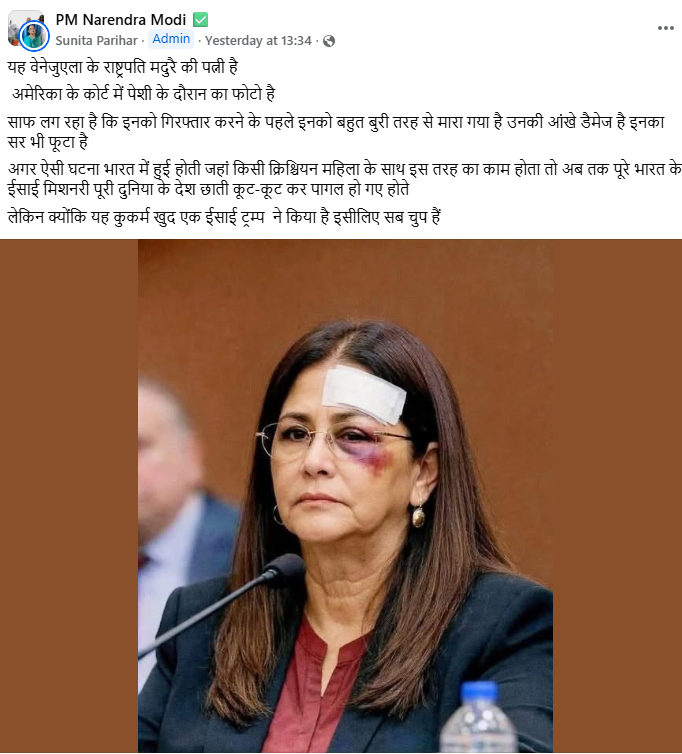
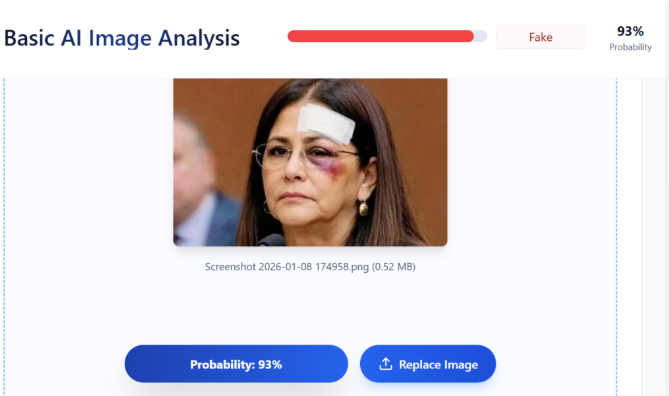
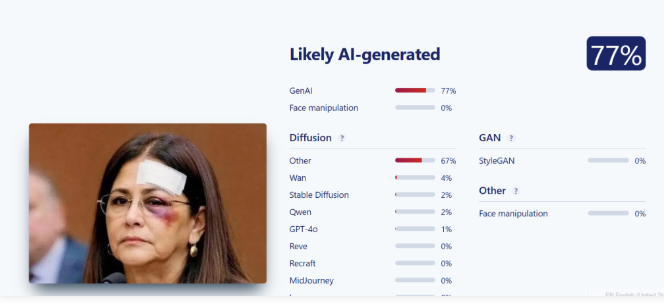
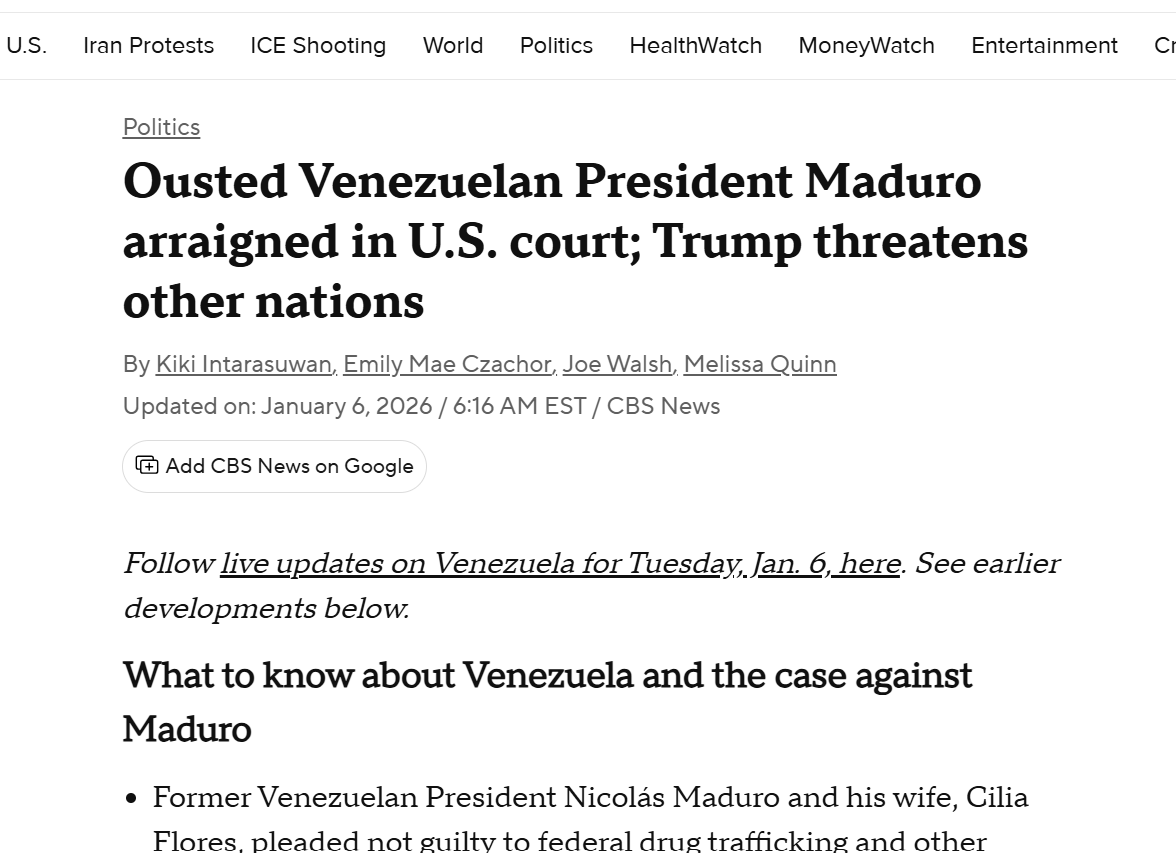
Post Session Report on Universal Acceptance and Multilingual Internet at BIT University under CyberPeace Center of Excellence (CCoE)
11th November 2022 CyberPeace Foundation in association with Universal Acceptance has successfully conducted the workshop on Universal Acceptance and Multilingual Internet for the students and faculties of BIT University under CyberPeace Center of Excellence (CCoE).
CyberPeace Foundation has always been engaged towards the aim of spreading awareness regarding the various developments, avenues, opportunities and threats regarding cyberspace. The same has been the keen principle of the CyberPeace Centre of Excellence setup in collaboration with various esteemed educational institutes. We at CyberPeace Foundation would like to take the collaborations and our efforts to a new height of knowledge and awareness by proposing a workshop on UNIVERSAL ACCEPTANCE AND MULTILINGUAL INTERNET. This workshop was instrumental in providing the academia and research community a wholesome outlook towards the multilingual spectrum of internet including Internationalized domain names and email address Internationalization.
Date –11th November 2022
Time – 10:00 AM to 12:00 PM
Duration – 2 hours
Mode - Online
Audience – Academia and Research Community
Participants Joined- 15
Crowd Classification - Engineering students (1st and 4th year, all streams) and Faculties members
Organizer : Mr. Harish Chowdhary : UA Ambassador
Moderator: Ms. Pooja Tomar, Project coordinator cum trainer
Speakers - Mr. Abdalmonem Galila, Abdalmonem: Vice Chair , Universal Acceptance Steering Group (UASG)and
Mr. Mahesh D Kulkarni Director, Evaris Systems and Former Senior Director, CDAC, Government of India,First session was delivered by Mr. Abdalmonem Galila, Abdalmonem: Vice Chair , Universal Acceptance Steering Group (UASG) “Universal Acceptance( UA) and why UA matters?”
- What is universal acceptance?
- UA is cornerstone to a digitally inclusive internet by ensuring all domain names and email addresses in all languages, script and character length.
- Achieving UA ensures that every person has the ability to navigate the internet.
- Different UA issues were also discussed and explained.
- Tagated systems by the UA and implication were discussed in detail.
Second session was delivered by Mr. Mahesh D Kulkarni, ES Director Evaris on the topic of “IDNs in Indian languages perspective- challenges and solutions”.
- The multilingual diversity of India was focused on and its impact.
- Most students were not aware of what Unicode, IDNS is and their usage.
- Students were briefed by giving real time examples on IDN, Domain name implementation using local language.
- In depth knowledge of and practical exposure of Universal Acceptance and Multilingual Internet has been served to the students.
- Tools and Resources for Domain Name and Domain Languages were explained.
- Languages nuances of Multilingual diversity of India explained with real time facts and figures.
- Given the idea of IDN Email,Homograph attack,Homographic variant with proper real time examples.
- Explained about the security threats and IDNA protocols.
- Given the explanation on ABNF.
- Explained the stages of Universal Acceptance.