application security life cycle, security testing, vendor risk management, data security, patch and change management life cycle, incident response, business continuity planning, API security, employee awareness and training, and other security measures should implement various baseline information security measures and controls.
PSOs should ensure that payment transactions involving debit to accounts conducted electronically are permitted only through multi-factor authentication, except where explicitly permitted/relaxed.

Conclusion
The relationship between cyber law and the banking industry is crucial in ensuring a secure and trusted digital environment. Recent trends indicate that cyber threats are evolving and becoming more sophisticated. Compliance with cyber law provisions and adherence to guidelines such as those provided by the RBI is essential for banks to protect themselves and their customers from cybercrimes. By embracing robust cyber law frameworks, the banking industry can foster a resilient ecosystem that enables innovation while safeguarding the interests of all stakeholders or users.

Introduction
Targeting airlines and airports, airline hoax threats are fabricated alarms which intend to disrupt normal day-to-day activities and create panic among the public. Security of public settings is of utmost importance, making them a vulnerable target. The consequences of such threats include the financial loss incurred by parties concerned, increased security protocols to be followed immediately after and in preparation, flight delays and diversions, emergency landings and passenger inconvenience and emotional distress. The motivation behind such threats is malicious intent of varying degrees, breaching national security, integrity and safety. However, apart from the government, airline and social media authorities which already have certain measures in place to tackle such issues, the public, through responsible consumption and verified sharing has an equal role in preventing the spread of misinformation and panic regarding the same.
Hoax Airline Threats
The recent spate of bomb hoax threats to Indian airlines has witnessed false reports about threats to (over) 500 flights since 14/10/2024, the majority being traced to posts on social media handles which are either anonymous or unverified. Some recent incidents include a hoax threat on Air India's flights from Delhi to Mumbai via Indore which was posted on X, 30/10/2024 and a flight from Nepal (Kathmandu) to Delhi on November 2nd, 2024.
As per reports by the Indian Express, steps are being taken to address such incidents by tweaking the assessment criteria for threats (regarding bombs) and authorities such as the Bomb Threat Assessment Committees (BTAC) are being selective in categorising them as specific and non-specific. Some other consideration factors include whether a VIP is onboard and whether the threat has been posted from an anonymous account with a similar history.
CyberPeace Recommendations
- For Public
- Question sensational information: The public should scrutinise the information they’re consuming not only to keep themselves safe but also to be responsible to other citizens. Exercise caution before sharing alarming messages, posts and pieces of information
- Recognising credible sources: Rely only on trustworthy, verified sources when sharing information, especially when it comes to topics as serious as airline safety.
- Avoiding Reactionary Sharing: Sharing in a state of panic can contribute to the chaos created upon receiving unverified news, hence, it is suggested to refrain from reactionary sharing.
- For the Authorities & Agencies
- After a series of hoax bomb threats, the Government of India has issued an advisory to social media platforms calling for them to make efforts for the removal of such malicious content. Adherence to obligations such as the prompt removal of harmful content or disabling access to such unlawful information has been specified under the IT Rules, 2021. They are also obligated under the Bhartiya Nagarik Suraksha Sanhita 2023 to report certain offences on their platform. The Ministry of Civil Aviation’s action plan consists of plans regarding hoax bomb threats being labelled as a cognisable offence, and attracting a no-flyers list as a penalty, among other things.
These plans also include steps such as :
- Introduction of other corrective measures that are to be taken against bad actors (similar to having a non-flyers list).
- Introduction of a reporting mechanism which is specific to such threats.
- Focus on promoting awareness, digital literacy and critical thinking, fact-checking resources as well as encouraging the public to report such hoaxes
Conclusion
Preventing the spread of airline threat hoaxes is a collective responsibility which involves public engagement and ownership to strengthen safety measures and build upon the trust in the overall safety ecosystem (here; airline agencies, government authorities and the public). As the government and agencies take measures to prevent such instances, the public should continue to share information only from and on verified and trusted portals. It is encouraged that the public must remain vigilant and responsible while consuming and sharing information.
References
- https://indianexpress.com/article/business/flight-bomb-threats-assessment-criteria-serious-9646397/
- https://www.wionews.com/world/indian-airline-flight-bound-for-new-delhi-from-nepal-receives-hoax-bomb-threat-amid-rise-in-similar-incidents-772795
- https://www.newindianexpress.com/nation/2024/Oct/26/centre-cautions-social-media-platforms-to-tackle-misinformation-after-hoax-bomb-threat-to-multiple-airlines
- https://economictimes.indiatimes.com/industry/transportation/airlines-/-aviation/amid-rising-hoax-bomb-threats-to-indian-airlines-centre-issues-advisory-to-social-media-companies/articleshow/114624187.cms


